Art of the Possible in 6G – A View from 6GIC
Ning Wang, Pei Xiao, Mohsen Khalily, Fabien Heliot, Chuang Heng Foh, Yi Ma, Bernard Hunt, Rahim Tafazolli, 6G Innovation Centre (6GIC) University of Surrey
Introduction
Since the initial commercial deployment of 5G in 2019, the research community and industry have already started to outline their future 6G visions especially into the direction of blending the physical and the virtual worlds in the digitised society. While 5G will continue to evolve in the near future, there are also brand new technical challenges that will be mainly tackled in the context of 6G, e.g. ambient sensing, precision localisation and synchronisation, and manipulation of the radio propagation environment. In this article we highlight our 6G vision and some selected 6G-oriented research activities carried out at the 6G Innovation Centre (6GIC) of the University of Surrey. 6GIC will be a key UK-based hub for global innovation and collaboration on 6G wireless, involving governments, regulators, mobile operators, vendors, enterprises, and leading research and development centres, as 5GIC was for 5G innovation at the University. In this article we first outline some key features of our top-level 6G vision before diving into specific topics where a number of selected research items investigated at 6GIC are introduced.
1. Our 6G vision
We have already started to witness the potential for huge social-economic impacts from 5G, due to the cutting-edge technologies enabling new digital applications across a wide range of vertical industrial sectors. In the 6G era, as shown in Figure 1, we can further anticipate an even richer fabric of digital services, including extending human senses and ambient data blending the virtual and physical worlds. We can imagine a world where one can interact with colleagues, friends/ families and doctors from different continents, from different cultures, without any perception of not being in a common physical space with natural interactions with ambient information including all human senses. In addition, 6G is expected to have a game-changing impact on specific vertical sectors especially those involving ultra-precision control operations at large scale. In particular, we would like to emphasise the importance of ultra-precision geolocation, sensing and synchronisation capabilities in 6G in support of natural interactions as well as future mission-critical applications, some of which might not yet have been envisaged.
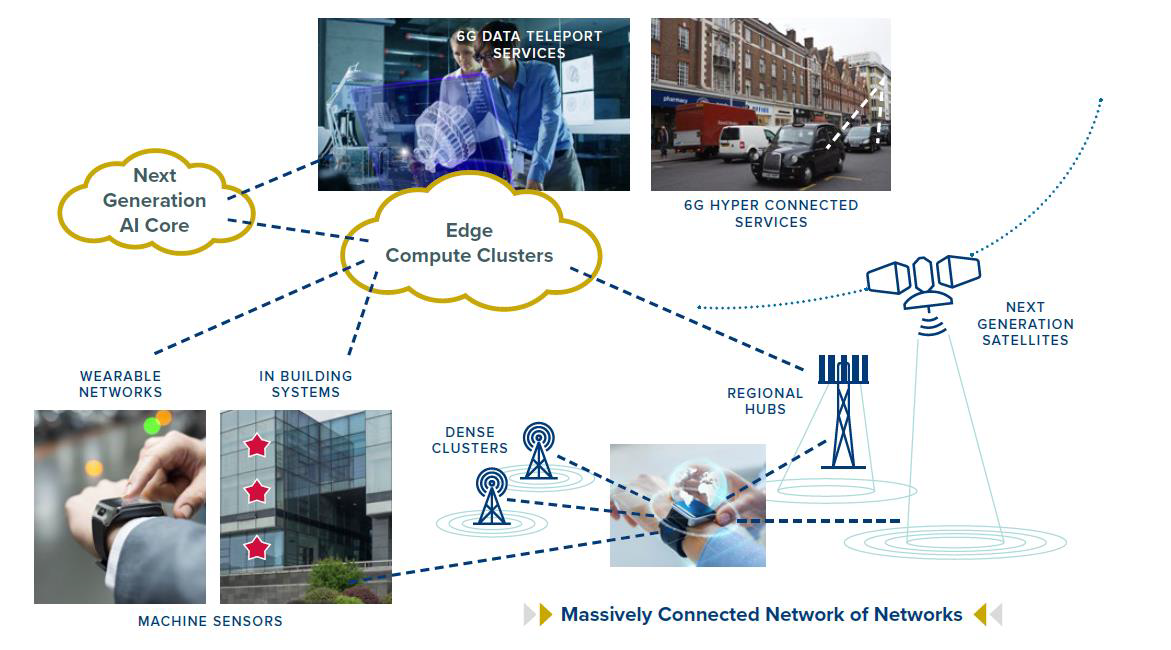
Figure 1. Our 6G vision on next generation of AI, network of networks and capabilities
It is presently difficult to predict whether the future 6G network architecture will follow a revolutionary or evolutionary pathway or a mixture of both. However, it is clear that 6G will witness the journey of network convergence as well as openness. Different types of networks bring different capabilities into the whole system: wearable and short range networks for acquisition and processing of ambient intelligence; wide area and cellular networks for mobility and capacity; and non-terrestrial networks for ubiquitous coverage and availability. It is worth mentioning that the traditional view of “network of networks” will advance into “network of capabilities” and “network of intelligence” giving that a wider variety of communication, cloud/edge computing, data storage, precise sensing/ location and software-based network functions can be integral parts of 6G supply chains. The 6G ecosystem will have the feature of deep and seamless level of capability integration, so that end users will appreciate easy and unified access to any capabilities anytime and anywhere. Ambient information and intelligence will be ubiquitous and their integration into communication infrastructure lead to smarter and energy efficient communications. We can envisage the concept of 6G consortium where stakeholders with heterogeneous capabilities can flexibly constitute a 6G system, either on a long-term basis or even on-demand. The current Open RAN concept will be naturally extended toward further openness of additional 6G components through de-aggregation of functionalities.
As far as the wireless technology is concerned, it is imperative to go beyond the ideas developed in 5G, considering the use of high definition and integrated sensing for ambient intelligence, new radio bands including THz frequencies for capacity, emerging technologies such as distributed MIMO and so-called “cell-free” concepts for resource-aware RAN architectures, and integrated satellite and terrestrial networks to support pervasive coverage. Meanwhile, materials science can enable new forms of antennas and wireless communication, including Reconfigurable Intelligent Surfaces (RIS), as well as massive and distributed antenna systems and architectures.
The full version of our 6G vision, developed in conjunction with major 6GIC industrial partners, can be found in our white paper [1].
2. 6G-related research topics
We now introduce specific dimensions of 6G-related technical challenges, as well as selected ongoing works carried out at 6GIC.
6G applications and requirements
Evolved from the 5G-oriented VR/AR, it is expected that fully immersive extended reality (XR) services such as holographic teleportation will become a killer application of 6G. We can deem teleportation as the next generation of Zoom where end users may communicate and interact with remote entities (people or objects) in a truly immersive manner, through a wide variety of human senses. The gap analysis on future network support for such applications has been investigated in the ITU Network 2030 Initiative [2] where the University of Surrey has been actively involved.

Figure 2. Real-time teleportation to human-size holographic display
Figure 2 provides a snapshot of teleportation to a holographic display. Depending on the video resolution level the data rate can be at the order of tens of Gbps according to our measurement. In addition to the ultra-high end-to-end data rate requirement for such fully immersive applications, we also envisage other technical challenges on the processing of ultra-high volume of content data at the mobile edge (e.g. remote production), as well as stringently in-time and synchronised delivery of multi-source teleportation content to end users. This is an ideal application scenario that illustrates the necessity of high-performance not only from the communication side but also (edge) computing features in future networks like 6G.
6G network architectures
Empowered by emerging technologies such as softwarisation, edge computing and network function virtualisation (NFV), 5G has become a much more open and flexible network platform capable of autonomously supporting a wider range of vertical applications compared to its predecessors. On the other hand, we still have the “fences”, in terms of necessary interfaces and gateways etc., between 5G and the outside world, known as “non-3GPP” networks, including fixed Internet, WiFi, satellite networks and cloud/fog infrastructures. One daring 6G vision is of a borderless ecosystem consisting of natively integrated capabilities contributed from heterogeneous communication, computing, storage, or even (AI-based) knowledge resources. The implication to the evolved business model is the creation of open opportunities for all types of stakeholders to be an integral part of 6G supply chains.
Specific to the integration of space networks and future 6G, we envisage satellite network segment to be a native component of the 6G ecosystem, offering not only backhaul functionalities but also direct user equipment access services. In particular, Low Earth Orbit (LEO) satellite systems will play an essential role thanks to the relatively low network latencies. Direct user equipment (UE) access to the satellite without the support of ground stations will be a key feature in 6G, allowing end users to access services even at rural areas conveniently. Meanwhile, the mega-constellation behaviours of LEO satellites will pose new research issues in terms of topology dynamicity, routing stability and optimality, as well as service continuity to end users. Similar to its terrestrial counterpart, we also look at the possibility of software defined space networks in 6G, allowing fully programmable traffic steering and service delivery tailored for specific application requirements and business policies.
6G Wireless Technologies, Reconfigurable Intelligent Surface (RIS)
An RIS is a reflecting surface capable of directing electromagnetic waves to the direction of interest as shown in Figure 3. Similar to the holographic metasurface concept [6], an RIS synthetises a radiation pattern of interest in a holographic manner [7]. The role of the RIS is to modulate the incident wave on the aperture into a desired aperture field that radiates the radiation pattern of interest. This is achieved by altering the phase of the incident wave with the phase response of each unit cell across the RIS upon reflection. As a result, an RIS can reconfigure the desired radiation pattern in an intelligent and automated manner and eliminate the need for mechanical scanning.
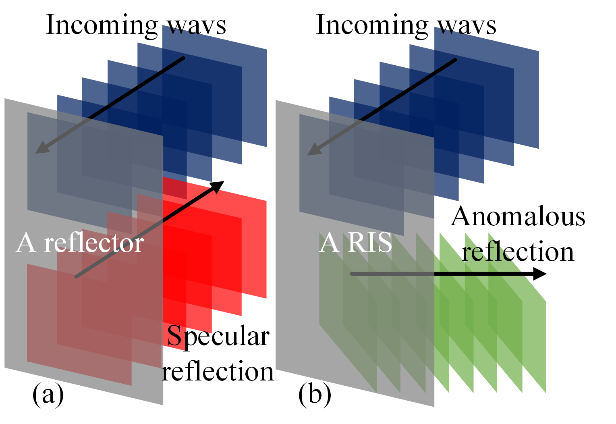
Figure 3. The mechanism of wave reflection in an RIS-enhanced environment, (a) specular reflection from a conventional reflector; (b) engineered reflection from an RIS to the desired angle.
6G networks require much higher data rate with robust and meaningful coverage. Network operators can employ THz bands to meet those requirements. However, the path loss will be dramatically increased for THz communications. As such, coverage would certainly be shrunk and remedial actions must be taken to compensate the loss. RIS will play a pivotal role in this regard where the sporadic waves in an environment can be purposefully recycled and redirected to the network’s blind spots.
The design procedure of an RIS is directly linked to the geographical properties of the region where it is going to be deployed. The location of base stations (BSs) and the direction of reflected waves will have a direct influence on the constructed pattern of unit cells within the RIS structure. Consequently, the design of an RIS should be customised for each case, which is in contradiction with mass production. One solution to sort this issue out is to equip the RIS with controlling components such as Varactor of PIN diodes to dynamically change the macroscopic response of the RIS without changing its physics. Two types of RISs have been prototyped at 6GIC, as shown in Fig. 4. The structure on the left side of Fig. is capable of dynamically changing the reflected beam, thus suita4ble to be employed in urban areas wherever beam scanning is required. Whereas, the one on the right side of Fig. 4 has fixed engineered reflected beam directions but needs no electrical power and works as a stand-alone equipment. It is thus useful either when the direction of the reflected beam does not need to be changed or the provisioning of electrical power is challenging for network operators.

Figure 4. The world’s first RIS demo at 6GIC. The left-side one can dynamically change the beam while the one on right has fixed reflected beam with no need of electrical power.
A video of the RIS demo can be found at https://www.youtube.com/watch?v=PoLEWaDg8f4
At 6GIC, we are also studying the fundamental limits of RIS-aided multi-input multi-output (MIMO), a.k.a. MIMO-RIS, communication systems, starting from simple scenarios, e.g. point-to-point, before tackling more advanced ones, e.g. multi-user distributed MIMO/cell-free. So far, we have derived both the capacity and fundamental energy efficiency (EE)-spectral efficiency (SE) trade-off expressions for point-to-point MIMO-RIS systems. These expressions have helped us to better understand the benefit of MIMO-RIS in comparison with other MIMO based systems, e.g. classic MIMO systems, MIMO relay-based systems. Our performance analysis shows that MIMO-RIS is more spectrally efficient than both MIMO-relay and MIMO (i.e. 60% and 15% more efficient, respectively) and at least three times more energy efficient than MIMO in a point-to-point communication scenario.
We have also explored different scenarios and use cases of RIS, e.g., in the areas of security [8], RIS-aided cell-free networks [9] and RIS assisted mobile edge computing [10], etc. Those studies have demonstrated diverse applications of RIS to improve network performance KPIs in terms of spectrum efficiency, energy efficiency, deployment efficiency and secrecy.
THz Communications for 6G:
Even though 5G systems are still being rolled out, it is argued that their rates, in the order of gigabits per second, may fall short at supporting many emerging applications, such as 3D gaming and extended reality. Such applications may require data rates of several hundreds of gigabits to several terabits per second with low latency and high reliability, which may be expected to be requirements of 6G. Given the potential of terahertz (THz) communications systems to provide such data rates over short distances, they are widely regarded to be the next frontier for wireless communications research.
However, the following major technical challenges need to be addressed in order to render THz viable for practical deployments. 1) its short communication range due to high propagation and molecular absorption losses; 2) THz transceiver design: the frequency band of the THz signal is too high for conventional oscillators, while it is too low for optical photon emitters. This problem is known as the THz gap; 3) Antenna and amplifier design for ultra-wideband THz transmissions; 4) THz beam tracking: the main challenge is how to acquire channel state information. It is crucial to accurately measure the angle of departure (AoD) of transmitters and the angle of arrival (AoA) of receivers by using beam tracking techniques.
At 6GIC, we have conducted research on several enabling technologies for THz communications. In [11], we designed a high gain on-chip antenna on silicon technology for sub terahertz applications over a wide-frequency range. An efficient terahertz (THz) photoconductive antenna (PCA) was proposed in [12]. The antenna is designed for continuous wave (CW) applications in the frequency range of 0.5-3 THz. The overall optical-to-THz efficiency of the proposed PCA is improved by enhancing the optical-to-electrical and radiation efficiencies. In [13], a novel terahertz (THz) spectroscopy technique and a new graphene-based sensor were proposed. It is the first THz sensor of its kind. A terahertz sensor structure was proposed in [14] that is capable of sensing any variations in physical properties of materials.
Our next step is to design spectrum and power efficient multi-carrier waveform for THz communication by leveraging visible light communication (VLC) and ultra-wide band (UWB) waveform designs, taking into consideration practical limitations. Based on the literature, the vast majority of experimental transceivers designed for THz band (0.3 to 3 THz) rely on optical communication with intensity modulation (IM)/direct detection (DD) being the common method for transmitting/detecting the waveforms. This makes pulse-based and optical multi-carrier waveform designs very relevant to THz communication. Another important aspect of the THz band is that molecular absorption, e,g, water vapor, plays a significant role in the waveform propagation. As such, the available transmission bandwidth varies as a function of the transmission distance, with the channel acting as a band-pass filter, i.e. creating transmission windows, for transmission distance greater than roughly half a meter for a standard environment. This effect requires the design of adaptive waveforms, where their shape is adapted to the transmission distance.
Meanwhile, channel modelling is a crucial element in the development of efficient and robust communication systems. In collaboration with the National Physical Laboratory (NPL) in UK, we have conducted some initial measurements over an ultra-wide bandwidth in the 500-750 GHz range to understand the behaviour of the THz channel [15], [16]. Our line-of-sight (LoS) measurements have shown the effect of molecular absorption; its induced losses in the received signal strength become more apparent as the distance between the two transmission nodes increases. We also conducted some non-line-of-sight (NLoS) measurements by placing various test materials at a specular angle between the transmitter and receiver ends and our results demonstrate the high frequency selectivity that causes clusters of diffuse components forming at the LoS peak. As the THz spectrum is currently unused and unregulated, it is also important to understand the behaviour of the propagating wave over ultra-wide bandwidths. The main challenges that needs to be addressed when modelling the channel at these frequencies over large bandwidths is the computational complexity faced by deterministic methods such as ray-tracing, i.e. the large number of lengthy measurements that are required to accurately and empirically characterise the propagation channel.
Cell-free Massive MIMO
Cell-free massive MIMO provides a new user-centric and scalable networking architecture for 6G. In Cell-free networks, such as that shown by Figure 5, communications functions are moved to the distributed network edge, implementing user-centric transmissions to overcome the inter-cell interference limitation in 4G and 5G cellular networks. Each user is served by coherent joint transmission from its selected subset of APs (user-specific cluster). This approach eliminates cell edge effects, resulting in more uniform user experience.
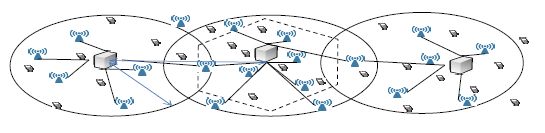
Figure 5. A cell-free network
Figure 6 illustrates the benefits of cell-free massive MIMO in terms of spectral efficiency performance (in bits/s/Hz) at different locations in an area with nine APs. The left-hand figure shows that the performance of cell-edge users is very poor in conventional cellular massive MIMO whereas the right-hand figure shows that cell-free massive MIMO provides almost uniform spectral efficiency thanks to the distributed APs.
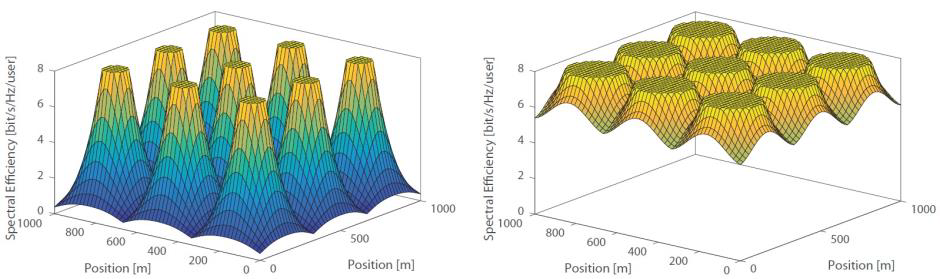
Figure 6. Left: cellular network. Right: cell-free massive MIMO network. Spectral efficiency achieved by users at different locations in an area covered by nine APs that are deployed on a regular grid.
In [19], we studied cell-free massive MIMO systems with limited-capacity front-haul which is the link between each access point and edge processing unit (EPU), and proposed deep convolutional neural network (DCNN) to solve the rate maximisation problem, leading to 70% improvement in sum data rate. In [20], the energy efficiency maximisation problem in cell-free massive MIMO system was investigated taking into account the effects of channel estimation error and quantisation distortion. We decoupled the original problem into two sub-problems, namely, receiver filter coefficient design, and power allocation. An iterative algorithm was proposed to alternately solve each sub-problem. The proposed scheme achieves 60% energy saving compared to conventional equal power allocation. In [21], we investigated the performance of the RIS-aided cell-free massive MIMO system. A novel optimisation scheme was developed. The simulation results demonstrated the superiority of the proposed scheme in terms of maximising the minimum rate of the users compared with the state-of-the-art schemes and 70% improvement in spectrum efficiency compared to the case without RIS.
6G intelligence
So far we have experienced the initial feature of network intelligence in the 5G paradigm, and there is no doubt that the intelligence capability will be further developed into the 6G era with future advancement of artificial intelligence, in particular machine learning (ML) technologies. As mentioned earlier, we envisage consortium-like 6G ecosystems that may flexibly consist of resources provided from different autonomous stakeholders. In this scenario, the resources supplied by different providers are typically managed by specific intelligence or policies from their own owners. Individual stakeholders may have their own business and operational intent, and the corresponding decision-making processes may heavily rely on individually tailored AI algorithms. This is in contrast to the current 5G scenario where an AI-based orchestration function can be fulfilled by a centralised orchestrator across multiple local control agents in different parts of a common network infrastructure, including RAN, transport and core network segments. In the case of multi-stakeholder scenario, intent and behaviours of individual players may interfere with each other in highly dynamic conditions. As such, multi-agent based AI solutions for prediction, detection and resolution of conflicts, in a fully distributed fashion, will be required in order to strike the best trade-off between global optimality (including end-to-end performance assurances) and local business/operation intent. The current intent-based networking (IBN) framework can be deemed as a promising starting point towards such an advanced scenario.
6G RANs will be more complex than earlier generations of RANs and, thus, automation will be required to achieve zero-touch operation. Automation in RAN can be achieved by utilising self-organising network (SON) techniques. Many existing SON designs rely on a rule-based approach to achieve automation. The recent wide spread use of ML techniques in communication has reached SON, where ML-based SON approaches have recently been designed for 5G. The existing ML-based solutions for SON often focus on applying a specific ML technique to automate a certain aspect of SON such as fault detection or self-healing [22]. We expect this trend to carry on beyond 5G. In 6G, with the accumulation of knowledge and experiences in individual ML-based SON design gained in 5G, we foresee that the main focus in SON research will be the convergence and consolidation of various ML algorithms into a single AI-framework that can achieve single-best non-conflicting decision making.
Last but not least, 6G radio technologies will be extremely demanding in terms of spectral efficiency, energy efficiency, reliability, and latency. These are making future wireless systems nonlinear, non-stationary, non-Gaussian, and non-ergodic (called 4N-Wireless). Design and optimisation of 4N-Wireless systems is fundamentally very challenging because there is no general theory available to this date that can handle such complex optimisation problems, and this is where AI and ML can play a central role. For instance, the autoencoder technique can be a useful tool for end-to-end wireless link optimisation, which does not need a trackable communication system model. The recurrent neural network (RNN) can be useful to solve many system reverse problems (such as MIMO precoding, channel equalisation, power amplifier linearisation, etc.) in 4N-Wireless systems. Moreover, AI can help to predict wireless channel changes and enable accurate radio resource scheduling and planning. For example, a deep convolutional neural network (DCNN) was exploited in [19] to optimize the power control in cell-free massive MIMO network. Overall, we expect AI/ML to become essential to 6G radio technologies.
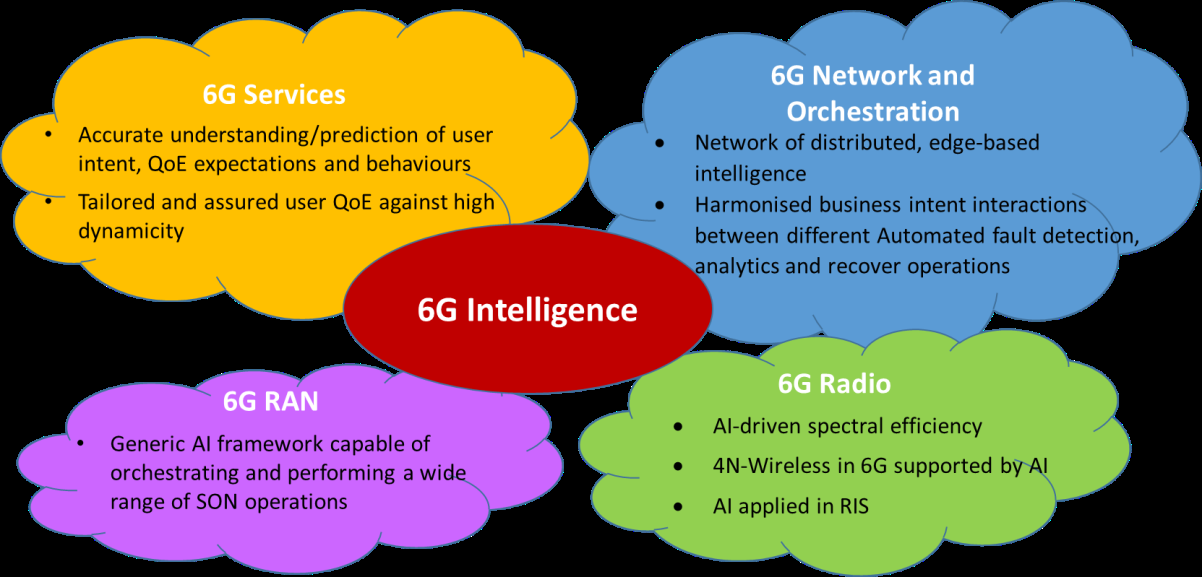
Figure 7. Applications of 6G Intelligence
3. Summary
In this article we highlighted our vision on future 6G networks from 6GIC hosted at the University of Surrey. We specifically elaborated in detail different facades of 6G, including 6G applications, network architectures, emerging radio technologies as well as new 6G intelligence. We also take this opportunity to highlight some of our ongoing work in the context of 6G research. Table 1 provides a summary on key 6G challenges and potential solutions or enabling technologies we have envisaged.
| Challenges | Potential Solutions | |
| 6G applications and requirements | - Blending physical and virtual worlds - Fully immersive eXtended Reality (XR) including Holographic Teleportation |
- Pervasive network availability - Beyond Gbps data rate - Ambient and user sensing - Ultra-precise localisation and synchronisation |
| 6G network architectures | - Seamless Integration of heterogeneous networks and capabilities | - New 6G architectures with open and flexible network capability integration |
| - Unified and direct UE access of connectivity | - New space-terrestrial network integration | |
| - Inconsistent network performance at cell-edge due to interference | - Cell-free network architecture | |
| 6G wireless technologies | - Unfavourable propagation environment at higher frequencies | - Reconfigurable Intelligent Surfaces to manipulate the physical environment |
| - Nonlinear, non-stationary, non-Gaussian, and non-ergodic wireless systems (4N-wireless) | - AI/ML applied to wireless signal processing | |
| 6G network and resource management | - Zero-touch network control and management in complex environments - Advanced intent-based network management paradigms |
- Harmonising co-existing stakeholders and players in the 6G - Distributed AI framework |
Table 1. Summary 6G technical challenges and potential solutions
While it is too early to predict whether the realisation of future 6G will follow in an evolutionary or revolutionary fashion, or a mixture, we have already identified some key enabling technologies and future directions as elaborated in this article.
References
[1] 5/6G Innovation Centre, “6G Wireless – A New Strategic Vision”, https://www.surrey.ac.uk/sites/default/files/2020-11/6g-wireless-a-new-strategic-vision-paper.pdf
[2] ITU Network 2030 white paper “A Blueprint of Technology, Applications and Market Drivers Towards the Year 2030 and Beyond”, https://www.itu.int/en/ITU-T/focusgroups/net2030/Documents/White_Paper.pdf
[6] Araghi, M. Khalily, P. Xiao, and R. Tafazolli, “Holographic-based leaky-wave structures: Transformation of guided waves to leaky waves,”IEEE Microwave Magazine, vol. 22, no. 6, pp. 49–63, 2021.
[7] A. Araghi, M. Khalily, P. Xiao, R. Tafazolli, ”Holographic-based mmw-wideband bidirectional frequency scanning leaky wave antenna,” in 14thEuropean Conference on Antennas and Propagation (EuCAP), 2020.
[8] Zheng Chu, et. al. “Intelligent Reflect Surface Aided Multi-antenna Secure Transmission”. IEEE Wireless Communications Letters, vol. 9, no. 1, pp. 108-112, Jan. 2020.
[9] Zheng Chu, et. al. "Secrecy Rate Optimization for Intelligent Reflecting Surface Assisted MIMO System". IEEE Transactions on Information Forensics and Security, vol. 16, pp. 1655-1669, Nov. 2020.
[10] Zheng Chu, et. al. “Intelligent Reflecting Surfaces Enabled Cognitive Internet of Things Based on Practical Pathloss Model’’, China Communications, vol. 17, no. 12, 2020.
[11] Manijeh Bashar, et. al. “On the Performance of Reconfigurable Intelligent Surface-Aided Cell-Free Massive MIMO Uplink”. IEEE Globecom 2020.
[12] Zheng Chu, et. al. “Intelligent Reflecting Surface Assisted Mobile Edge Computing for Internet of Things”, IEEE Wireless Commun. Lett., vol. 10, no. 3, pp. 619-623, March 2021.
[13] M. Alibakhshikenari et al., "High-Gain On-Chip Antenna Design on Silicon Layer With Aperture Excitation for Terahertz Applications," in IEEE Antennas and Wireless Propagation Letters, vol. 19, no. 9, pp. 1576-1580, Sept. 2020, doi: 10.1109/LAWP.2020.3010865.
[14] S. B. Amlashi, M. Khalily, T. Brown, P. Xiao and R. Tafazolli, "An Efficient Plasmonic Photoconductive Antenna for Terahertz Continuous-Wave Applications," 2021 15th European Conference on Antennas and Propagation (EuCAP), 2021, pp. 1-5, doi: 10.23919/EuCAP51087.2021.9410902.
[15] S. B. Amlashi, M. Khalily, V. Singh, P. Xiao, J. D. Carey and R. Tafazolli, "Surface Electromagnetic Performance Analysis of a Graphene-Based Terahertz Sensor Using a Novel Spectroscopy Technique," in IEEE Journal on Selected Areas in Communications, vol. 39, no. 6, pp. 1797-1816, June 2021, doi: 10.1109/JSAC.2021.3071835.
[16] Niknam S, Yazdi M, Behboudi Amlashi S and Khalily M (2020) Numerical Performance Analysis of Terahertz Spectroscopy Using an Ultra-Sensitive Resonance-Based Sensor. Front. Phys. 8:19. doi: 10.3389/fphy.2020.00019.
[17] D. Serghiou, Mohsen Khalily et al., "Ultra-Wideband Terahertz Channel Propagation Measurements from 500 to 750 GHz," 2020 International Conference on UK-China Emerging Technologies (UCET), Glasgow, United Kingdom, 2020, pp. 1-4,
[18] D. Serghiou, Mohsen Khalily, et al., "Comparison of Diffuse Roughness Scattering from Material Reflections at 500-750 GHz," 2021 15th European Conference on Antennas and Propagation (EuCAP), 2021, pp. 1-5.
[19] M. Bashar, et. al. “Exploiting Deep Learning in Limited-Fronthaul Cell-Free Massive MIMO Uplink,” IEEE JSAC special issue on Multiple Antenna Technologies for Beyond 5G, vol. 38. no. 8, August 2020.
[20] M. Bashar, et. al. “Energy Efficiency of the Cell-Free Massive MIMO Uplink with Optimal Uniform Quantization,” IEEE Transactions on Green Communications and Networking, vol. 3, no. 4, Dec. 2019.
[21] M. Bashar, et. al. “On the Performance of Reconfigurable Intelligent Surface-Aided Cell-Free Massive MIMO Uplink”. IEEE Globecom 2020.
[22] Mulvey, et al. "Cell Fault Management Using Machine Learning Techniques," IEEE Access, vol. 7, pp. 124514-124539, 2019.
Secure RF/FSO Communications Towards the 6G Era
Olfa Ben Yahia and Gunes Karabulut Kurt, Polytechnique Montreal, Canada; Eylem Erdogan, Istanbul Medeniyet University, Turkey; Ibrahim Altunbas, Istanbul Technical University, Turkey; and Halim Yanikomeroglu, Carleton University, Canada
(This email address is being protected from spambots. You need JavaScript enabled to view it., This email address is being protected from spambots. You need JavaScript enabled to view it., This email address is being protected from spambots. You need JavaScript enabled to view it., This email address is being protected from spambots. You need JavaScript enabled to view it., This email address is being protected from spambots. You need JavaScript enabled to view it.)
Abstract
Compared to terrestrial infrastructures, wireless heterogeneous networks provide cost-effective global coverage with high-speed data connectivity. Furthermore, to overcome the spectrum limitations imposed by radio frequency communication and to meet the demands of high data rates, free-space optical links present an alternative solution. This work sheds the light on the physical characteristics of radio frequency and free-space optical links from a communication and physical layer security perspectives. Motivated by the complementary behavior of both communication channels, we first investigate hybrid radio frequency/free-space optical communications. Then, we provide an overview of the physical layer security of both channels considering different scenarios and conditions.
1. Introduction
The seamless integration of space and terrestrial networks is one of the promising architectural aspects of the sixth generation (6G) networks. Known as a vertical heterogeneous network (VHetNet), this architecture comprises space, aerial, and terrestrial networks. The envisioned space network consists of different types of satellite constellations, including geostationary Earth orbit, medium Earth orbit, and low Earth orbit (LEO), which are connected via high data rates inter-satellite links. LEO satellites are expected to have a pivotal role in future wireless communication by providing high data rate, low latency, and wide coverage that includes remote rural areas. For this reason, thousands of LEO satellites are planned to be launched for deployment by different commercial and public companies in the next decade, where these companies want to design a flexible network with seamless global coverage and high capacity.
The aerial network layer, which includes flying platforms, is divided into two interacting sub-layers [1]. The first sublayer is composed of unmanned aerial vehicle (UAV) nodes, which are known as drones. UAVs are low-altitude flying vehicles operating near the ground up to 150 m. UAVs provide inherent characteristics such as flexibility, mobility, easy deployment, and low costs. In recent years, UAVs have become enablers for different wireless applications that include surveillance, monitoring, military operations, and delivery due to their capabilities to hover at adaptive altitudes [2]. The second sub-layer includes high altitude platform station (HAPS) systems, also known as stratospheric repeaters [3]. HAPS is defined as a quasi-stationary object flying at an altitude of 20 to 50 km, whereas, most of the recent deployments focused on an altitude between 18 km and 20 km [4]. HAPS systems can offer complementary characteristics over satellite communication (SatCom) and terrestrial infrastructure. These stratospheric platforms provide narrowband, broadband, and broadcasting telecommunication services [3]. Positioned above the clouds, HAPS systems can serve large areas due to their large footprint with lower costs compared to LEO satellites.
Up to date, the majority of existing VHetNet links are operating based on microwave radio frequency (RF) bands. However, RF communication requires regulatory restrictions, high costs, provides limited capacity, and cannot meet the high demands in data rate communication. Moreover, RF communication is prone to an interception, jamming, and security risks. Thus, owing to the good directivity and the fast deployment, free-space optical (FSO) communication is the key enabler to meeting these high data rate requirements and solving the above problems. However, it is worth mentioning that FSO communication is sensitive to weather conditions, atmospheric effects, beam wanders, and pointing errors. Furthermore, due to diffraction, an amount of the beam can be reflected by small particles present in the atmosphere and then received by illegitimate users [5]. Moreover, when there is no perfect line-of-sight between transmitter and receiver caused by pointing error issues, an eavesdropper can capture the information.
Overall, the vision of 6G is produced by several innovations and developments in architecture, applications, and technologies. Meanwhile, attackers become more powerful and sophisticated, capable of developing new types of security risks [6]. In this context, to study the secrecy performance of future networks from a physical layer perspective, we first need to understand the communication performance. Herein, our work provides a comprehensive study of the physical layer of non-terrestrial networks (NTN) from two aspects; communication and security.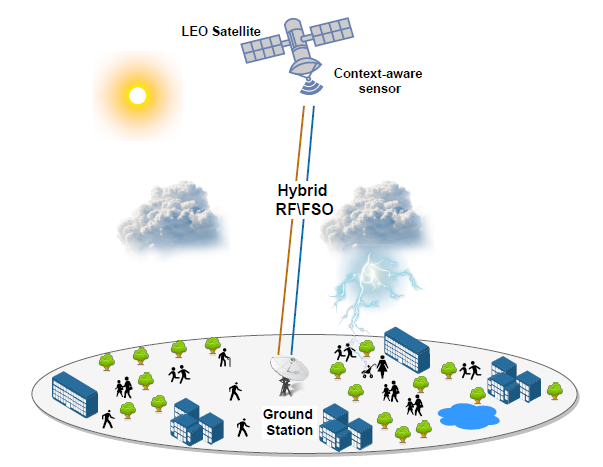
Figure 1: Illustration of weather-dependent hybrid RF/FSO SatCom.
2. Hybrid RF/FSO communication
Due to the complementary nature of RF and FSO channels, we propose two different system models in which we implement RF and FSO links in parallel [7], [8]. As widely known, the performance of FSO communication is highly degraded by fog and snow, whereas RF communication is highly affected by rain [9]. Thus, we propose two novel reliable strategies for downlink SatCom using hybrid RF/FSO communication.
In the first model which is shown in Figure 1, we consider an LEO satellite communicating with a ground station (GS) through RF and FSO communication [7]. In the proposed strategy, the LEO satellite can switch between RF and FSO links depending on the weather status obtained from the sensors on the satellite and used for context awareness. Moreover, we allocate equal transmit power on both channels. In this approach, we assume three different states of weather. In State-0, we assume the presence of a thin cloud. Thus, both RF and FSO channels show high performance, and both might be active simultaneously and combined at the GS using the selection combining (SC) scheme. For State-1, we assume rainy weather, thus the RF channel is highly affected and the transmission is handled through FSO communication using the total transmit power Pt. Likewise, for State-2, we assume foggy weather where FSO communication is not available and the RF channel is used with total transmit power Pt. The simulation results have shown that our proposed strategy outperforms the dualmode hybrid RF/FSO communication in which the total transmit power is always divided into Pt/2 for all states in terms of outage probability. Thus, our proposed scheme improves power efficiency. Moreover, we study the impact of non-zero boresight pointing error and the impact of the aperture averaging technique for the proposed setup. The results have revealed that increasing the boresight displacement deteriorates the overall performance. Furthermore, increasing the aperture size can alleviate the effects of misalignment and atmospheric turbulence and thus improve performance.
In the second scenario, the communication between an LEO satellite and a GS may be unavailable due to barriers, shadowing effects, or huge attenuation between them. Thus we propose to use a dual-hop multi-relay scheme to guarantee reliable communication as illustrated in Figure 2. Recently, the authors in [10], [11] introduced the use of HAPS in hybrid RF/FSO SatCom communication. It has been observed that the use of HAPS enhances the reliability of SatCom systems. Therefore, different from the current literature, we propose a novel HAPS selection strategy for hybrid RF/FSO communication [8]. Specifically, a HAPS system that can provide the best channel characteristics is selected in the first hop and acts as a decode-and-forward relay. In the second hop, the selected HAPS decodes and forwards the signal to the GS through hybrid RF/FSO communication. At the GS, SC is deployed with equal transmit power on both channels. In this work, we consider the effects of stratospheric attenuation, atmospheric turbulence, atmospheric attenuation due to scattering, path loss, fading, and temperature. Furthermore, we studied the impact of zero-boresight pointing errors, and aperture averaging techniques. From the simulation results, we concluded that the proposed scheme outperforms the single-hop RF and FSO communications, single-hop hybrid RF/FSO, the HAPS-aided FSO, and HAPS-aided RF communications. Thus, the use of HAPS as a relay node improves SatCom’s performance as the FSO link from the satellite to the HAPS is barely affected by atmospheric conditions. Also, the HAPS selection scheme based on the satellite-HAPS channel quality enhances the overall performance. 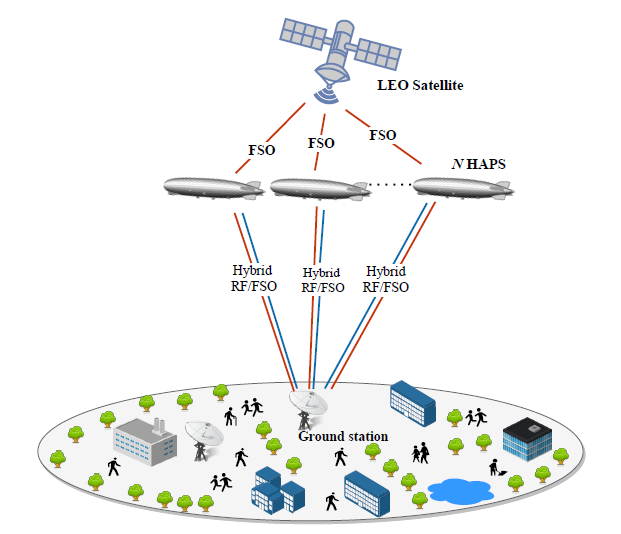
Figure 2: Illustration of the HAPS node selection for hybrid RF/FSO SatCom.
Furthermore, for rainy weather, the RF link is highly affected, yet, it remains available. The FSO communication is slightly affected by rain, whereas, it is highly deteriorated by fog. The misalignment between the satellite and the HAPS node introduced by pointing errors degrades the overall performance. To reduce the impact of turbulence-induced fading and pointing errors, the aperture averaging technique can be used. In addition, the results have shown that decreasing the zenith angle or the wind speed decreases the atmospheric attenuation and enhances the overall performance.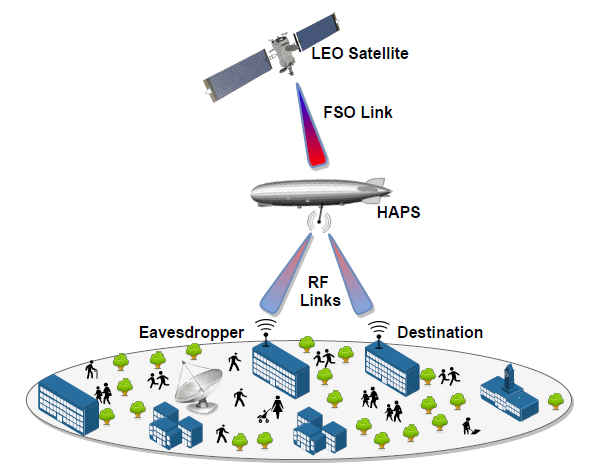
Figure 3: Illustration of the HAPS-aided FSO-RF SatCom system model.
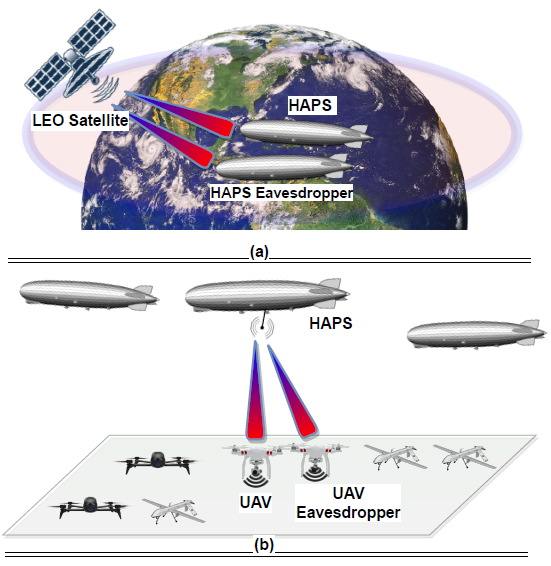
Figure 4: (a) HAPS eavesdropping, (b) UAV eavesdropping.
3. Physical Layer Security Performance
To investigate the RF eavesdropping in downlink SatCom, we proposed a new dual-hop HAPS-aided downlink communication [12]. As shown in Figure 3, we assumed an LEO satellite communicating with a GS through a HAPS node in the presence of a malicious user located on the ground and trying to intercept the communication. FSO communication is adopted between the satellite and the HAPS node, whereas RF communication is considered between the HAPS and the ground receivers. We derived closed-form of secrecy outage probability (SOP) and probability of positive secrecy capacity (PPSC) expressions by considering the impact of pointing errors and different shadowing levels. The simulation results have shown that the proposed HAPS-aided FSO-RF SatCom model is more secure than direct satellite-ground RF communication. Due to its strategic position, the HAPS node is able to provide secure communication even in harsh winds in the first hop of communication. Furthermore, the zenith angle is considered an important enabler in the design of FSO communication to decrease the effects of atmospheric conditions. For the design of the RF communication, severe shadowing effects deteriorate the overall secrecy performance. Furthermore, as the pointing errors increases, the system performance worsens. Finally, the average signal-to-noise ratio (SNR) of the eavesdropper can be a crucial parameter to guarantee secure communication.
In what follows, we investigate optical eavesdropping in NTNs [13], [14]. We proposed novel use cases for attacks in space as can be seen in Figure 4. In the first use case, we assumed an LEO satellite that is communicating with a HAPS node while an external HAPS is trying to collect the transmitted information. In the second use case, we considered a HAPS node sending secret information to a UAV in the presence of a UAV eavesdropper. The communication in both scenarios is through FSO links. Furthermore, we assumed that the illegitimate receivers are located very close to the main receivers. Final expressions of SOP and PPSC were derived and validated with MC simulations. In this work, we studied the effects of zenith angle, wind speed, aperture averaging technique, and atmospheric/stratospheric attenuation. The simulation results have shown that the HAPS eavesdropping scenario is more secure than the UAV eavesdropping. Furthermore, the higher the wind speed level, the more the leakage of the information to the eavesdropper. This shows the huge impact of atmospheric effects on the secrecy performance.
In the scenario depicted in Figure 5, we proposed a satellite eavesdropping strategy, in which the optical communications established between an LEO satellite and a HAPS node can be captured by an attacker spacecraft, which is located within the convergence area of the transmitted optical beam [14]. Considering two practical eavesdropping scenarios, satellite-to-HAPS (downlink) and HAPS-to-satellite (uplink), we derived novel expressions of average secrecy capacity, SOP, and secrecy throughput. The main findings of this work can be summarized as follows. In terms of SOP, the satellite-to-HAPS communication shows better performance as the eavesdropper gathers more information in the uplink due to reflection or refraction based on the large distance. Additionally, the secrecy performance is directly affected by the fluctuations in the signal due to atmospheric conditions. Finally, it has been observed that after a certain level of secrecy rate, the system’s reliability and secrecy are compromised.
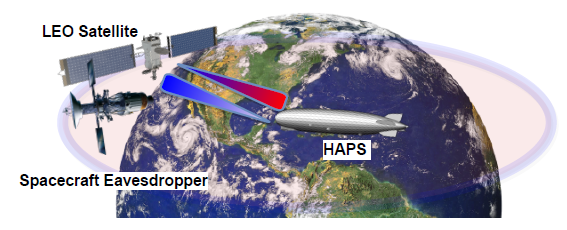
Figure 5: Illustration of the satellite eavesdropping.
According to [15], the threats given in this work can be categorized as loss of confidentiality, as the attacker eavesdrops or accesses sensitive information. To summarize, both the ground and space segments are susceptible to diverse types of attacks including electronic and physical ones. In addition, the development of new technologies for the 6G including artificial intelligence techniques and smart surfaces may introduce new threats such as poisoning and evasion attacks [6].
4. Conclusion
To conclude, the channel modeling and the radio propagation environment must be carefully designed to meet the envisioned requirements of future wireless networks in terms of quality of service and security. In this work, we summarized our studies concerning the physical layer performance of NTNs from a communication perspective, as well as evaluating the secrecy performance while assuming random channel characteristics without having any knowledge of the attacker’s ability.
In future work, we intend to propose new mitigation techniques for predicting, detecting, and preventing potential threats in the next generations of wireless networks. Finally, to enhance privacy and provide redundant security, a cross-layer framework can be considered in a use-case specific manner for the target service reliability level.
References
[1] M. S. Alam, G. Karabulut Kurt, H. Yanikomeroglu, P. Zhu, and N. D. D`ao, “High altitude platform station based super macro base station constellations,” IEEE Communications Magazine, vol. 59, no. 1, pp. 103–109, 2021.
[2] M. Mozaffari, W. Saad, M. Bennis, Y.-H. Nam, and M. Debbah, “A tutorial on UAVs for wireless networks: Applications, challenges, and open problems,” IEEE Communications Surveys Tutorials, vol. 21, no. 3, pp. 2334–2360, 2019.
[3] A. Aragon-Zavala, J. L. Cuevas-Ru´ız, and J. A. Delgado-Pen´ın, High-Altitude Platforms for Wireless Communications. John Wiley & Sons, 2008.
[4] G. Karabulut Kurt, M. G. Khoshkholgh, S. Alfattani, A. Ibrahim, T. S. J. Darwish, M. S. Alam, H. Yanikomeroglu, and A. Yongacoglu, “A vision and framework for the high altitude platform station (HAPS) networks of the future,” IEEE Communications Surveys Tutorials, vol. 23, no. 2, pp. 729–779, 2021.
[5] F. J. Lopez-Martinez, G. Gomez, and J. M. Garrido-Balsells, “Physical-layer security in free-space optical communications,” IEEE Photonics Journal, vol. 7, no. 2, pp. 1–14, 2015.
[6] P. Porambage, G. G¨ur, D. P. M. Osorio, M. Liyanage, A. Gurtov, and M. Ylianttila, “The roadmap to 6G security and privacy,” IEEE Open Journal of the Communications Society, vol. 2, pp. 1094–1122, 2021.
[7] O. Ben Yahia, E. Erdogan, G. Karabulut Kurt, I. Altunbas, and H. Yanikomeroglu, “A weather-dependent hybrid RF/FSO satellite communication for improved power efficiency,” IEEE Wireless Communications Letters, vol. 11, no. 3, pp. 573–577, 2022.
[8] “HAPS selection for hybrid RF/FSO satellite networks,” IEEE Transactions on Aerospace and Electronic Systems, (early access), pp. 1–13, 2022.
[9] F. Nadeem, V. Kvicera, M. S. Awan, E. Leitgeb, S. S. Muhammad, and G. Kandus, “Weather effects on hybrid FSO/RF communication link,” IEEE Journal on Selected Areas in Communications, vol. 27, no. 9, pp. 1687–1697, 2009.
[10] R. Swaminathan, S. Sharma, N. Vishwakarma, and A. Madhukumar, “HAPS-based relaying for integrated space-air-ground networks with hybrid FSO/RF communication: A performance analysis,” IEEE Trans. Aerosp. Electron. Syst., vol. 17, pp. 1–17, 2021.
[11] S. Shah, M. Siddharth, N. Vishwakarma, R. Swaminathan, and A. S. Madhukumar, “Adaptive-combining-based hybrid FSO/RF satellite communication with and without HAPS,” IEEE Access, vol. 9, pp. 81 492–81 511, 2021.
[12] O. Ben Yahia, E. Erdogan, and G. Karabulut Kurt, “On the use of HAPS to increase secrecy performance in satellite networks,” in IEEE International Conference on Communications Workshops (ICC Workshops), 2021, pp. 1–6.
[13] O. Ben Yahia, E. Erdogan, G. Karabulut Kurt, I. Altunbas, and H. Yanikomeroglu, “Physical layer security framework for optical non-terrestrial networks,” in International Conference on Telecommunications (ICT), 2021, pp. 162–166.
[14] “Optical satellite eavesdropping,” IEEE Transactions on Vehicular Technology, (early access), pp. 1–6, 2022.
[15] A. Dutta and E. Hammad, “5G security challenges and opportunities: A system approach,” in IEEE 5G World Forum (5GWF), 2020, pp. 109–114.6
 Olfa Ben Yahia received the Engineering degree with honors in Telecommunications from the Ecole Nationale d’Electronique et des T´el´ecommunications de Sfax, Sfax, Tunisia, in 2016 and the Ph.D. degree in Telecommunications Engineering from Istanbul Technical University, Istanbul, Turkey in 2022. She is currently a Postdoctoral Fellow with the Department of Electrical Engineering, Polytechnique Montr´eal, Montreal, QC, Canada. Her current research interests include optical wireless communications, performance analysis of physical layer security, satellite communication, aerial platforms, and cooperative communications. She is a Graduate Student Member of IEEE.
Olfa Ben Yahia received the Engineering degree with honors in Telecommunications from the Ecole Nationale d’Electronique et des T´el´ecommunications de Sfax, Sfax, Tunisia, in 2016 and the Ph.D. degree in Telecommunications Engineering from Istanbul Technical University, Istanbul, Turkey in 2022. She is currently a Postdoctoral Fellow with the Department of Electrical Engineering, Polytechnique Montr´eal, Montreal, QC, Canada. Her current research interests include optical wireless communications, performance analysis of physical layer security, satellite communication, aerial platforms, and cooperative communications. She is a Graduate Student Member of IEEE.
 Eylem Erdogan received B.Sc. and M.Sc. degree from Is¸ık University, Istanbul, Turkey and the Ph.D. degree from Kadir Has University, Istanbul, Turkey in 2014 all in electronics engineering. He is currently an Associate Professor in the Department of Electrical and Electronics Engineering, Istanbul Medeniyet University. He was a Post-Doctoral Fellow in Electrical Engineering department, Lakehead University, Thunder Bay, ON, Canada from March 2015 to September 2016 and a visiting professor in Carleton University, Ottawa, Canada during summer 2019. He has authored or coauthored more than 30 papers in peer-reviewed SCI/SCI-E journals and international conferences. His research interests include the broad areas of wireless communications, including cognitive radio net- works, physical layer security of wireless systems, nonterrestrial networks, free-space optical communications, and satellite communications. He is a Senior Member of IEEE.
Eylem Erdogan received B.Sc. and M.Sc. degree from Is¸ık University, Istanbul, Turkey and the Ph.D. degree from Kadir Has University, Istanbul, Turkey in 2014 all in electronics engineering. He is currently an Associate Professor in the Department of Electrical and Electronics Engineering, Istanbul Medeniyet University. He was a Post-Doctoral Fellow in Electrical Engineering department, Lakehead University, Thunder Bay, ON, Canada from March 2015 to September 2016 and a visiting professor in Carleton University, Ottawa, Canada during summer 2019. He has authored or coauthored more than 30 papers in peer-reviewed SCI/SCI-E journals and international conferences. His research interests include the broad areas of wireless communications, including cognitive radio net- works, physical layer security of wireless systems, nonterrestrial networks, free-space optical communications, and satellite communications. He is a Senior Member of IEEE.
 Gunes Karabulut Kurt received the B.S. degree with high honors in electronics and electrical engineering from the Bogazici University, Istanbul, Turkey, in 2000 and the M.A.Sc. and the Ph.D. degrees in electrical engineering from the University of Ottawa, ON, Canada, in 2002 and 2006, respectively. Between 2010 and 2021, she was with Istanbul Technical University. She is currently an Associate Professor of Electrical Engineering at Polytechnique Montr´eal, Montreal, QC, Canada. She is also currently serving as an Associate Technical Editor (ATE) of the IEEE Communications Magazine and a member of the IEEE WCNC Steering Board. Her current research interests include space information networks, satellite networking, wireless network coding, wireless security, space security, and wireless testbeds radio. She is the chair of the IEEE special interest group entitled “Satellite Mega-constellations: Communications and Networking.”
Gunes Karabulut Kurt received the B.S. degree with high honors in electronics and electrical engineering from the Bogazici University, Istanbul, Turkey, in 2000 and the M.A.Sc. and the Ph.D. degrees in electrical engineering from the University of Ottawa, ON, Canada, in 2002 and 2006, respectively. Between 2010 and 2021, she was with Istanbul Technical University. She is currently an Associate Professor of Electrical Engineering at Polytechnique Montr´eal, Montreal, QC, Canada. She is also currently serving as an Associate Technical Editor (ATE) of the IEEE Communications Magazine and a member of the IEEE WCNC Steering Board. Her current research interests include space information networks, satellite networking, wireless network coding, wireless security, space security, and wireless testbeds radio. She is the chair of the IEEE special interest group entitled “Satellite Mega-constellations: Communications and Networking.”
 Ibrahim Altunbas received the B.Sc., M.Sc. and Ph.D. degrees, all in electronics and communication engineering, from the Istanbul Technical University, Istanbul, Turkey, in 1988, 1992 and 1999, respectively. He is currently a Professor at the same university. Between January 2001 - November 2001, he was a Visiting Researcher at Texas A&M University, USA. Between November 2001 - September 2002 and June 2015 - August 2015, he was a Postdoctoral Fellow and a Visiting Researcher, respectively at the University of Ottawa, Canada. His current research interests include spatial modulation, non-orthogonal multiple access, physical layer security, satellite and UAV/drone-integrated wireless communications, reconfigurable intelligence surface-based communication. He is a Senior
Ibrahim Altunbas received the B.Sc., M.Sc. and Ph.D. degrees, all in electronics and communication engineering, from the Istanbul Technical University, Istanbul, Turkey, in 1988, 1992 and 1999, respectively. He is currently a Professor at the same university. Between January 2001 - November 2001, he was a Visiting Researcher at Texas A&M University, USA. Between November 2001 - September 2002 and June 2015 - August 2015, he was a Postdoctoral Fellow and a Visiting Researcher, respectively at the University of Ottawa, Canada. His current research interests include spatial modulation, non-orthogonal multiple access, physical layer security, satellite and UAV/drone-integrated wireless communications, reconfigurable intelligence surface-based communication. He is a Senior
Member of IEEE.
 Halim Yanikomeroglu is a Professor in the Department of Systems and Computer Engineering at Carleton University, Ottawa, Canada. He received the BSc degree in electrical and electronics engineering from the Middle East Technical University, Turkey, in 1990, and the MASc degree in electrical engineering and the PhD degree in electrical and computer engineering from the University of Toronto, in 1992 and 1998, respectively. His research group has made substantial contributions to 4G and 5G wireless technologies; his group’s current focus is the wireless infrastructure for 6G networks and beyond. His extensive collaboration with industry resulted in 39 granted patents. He is a Fellow of IEEE, EIC (Engineering Institute of Canada), and CAE (Canadian Academy of Engineering), and a Distinguished Speaker for both IEEE Communications Society and IEEE Vehicular Technology Society. Dr. Yanikomeroglu received several awards for his research, teaching, and service.
Halim Yanikomeroglu is a Professor in the Department of Systems and Computer Engineering at Carleton University, Ottawa, Canada. He received the BSc degree in electrical and electronics engineering from the Middle East Technical University, Turkey, in 1990, and the MASc degree in electrical engineering and the PhD degree in electrical and computer engineering from the University of Toronto, in 1992 and 1998, respectively. His research group has made substantial contributions to 4G and 5G wireless technologies; his group’s current focus is the wireless infrastructure for 6G networks and beyond. His extensive collaboration with industry resulted in 39 granted patents. He is a Fellow of IEEE, EIC (Engineering Institute of Canada), and CAE (Canadian Academy of Engineering), and a Distinguished Speaker for both IEEE Communications Society and IEEE Vehicular Technology Society. Dr. Yanikomeroglu received several awards for his research, teaching, and service.
Indoor Coverage - The Key to Delivering 5G
Adrian O’Connor, Benetel
Many of the transformative applications upon which 5G’s revenue generating promise are based will require indoor coverage. However, this is challenging to mobile network operators (MNOs). The traditional MNO business case does not justify the deployment of infrastructure within office complexes, factories, etc. Although indoor coverage is certain to be an essential element for driving the economic success of 5G, it will therefore call for a disruption of the established supply chain. The objective of the following article is to show how this can be achieved by opening up the radio access network (RAN) to a broader cross section of vendors.
The RAN is typically the most expensive component of MNO infrastructure, accounting for as much as 70% of the total cost of ownership (TCO) of the network (according to Ericsson Technology Review figures). Making RAN implementations more cost effective represents the biggest barrier to the widespread roll-out of indoor cellular coverage and 5G is exacerbating this significantly. In order to deliver the throughput, capacity and connectivity requirements outlined within the 5G specification, MNOs are going to need to undertake heavy financial outlay on their existing RANs - increasing network cell densities and adding technologies such as massive MIMO in order to improve spectrum utilization and support the propagation characteristics of 5G signals.
Faced with these unprecedented demands, MNOs will find it difficult to make the additional investments required to provide indoor coverage. At the same time, it is impractical for building owners to host the infrastructure of multiple MNOs.
1. Addressing Indoor Coverage Challenges
It is widely reported that over 80% of cellular traffic originates or terminates indoors, and this demand for indoor connectivity is only set to heighten. It will increase as the number of connected IoT devices that must be supported grows and new applications emerge, such as the Industry 4.0, building automation, augmented reality, etc.
The high cost and lack of flexibility of the RAN has led governments and industry bodies to address the whole structure and supply chain of the cellular network. There is widespread recognition that the cloud-level economies of scale required to remove this roadblock can only be achieved by creating an OpenRAN ecosystem.
2. Addressing the Challenge - Opening the RAN
A number of industry bodies, including the O-RAN Alliance, the Telecom Infra Project (TIP) and the Small Cell Forum, have been instrumental in driving the definition, adoption and deployment of OpenRAN options and standards. Based on this work, 3GPP has defined a number of different functional splits. Here the essential functionality of the RAN is spread across three defined elements - namely the centralized unit (CU), the distributed unit (DU) and the radio unit (RU). Each split places a different proportion of the workload on these three respective elements, and assigns them with responsibility for certain key activities. The different potential functional splits that can be implemented are described in Figure 1.
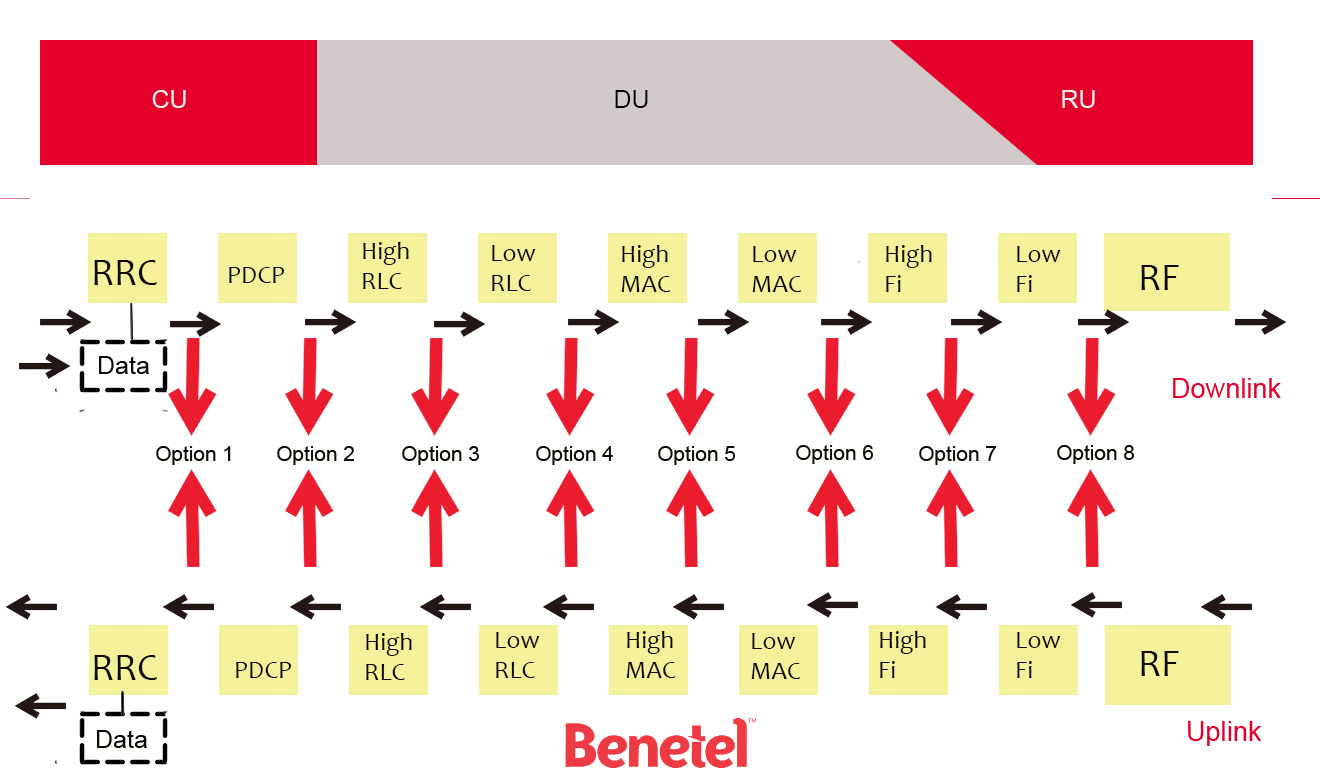
Figure 1: The functional splits available and how these define the way in which the 5G NR stack is allocated to the logical nodes
Through this disaggregation of conventional vertically integrated base station architectures, it is possible for more flexible deployments to be realized with lower associated costs. Although the industry had already taken some steps in this direction, the disaggregated interfaces were initially still of a proprietary nature. This kept barriers to new entrants in place and stifled technological progression.
In contrast, by creating a set of open standards, the above organizations are now able to encourage new vendors to develop solutions based on their specific areas of expertise. With network functions separated, solutions from multiple vendors can all be run on the same hardware. The upshot of this being increased flexibility for MNOs, and further reductions in TCO. Ultimately, having a RAN that is fully open will drive down the expense involved by leveraging standard components for common tasks, enabling competition and avoiding vendor lock-in.
As OpenRAN technology has gained momentum, a new breed of innovative suppliers are now becoming part of the ecosystem. These are bringing new hardware and software products onto the market - reducing the cost, power budget and space constraint issues that previously limited indoor deployment viability. It is now possible, for example, to install high performance RUs containing MIMO functionality indoors.

Figure 2: The Benetel RAN550 OpenRAN RU for indoor deployment
An example of this is Benetel’s RAN550 RU, as shown in Figure 2., incorporating RF transceiver technology from Analog Devices and FPGA technology from Intel, this OpenRAN radio hardware is based on a 7.2 functional split for maximum operational deployment versatility. It has a 4T4R antenna arrangement for MIMO transmission, and delivers 100MHz of instantaneous bandwidth. Versions can be selected from for addressing the n78 (3.3GHz to 3.8GHz), n77u (3.7GHz to 4.2GHz) and n79 (4.4GHz to 5.0GHz) frequency bands. 256 quadrature amplitude modulation (QAM) is employed for downloads and 64 QAM is used for uploads.
Through its 10Gbit/s Ethernet ports, the RAN550 can make use of existing cabling infrastructure to connect to the corresponding CU and DU elements. It can draw from a 12-volt supply, as well having built-in Power-over-Ethernet (PoE) capabilities. Thanks to its compact dimensions and straightforward mounting, this RU is easy to install within office environments.
3. Leveraging the OpenRAN
Disruption of the RAN supply chain will have major implications for 5G - enabling different business models to be experimented with and a wider array of vendors to participate. The reduced TCO and more flexible architectures resulting from the arrival of OpenRAN mean that provisioning of indoor coverage is one of the use cases that will significantly benefit.
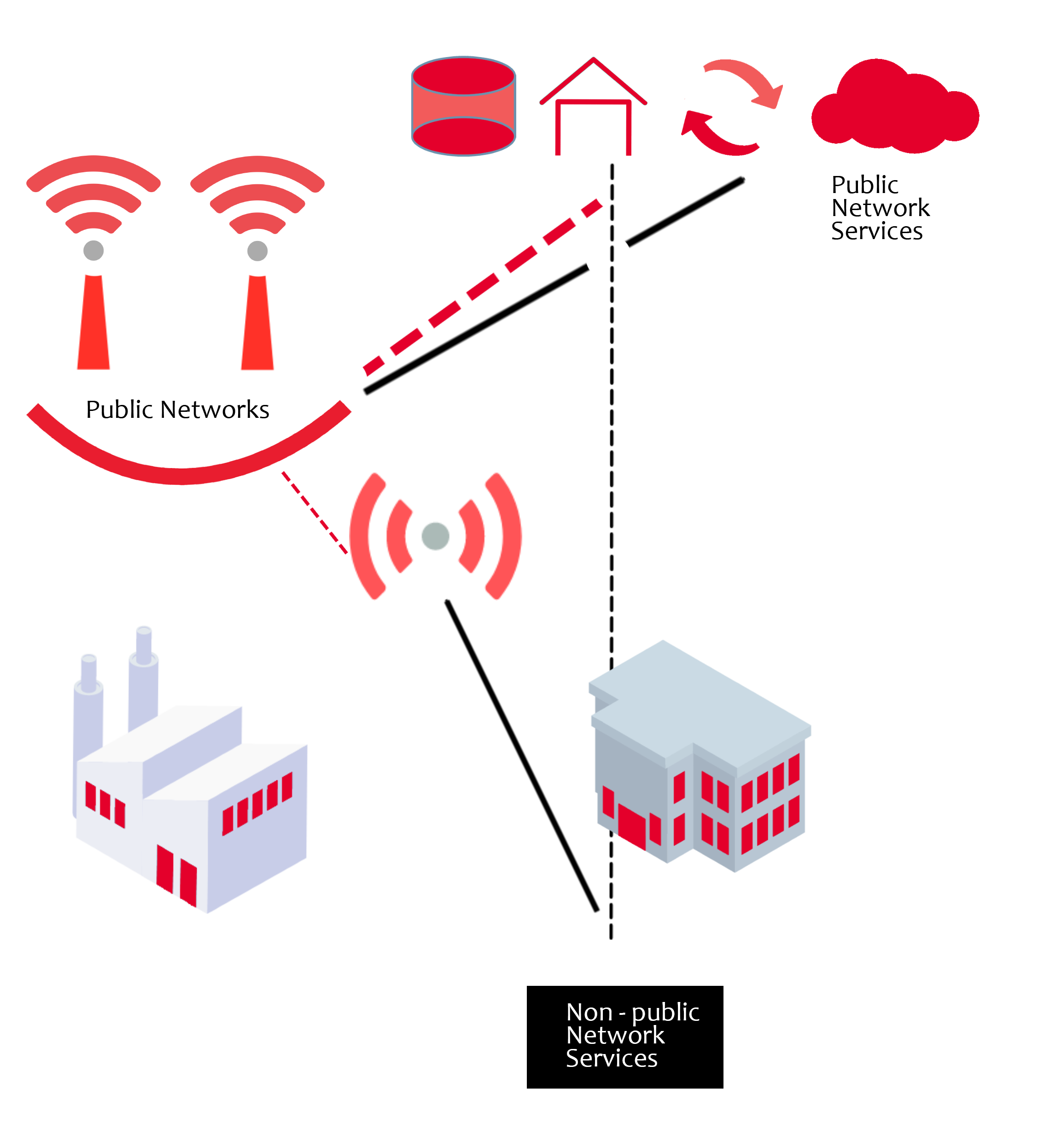
Figure 3: Sharing of the RAN with the public network is one of the NPN deployment options that can be utilized
It is now becoming practical for enterprises to consider implementing non-public networks (NPNs) to address specific operational needs. A factory owner, for example, may decide to do so in order to meet the security or real-time requirements of their site. They will be able to mix and match network functionality - drawing on aspects of their NPN or the 5G network provided by their MNO, as illustrated in Figure 3. The NPN can be completely isolated from the public network, can share the RAN with the public network, share RAN and control plane functionality, or even be completely hosted by the MNO, as particular requirements dictate.
The role that system integrators play will change. As well as designing and implementing NPNs, they may also be required to manage these networks for businesses who do not wish to retain the necessary expertise or resources in-house. In public areas (such as shopping malls, large entertainment venues, hotels, airport terminals, etc.), the neutral host has emerged to provide multi-operator access. The neutral host approach relies on OpenRAN technologies to operate a shared network solution, which is available to multiple MNOs. Regulatory authorities around the world have recognized this growing requirement for NPNs and have begun allocating dedicated and shared spectrum options for owners and providers.
The Future Looks Bright for the OpenRAN
An increasing number of governments and the wider industry are recognizing the importance that indoor coverage is destined to have, with various OpenRAN-related initiatives consequently being launched. The US government recently approved a bill to invest $750 Million in OpenRAN technologies over the course of the next decade, while in the UK the Knowledge Transfer Network’s 5G Supply Chain Diversification Strategy likewise aims to accelerate the development and deployment of open-interface solutions.
The global financial markets also seem certain that OpenRAN technologies will play a pivotal role in the 5G roll-out. As detailed in Figure 4, projections published by ABI Research expect global OpenRAN spend in public cellular networks will constitute an annual figure of $10 billion in the 2026/27 time frame, and will exceed traditional RAN spending by 2030 (reaching $30 billion by that time).
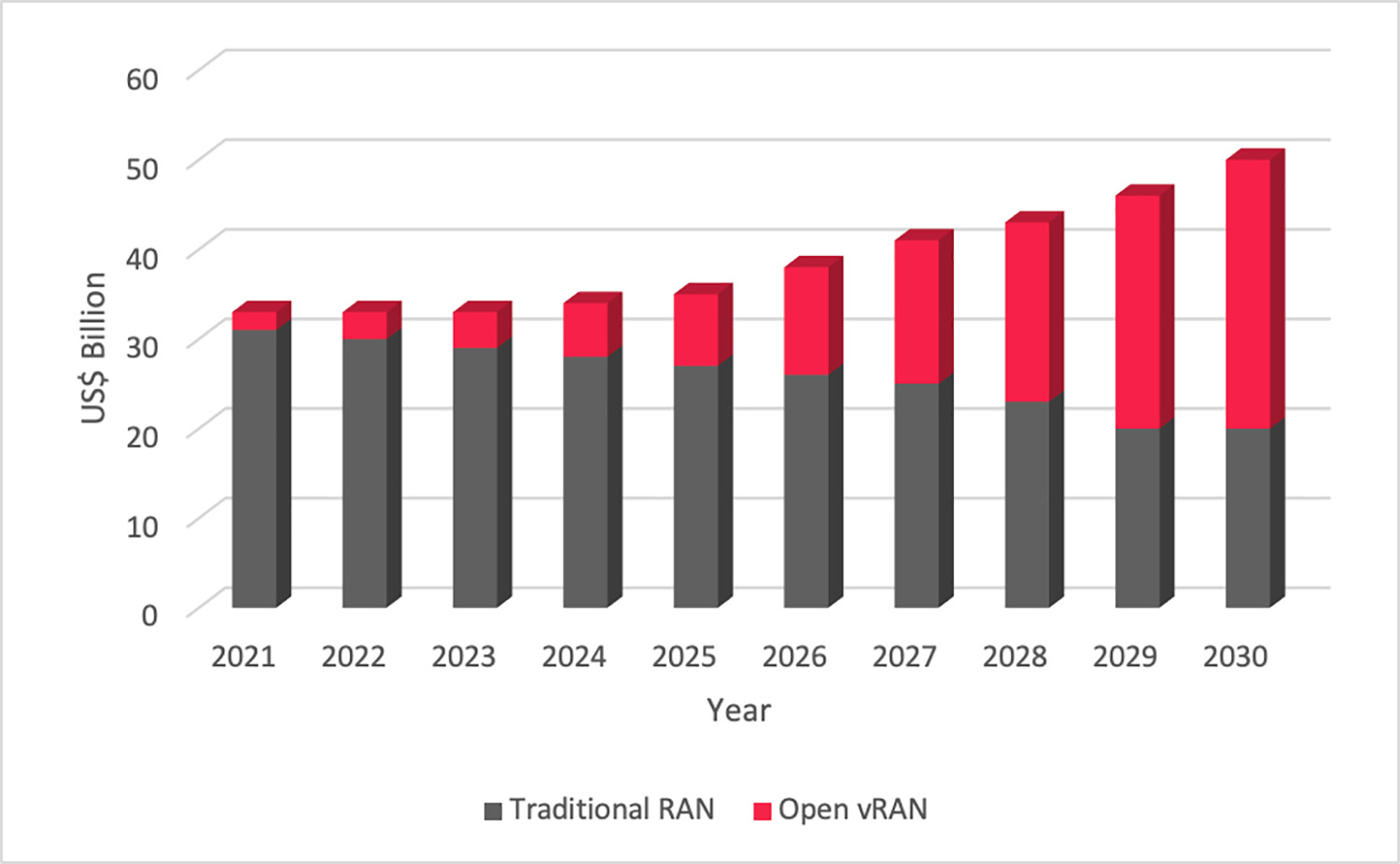
Figure 4: Public cellular spend - covering traditional and OpenRAN
4. Conclusion
As applications such as the IoT and industrial automation have driven the demand for wireless connectivity, having adequate indoor coverage has become an increasing concern. Through the advent of interoperable hardware and software solutions that are aligned with the OpenRAN ecosystem, there is huge scope to reduce the TCO associated with network infrastructure - and this will enable a plethora of new use cases to be explored.
Learn more about Benetel at https://benetel.com/
Learn more about the RAN550, Benetel’s OpenRAN RU for indoor deployment.
6G Activities in Germany
Authors: Frank H.P. Fitzek, TU Dresden; Holger Boche, TU München; Slawomir Stanczak, TU Berlin; Harris Gacanin, RWTH Aachen; Gerhard Fettweis, TU Dresden; Hans D. Schotten, TU Kaiserslautern
1. 6G Platform Germany
Mobile communications have unleashed a significant transformative force on society and businesses. Services have gone mobile and the smart phone has become an increasingly omnipotent companion. With 5G, this impact has extended to vertical industries - especially automation, mobility, logistics, and agriculture - where 5G is increasingly becoming a key enabler for efficient digitization.
With 6G, this trend is expected to affect almost all areas of society and economy, with an increased focus on people and their needs in addition to the vertical user industries. Humans will be supported by avatars and autonomous robots, digital twinning will allow increasing efficiency in mobility and production, new personalized medical applications and new types of human-machine interaction will improve health and increase safety, comfort, and – in particular – sustainability of our daily life.
Acknowledging the importance of 6G as future infrastructure for digitalization, the German Federal Ministry of Education and Research, the BMBF, launched a research initiative for 6G technology in 2021. The German 6G program will comprise several funding schemes.
A “Platform for Future Communication Technologies and 6G” (also known as the “6G Platform Germany” for short) acts as umbrella organization for the German 6G program. The 6G Platform Germany provides a platform for collaboration, networking, and coordination within the German 6G program. It is also the point of contact for external collaborations on a European and international level. Besides this organizational work and the liaison management, the 6G Platform implements several Working Groups that address topics of high societal importance and important technical topics requiring coordination.
Another part of the German 6G Program are four 6G Research Hubs: 6GEM, 6G-RIC, 6G-life and Open6GHub with the coordination offices being located in the German cities of Aachen, Berlin, Dresden/Munich, and Kaiserslautern. The projects started in August 2021 for an initial period of four years. They are canters of excellence targeting fundamental research questions in all areas relevant for defining a new generation of mobile systems including microelectronics, quantum technology, information theory, propagation, security and resilience, system engineering, architecture, software techniques, sensing, etc.
Figure 1
Collaborative industry projects for “research of holistic systems and component technologies for 6G mobile communications” including a 6G flagship project ensure that stakeholders from the telecommunications industry and vertical industries work together on the overall system design. This part of the 6G program aims to develop innovative solutions on all technology levels: material, component, microelectronic, modular and network level. IT security, software defined networking and artificial intelligence represent further areas of focus as cross-cutting topics. The participation of industry players will enable application-oriented development and the transfer of the research results into the international standardization and regulatory processes.
The 6G platform creates a structured space for networking of all partner involved in the 6G program. For this purpose, working groups are established to develop position statements, white papers or other deliverables. The working groups and their work assignments are defined by an industry-led steering committee. Four working groups targeting topics of societal importance are already established. Additional working groups will address system architecture, specific technical topics as well as the application domain. The four already established working groups are described below.
One of the 6G Platform Working Groups focuses on “Science Communication”. This topic is given particular importance within the 6G platform, since the involvement of all interested parties in the 6G vision process and the consideration of requirements of all stakeholder groups is of high significance for public acceptance. A dialogue process with civil and industrial stakeholder groups guarantees an iterative assessment of 6G vision statements and identified key functionalities. Content is prepared in a transparent, information and target group-oriented manner and made accessible via effective communication channels. Cooperative and participatory formats are the focus in order to reach both technologically inclined parts of the population as well as the group of those who have reservations about technology.
Sustainability and participation is the focus topic of another Working Group. Green ICT as well as 6G for sustainability will all its different aspects will be the focus of this group. With the increasing importance of mobile digital services in the areas of health, education and public administration, it is becoming essential to provide all citizens in urban and rural areas with mobile Internet access. Increasing digitization in businesses and the importance of digitization as a key technology for efficient sustainability led to further pressure to ensure comprehensive participation opportunities. To this end, a 6G system will combine network components ranging from traditional terrestrial devices to drones and satellites into a unified 3-dimensional network. Such 3D networks will provide "unlimited connectivity" through innovations such as organic 3D networking, dynamic shifting of network functionalities (radio access and core network), and dynamic control of information flows. A basic prerequisite for this is to support intensive cooperation between the two hitherto rather separate industries of mobile and space communications at various levels (technological, economic, regulatory, political). In order to develop largely harmonized and standardized solutions, the 6G Platform accompanies and moderates this cooperation.
The establishment of concepts as campus networks, Open RAN and “Reduced Capability” products are opening up great potential for innovations and new market opportunities for SMEs and start-ups. In a third Working Group, the 6G platform will therefore coordinate the identification of such potentials and the resulting new business models, provide mentoring for start-ups, and promote the establishment of a growing and innovative mobile ecosystem.
Building a harmonized vision on 6G is the focus of another Working Group. Here, a comprehensive and realistic vision for a future hyper-connected society is derived based on input of all 6G projects. In particular, mobility visions, smart cities, campus networks of the future, but also personalized medicine, e-government and novel human-machine interaction will be considered. The developed visions will support science communication, help to set technological priorities and also be a contribution to Germany's digitization agenda.
The partner organization of the 6G Platform Germany are Barkhausen Institut, Dresden, Fraunhofer-Institut für Integrierte Schaltungen, Friedrich-Alexander-Universität Erlangen-Nürnberg, Institut für Automation und Kommunikation e.V., Technische Universität Berlin, Technische Universität Dresden, Technische Universität Kaiserslautern, and Universität Bremen.
Link: www.6g-plattform.de
2. 6G-life - Digital Transformation and Sovereignty of Future Communication Networks
6G-life is one of the four 6G research hubs in Germany that addresses the question of future communication networks with respect to human-machine interaction in real and virtual space (metaverse). 6G-life offers new approaches to sustainability, security, resilience and latency and will sustainably strengthen the economy and thus digital sovereignty in Germany.
After the Neolithic and Industrial Revolutions, the digital transformation is one of the next great challenges facing humanity. For society, change through digital transformation offers completely new opportunities, but also raises questions: How will our children learn in the future? How will we shape our work? How will we receive medical care in old age and be cared for with dignity in our familiar surroundings? Even if the change offers a lot of potential and the societal need is obvious, society must be accompanied on this path. For the economy and industry, and thus for the productivity of our country, it is of enormous importance how this change is responded to. Due to the high speed at which the digital transformation is progressing, the economic-evolutionary pressure is also increasing enormously. It is therefore absolutely essential for business and industry not only to keep pace with this fast-moving change, but to actively shape it. After all, Charles Darwin's guiding principle that it is not the currently strongest but the one who best shapes change that will survive still applies.
Whether in private life or in business, the key to digitization is reliable, high-performance communications networks. For the Federal Republic of Germany, as well as for Europe, it is not only important to deploy future communications networks in time to support society and the economy, but it is also essential to exert a significant influence in research and development so that developments meet our requirements in terms of ethics, sustainability and economic activity. The latter comes under the heading of digital sovereignty. To this end, the Federal Republic of Germany has rolled out a stimulus package to promote research in the field of future communications networks under the term 6G. 6G focuses on humans and their communication and interaction with machines and virtual worlds, while the current 5G focuses on a network for machines.
In response to the call for proposals from the German Federal Ministry of Education and Research (BMBF) for 6G research hubs, the Technical University of Dresden (TUD) and the Technical University of Munich (TUM) successfully applied with the 6G-life research hub to (i) drive cutting-edge research for future 6G communication networks with a focus on human-machine collaboration, (ii) patent and standardize the research results worldwide (3GPP, IETF, ETSI, ITU, ACIA), (iii) secure digital sovereignty for the Federal Republic of Germany and (iv) support start-ups, SMEs and industry with innovative and sustainable concepts. In this context, the merger of the two universities of excellence combines the world-leading, mostly joint preliminary work of both universities in the field of (i) the tactile Internet in the Cluster of Excellence CeTI (www.ceti.one) , (ii) 5G communication networks, (iii) quantum communication, (iv) disruptive ideas in information theory, such as post-Shannon theory, (v) artificial intelligence methods, and (vi) adaptive and flexible hardware and software platforms.
6G-life has identified the following challenges for cutting-edge research: (i) Information transmission and computing are the keys to successful digitization. However, ever-increasing data volumes lead to higher energy consumption, which could deplete world energy production as early as 2040. 6G-life provides new approaches to sustainability, such as the post-Shannon theory, to decouple the relationship between data volumes and energy consumption as much as possible. (ii) Because of the various applications expected in human-machine collaboration (MMC), the communication platform must be kept highly flexible. However, this leads to new attack opportunities and, as a consequence, possibly to failures. Here, 6G-life will provide new concepts for security by design (quantum communication, information theoretic security, post-quantum cryptography and protocols) and for resilience by design (artificial intelligence methods to control in-network computing, resilience against denial-of-service attacks using coding schemes with common randomness and quantum communication). (iii) Current latencies are still too high for critical use cases. In-network computing has contributed significantly to reduce propagation delay, but at the same time added additional delays due to computation time. New approaches in compiler construction and for operating systems are needed here. Also, most sensors and actuators are still too slow. To speed them up, 6G-life will explore new materials. Nearly all of the network and data security mechanisms used to date cause delays. To maintain quality of service without sacrificing security, 6G-life will research and test new, fast methods to ensure privacy and resilience.

Figure 2: 6G-life – research team.
Involving about 60 professorships from both universities and more than 150 newly recruited researchers, national industry partners, a high-level international advisory board, and international collaborative projects in Europe, Asia, and the U.S., a 6G hub is being created that will have a global impact on the research landscape. Digital sovereignty will not be achieved through compartmentalization, but as a technology leader in global cooperation. In parallel, this hub will significantly stimulate industry and the start-up landscape in Germany through positive showcase projects and thus sustainably strengthen digital sovereignty in Germany. It is the goal to involve at least 30 start-ups through 6G-life in the first four years and to create at least 10 new start-ups. Testbeds for both use cases will drive research and economic stimulation.
6G-life has also set itself the task of making a contribution to society: specifically (i) to accompany the population through information events in the digital transformation (a partnership with the Federal Office for Information Security (BSI) and the Federal Office for Radiation Protection (BSF) will contribute to this), (ii) to create a sustainable support program for young scientists: in this field, (iii) make 6G-life knowledge available to industry, especially SMEs, and (iv) secure Germany's digital sovereignty with Kantian thinking (as opposed to George Orwell's dystopia).
Aspects that address societal change take on special significance due to the holistic approach taken by 6G-life. There are plans to include the humanities and social sciences in the research to address ethical issues and comprehensively counter potential concerns, such as radiation exposure. In this context, explicit public relations work is extremely important in addition to pure science communication. Both aspects are adequately addressed at 6G-life.
Link: https://6g-life.de/

Figure 3: Logo
3. 6GEM
Communication systems are the central nervous system of a digital economy and society. To be able to shape the digital future. The next-generation (6G) networks will face a massive increase in data heterogeneity generated by either human social behavior or intelligent machines where demands on communication resources are transient, unpredictable, and dynamic. Furthermore, commercial adoption of experience-rich (e.g., extended reality with low-latency and high-reliability) services for innovative and sustainable societies of tomorrow requires future networks with stringent security, advanced automation at the sub-ms scale, and decentralized open communication infrastructure.
Figure 4: BMBF 6GEM consortium
From August 1, 2021, the "6G Research Hub for Open, Efficient and Secure Mobile Communications Systems (6GEM)" project is funded by the Federal Ministry of Education and Research of Germany to establish Germany as a digitally sovereign key player in the development of next-generation mobile communication technologies. The 6GEM consortium partners are RWTH Aachen University, Ruhr-Universität Bochum, TU Dortmund University, the University of Duisburg-Essen, TU Ilmenau, Friedrich Alexander University, and four research institutions, the Fraunhofer Institute for Material Flow and Logistics, the Fraunhofer Institute for Integrated Circuits and Sensor Systems, the Fraunhofer Institute for High-Frequency Physics and Radar Techniques, and the Max Planck Institute for Security and Privacy.
The next-generation of mobile communication systems are blending with social activities through various human-centric applications/cyber-physical spaces. Thus, the space dynamically improves the social environment of humans. By utilizing digitally distributed data, the network senses human behavior to determine why a specific service is needed. To build such a vision, we require flexible Hardware, distributed Software, and human-centric Applications, which are strongly dependent on human interactions and environment interactions. Thus, there are multiple and dispersed data delivery points from the network to devices, while each device communicates with preferred physical links depending on the sensed environment. We cannot rely on incremental changes to the present information and communication technologies to build such a vision.
In the project, researchers design communication systems - from the hardware to the software - that offers a flexible network infrastructure. The aim is to guarantee resilient, adaptive system operation with extremely low latency and maximum reliability. Newly developed technologies will enable promising applications such as safer road traffic, port logistics, intralogistics, rescue robotics, and the digital operating room using digital twins. Research focuses on open, modular, and flexibly expandable 6G platforms that enable resilient and highly adaptive communication. The communication infrastructure is programmable by itself and becomes aware of how it is being used at the specific moment and what is likely to be required later. Simultaneously, communication devices need to share their data computing and storage resources and utilize distributed signal processing and artificial intelligence in real-time. Naturally, this research will include safety and security technologies as part of the network architecture from the design. Innovations for the planned mobile radio system are the new terahertz radiation, distributed computing resources in the network, and RADAR-based approaches for communication technologies. Furthermore, new approaches to artificial intelligence and machine learning complement the technologies mentioned. The goal is to incorporate knowledge from the physical layer and application processes into automated network diagnostics, troubleshooting, and management. The technologies will be integrated into a flexible 6G system consisting of software and hardware and demonstrated in different application areas. Thorough interdisciplinary and cross-location research cooperation the consortium will seek to establish the value of future 6G systems for highly relevant societal and industrial use cases, ranging from healthcare, robotics, production, logistics, and road traffic to show the potential of 6G in these areas (see the next illustration of technology development research areas).
One of the main objectives of this project is to establish advanced digital and technological sovereignty of the German research and development landscape. To this goal, we define and appropriately implement the open, efficient, secure and safe communication technologies through programmable platforms. The platforms will provide testing and validation opportunities for startups, SMEs and telecom vendors/operators, including complex standardization and security requirements for core network components. The technology focus will cover algorithmic, control and system integration, while networking and security will be covering the higher communication layers. Our goal is to play a crucial role in shaping, not just using, 6G technology development. Thus, our goal is to strengthen the national and international networking and cooperation between industry and academia.
The results of the 6GEM project are combined in a modular 6G platform that enables companies to evaluate their business models and products based on 6G at an early stage. The technologies developed in the project should form the basis for founding companies that will strengthen the future 6G ecosystem in Germany. The research work carried out in the project can also provide important building blocks for the future 6G mobile communications standard. In addition, there is a prospect that excellent specialists will be trained for the companies in the project partner's environment, thus enabling a faster transfer of knowledge to the economy.
Link: https://www.6gem.de

Figure 5: Logo
4. 6G-RIC
The 6G Research and Innovation Cluster (6G-RIC) is a research hub that aims to deliver scientific and technical foundations for the next generation of mobile communications (6G) across multiple technology disciplines, including radio access, core and fiber optic transport networks. This aim will be achieved through an interdisciplinary and coordinated collaboration of leading experts in communications engineering, computer science, mathematics and related disciplines. The focus is on research and development of a secure, flexible and open communications infrastructure as the basis for successful digitization in business and in other areas of society.
The greatest challenges for research arise from the radically increased requirements of the envisioned 6G applications expressed in terms of data rate, latency, reliability, and security. The required data rates per user of up to 100 Gbit/s and even beyond cannot be realized with 5G, particularly when several of the requirements need to be met simultaneously. This generally leads to notoriously difficult optimization problems with conflicting objectives. The integration of sensing services (keyword: “network as a sensor”) will result in new requirements that have to be met in addition to the communication requirements, ideally without impairing the quality of service of the communication. An essential prerequisite for satisfying the requirements of 6G applications is the availability of large bandwidths, which are not available below 60GHz. For this reason, the sub-THz band (up to 300GHz) must be exploited for mobile access, and this poses some major challenges for hardware, signal processing and wireless networking such as seamless handover in mobile scenarios. Due to strong Doppler effects, high channel attenuation and sensitivity to shadowing effects, the sub-THz frequencies are currently used only in stationary point-to-point communication scenarios.
Given long-term climate targets and the rapid spread of wireless communications, a profound reduction in energy consumption in future mobile communications networks is of particular social and economic importance. Therefore, a special attention must be devoted to the trade-off between the communication and sensing requirements of 6G applications on the one hand and the energy efficiency on the other. The goal must be to reconcile the expected explosive growth in data traffic, the integration of sensing services and the massive network densification with the demand for global sustainability and fairness. Similarly, user privacy and security must be a major design criterion to increase the social acceptance of future 6G technologies. With the advent of quantum computing, it is essential that the security of 6G networks will be built from the beginning on methods that are robust to quantum attacks.
There is little doubt that artificial intelligence (AI) will be one of the key technologies to address the mentioned challenges as we move from 5G to 6G. However, AI does not come at zero cost, and the gains achieved through its use must be put in relation to the corresponding effort and resources required. This will drive the convergence of information and communications technology to reduce the need for (wireless) communications in favor of local computing and processing. Indeed, in terms of energy efficiency, the statement "computing is cheap, communication is expensive" is more true today than ever before. Therefore, 6G-RIC envisions a holistic approach that expands the optimization dimensions of 5G by incorporating energy consumption, data acquisition and network computing, complemented by security by design, as an integral part of the overall network design (see Fig.)
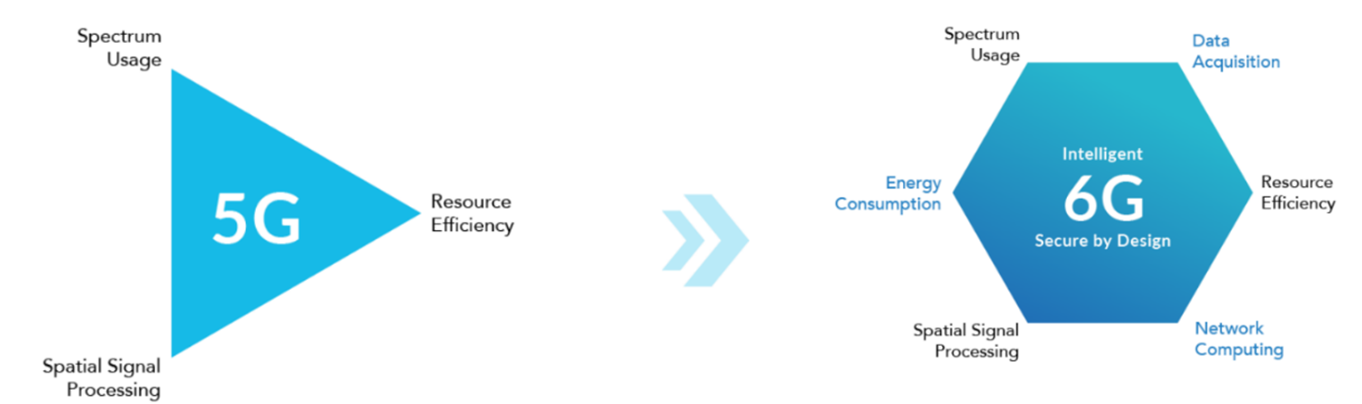
Figure 6: The expansion of the optimization dimensions in the transition from 5G to 6G.
6G-RIC is supported by an interdisciplinary and coordinated collaboration of a total of 32 research groups from 20 universities and research institutions and by more than 50 associated partnerships from science, industry and administration as well as an expert advisory board. The early involvement of government authorities (such as, e.g., the federal states of Berlin and Brandenburg) is intended to enable the test infrastructure to become permanent in order to support innovations in the medium and long term. The 6G-RIC is funded by The German Federal Ministry of Education and Research (BMBF) with 70 million Euros over 4 years.
6G-RIC envisions an ambitious, comprehensive and interdisciplinary research program that is centered on the following Technical Innovation Areas (TIAs):
- Opening up the highest frequencies for mobile applications through efficient transceiver technologies (Sub-THz Mobile Access);
- Research and development of intelligent reconfigurable surfaces for the adaptation and optimization of the radio environment (Intelligent Radio Environments);
- Convergence of radio sensing applications and communications (Network as a Sensor);
- Goal-oriented unification of data generation, transmission and use (6G Connectivity);
- Integration of communications security and data protection as part of the system design (Post-Quantum Security by Design);
- Virtualization of network components (Autonomous Convergent Networks).
Within each TIA, 6G-RIC will study and develop key technologies for future 6G communication systems and evaluate them in the form of technology demonstrations in the "real laboratory". Selected technology components will be brought together in overarching end-to-end demonstrators and presented in the context of selected 6G use cases. Currently, two potential use cases are under discussion: Mixed Realities and Mobile Robot Swarms. Whereas the first use case has very high demands on data rates and latency, mobile robot swarms require highly accurate sensing and tracking capabilities with real-time analytics.
In addition to the scientific objectives, 6G-RIC pursues the following strategic goals:
- Creation of an open network infrastructure that will enable SMEs and start-ups to develop and test 6G technologies.
- Contributing to the establishment of a new ecosystem based on disagreggation, virtualization and openness
- Improve conditions for spin-offs and collaboration with industry
- Contributing to the training and promotion of young talent
The modularization, virtualization, and openness promoted in the 6G RIC are important enablers for the creation of numerous opportunities for German and European industry to enter the global market, especially in the area of campus networks (i.e., "private networks"), which are increasingly attracting attention worldwide as drivers of innovation. The development of intelligent communication technologies for future campus networks, which sometimes have to meet highly specialized industry-specific requirements, is expected to open up a variety of new business models. In this respect, 6G-RIC will contribute to the creation of an open ecosystem for innovation that can withstand the ever-increasing dynamics of the communications and smart services markets.
Link: https://6g-ric.de/

Figure 7: Logo
5. Open6GHub - 6G for Society and Sustainability
The project "Open6GHub" develops a 6G vision for sovereign citizens in a hyper-connected world from 2030. The aim of the Open6GHub is to provide contributions to a global 6G harmonization process and standard in the European context. Societal needs (sustainability, climate protection, data protection, resilience, ...) are our most important 6G design goals.

Figure 8: Setup and Structure of Open6GHub
The Open6GHub will contribute to the development of an overall 6G architecture and end-to-end solutions. Main research areas are advanced network topologies with highly agile Organic Networking (ON), security and resilience, THz and photonic transmission concepts, sensing functionalities in the network and a privacy-preserving and energy-efficient processing of the generated data, as well as application-specific radio protocols.
The Open6GHub cares about its openness and seeks an early, open and interactive dialogue with the public. It is open to collaborations with industry and users and will implement OpenLabs and experimental fields for this purpose, and wants to foster an open innovation system by involving SMEs and start-ups.
The work of the Open6GHub is based on input of experts from all stakeholder groups, the advisory boards (technical and user board) and an analysis of new technological trends. Based on this input, the 6G design process will be guided by an iteratively refined common vision for a hyper-connected world in 2030+.
The developed 6G architecture tries to support all foreseeable upcoming application requirements as well some new concepts and functionalities that might become enablers for future not yet known services. For the implementation, the Open6GHub focusses on a selection of promising and new technologies and features. Some of them are described hereafter.
The availability of the necessary connectivity for tomorrow's digital society and economy requires new network architectures in which flying network nodes - from drones to satellites - together with terrestrial network components form a unified 3D communications network. The holistic approach required for this opens up space for innovations that go beyond the capabilities of the 3GPP 5G-NTN approach by exploiting the potential of flying network components much more comprehensively and deeply. Examples of innovations include: 3D ONs, dynamic relocation of network functionalities (radio access and core network) within the 3D network, and dynamic control of information flows. In the Open6GHub, the key technologies and core components required for this are being developed, and experimental platforms are being used to assess the feasibility of 3D networks.
For experimental evaluation, the Open6GHub develops a broadband test platform at 26 GHz that offers researchers and the industry the possibility to test at a very early stage new developments in the context of 6G, e.g., joint communication and sensing (JCAS), MIMO concepts, etc. At the final expansion stage, the demonstrator can provide up to 256 Tx and Rx channels each with a signal bandwidth up to 1 GHz (2 GHz if only half of the channels is used). It offers the replay and storage of raw data to directly start the investigations at the physical layer. In addition, real-time implementations on the FPGA are also in the scope of the project.
An ultra-high data rate wireless link operating at 300 GHz is foreseen for indoor applications like a data kiosk serving several mobile users with multi-Gbps download pipes. For that, the transmitter requires 2D beam steering, which will be achieved by combining an optical beam forming network chip with a frequency-scanning leaky-wave antenna array. Two possible hardware architectures for the receiver are foreseen including an in-phase and quadrature mixer approach, in which the antenna, low noise amplifier and mixer will be realized monolithically using GaAs technology. The second architecture is based on a Schottky barrier diode envelope detector which will result in a hybrid integration approach of InP and GaAs components. Based on first experimental results of using a hybrid setup of the foreseen architecture, a 300 GHz multi-user wireless supporting a data rate of 10 – 100 Gbps will be feasible.
Recently, it has turned out that JCAS becomes a key feature of future 6G networks. Hence, it is also one of the cornerstones of Open6GHub. JCAS is considered a deep integration of radio sensing capabilities into mobile network architecture reaching from radio access through network layers up to a quality controlled sensing service in public or private networks. In contrast to well-known and already established positioning services, JCAS will allow positioning, tracking and recognition of passive objects that are not equipped with a radio tag. A key advantage of JCAS is the re-use of radio and network resources of 6G. This increases resource efficiency and unlocks the whole access and network functionality to develop 6G a full-fledged distributed sensing network with adaptive and cognitive performance.
Resilience against failures and external threats is an essential property of future 6G networks. Thus, Resilience-by-Design is a key design criterion in the Open6GHub. Future 6G networks need to dynamically and predictively adapt, enabling resilient communication when necessary but allowing for resource-efficient high-performance communication when possible. In Open6GHub, we focus on such intelligent network adaptation to constantly mitigate known and unforeseen threats.
The idea of Organic Networking (ON) is a software-centric architectural approach that enables networks to continuously morph themselves to momentary localized user- and application-specific needs and available infrastructure resources, i.e. fully customized network provision at any location and any point in time. In ONs, distributed and heterogeneous infrastructures, converge into a coherent and resilient communication system including different access networks customized for campus and public networks. Beyond the 5G Service-based Architecture (SBA), the ON addresses the end-to-end service requirements with flexible dis/aggregation, orchestration, placement and morphing of network functions, based on the internet software services concepts.
An agile AI/ML driven self-aware network can adapt, optimize, learn and evolve itself. Intelligence can be gathered and processed anywhere in the network, ranging from the user terminal, network edge and central servers up to end applications by using a new highly customizable data exchange layer. It also means that contextual information (sensing, localization, ...) occurring on the network side is made available openly and transparently to third parties for the generation of innovative services. The same applies to making available network-side resources for AI, computing and trust. Mobile trusted multi-party AI services that need to use local context are likely to become possible only in this way.
The Open6GHub considers public and non-public networks. Here, there is a special focus on application fields with high requirements, such as those found in manufacturing and automation. Additional application areas that will be demonstrated include agriculture, logistics, new human-machine interfaces (HMIs), Smart Cities, and campus mobility solutions. Applications and technological solutions for 6G end-to-end communication system will be demonstrated and evaluated in several experimental fields with each partner, but can also be visited on dedicated OpenLabs which individually focus on a chosen application field of 6G like hyperconnected factory, smart and automated agriculture, ambient assisting living and tele medicine.
Link: www.open6ghub.de

Figure 9: Logo
Ten Experts “Get Real” With 5G in 2022
 …But don’t always agree
…But don’t always agree
25 February 2022
5G deployment is well underway – or so ‘they’ tell us.
The ‘conventional wisdom’ around 5G has been that it would take root at the enterprise level and drive business innovation first, then touch consumers though secondary applications and services (although not everyone agrees with that, as you’ll see below). 5G has been a lightning rod; it’s been over-hyped, met with resistance from the public, come up against spectrum availability and use issues, and slowed down by a pandemic of global proportions and resulting supply chain issues. No wonder 5G still does not feel “real” to many businesses and business owners.
Is 2022 the year when that will change? “Yes!”, say the experts. And, “not so fast” say others.
Could the convergence of 5G with other emerging technologies, such as AI, ML, and AR/VR usher in the next industrial revolution – Industry 5.0 - and be the game-changer that brings applications and use cases in healthcare, manufacturing, and agriculture and mining? It will do that and make strides in connecting the unconnected say most. But, not in agriculture, says another. Will 5G will aid the utility sector, or tax the electric grid? Yes!
We turned to experts from industry, government, and academia around the globe, who volunteer with IEEE Future Networks for their insights and perspectives on what about 5G might become “real” in the year ahead. And, although they aren’t all singing in unison, each of their predictions is based on a solid foundation of professional expertise and experience. Here is what they said:
Getting Real with 5G Deployment
 David Witkowski
David Witkowski
IEEE Senior Member
IEEE MTT-S Life Member
Co-Chair, Deployment Working Group, INGR (International Network Generations Roadmap)
Founder & CEO, Oku Solutions LLC
2022 will be the year that 5G enters the market in force, with new 5G radio access networks and 5G network cores coming online—it’s the combination of these two that enables delivery of true 5G service in a configuration known as 5G Standalone or 5G-SA.
We’ve seen some limited deployment of 5G-SA, including T-Mobile’s low-band and reclaimed mid-band networks, and Verizon’s Ultra-Wideband millimeter-wave network. Low-band networks provide wide-area coverage with limited throughput, and millimeter-wave networks provide high throughput but very limited range. Mid-band 5G delivers the best balance between coverage and throughput.
Carriers have added 5G to their existing mid-band networks, but these use the old 4G cores in a configuration known as 5G Non-standalone or 5G-NSA, and without a 5G core throughput is limited. Starting in 2022, 5G in mid-band will use 5G network cores. 2022 is also the year when carriers will complete the shutdown of their 3G networks, freeing up additional spectrum for 5G-SA networks.
That said, 5G could face deployment challenges in 2022 and beyond. Public anxiety about 5G, which is relatively new technology and therefore sometimes perceived as threatening, is showing up at the local government level in the form of opposition and appeals. In early 2022, the U.S. Federal Aviation Administration’s efforts to delay the launch of 5G in the C-band generated an international media firestorm. And some new features intended for 5G still need to go through the Third Generation Partnership Project (3GPP) candidate release process before carriers and device makers can adopt them.
Nevertheless, we’ve faced similar challenges with previous generations of cellular technology, and I have confidence that 2022 will be the year when 5G becomes real for many people.
The Real Deployment Challenge is Cost, Directly Impacted by Energy Usage
 Francesco Carobolante
Francesco Carobolante
Energy Efficiency Working Group, INGR
Principal, IoTissimo LLC
As highlighted in the Energy Efficiency chapter of the 2021 edition of the IEEE INGR (International Network Generations Roadmap), the viability of the services enabled by 5G and Beyond (5G&B) is directly tied to energy efficiency, which needs to be addressed across the whole ecosystem due to up-time requirements and reliability of the network. While the main development efforts at the system level have focused on spectral efficiency through the use of massive MIMO, the real challenge in the deployment of 5G&B technology is cost, which is directly impacted by energy usage – not just for CAPEX (equipment and installation), but also for OPEX (maintenance and energy cost).
This is true not only in urban environments, where local regulations constrain size and heat dissipation, but also in other locations: while edge computing increases energy demand, new safety concerns for the applications being promoted are forcing regulators to require extended power back-up capability. To overcome these initial headwinds, the industry is now focused on reducing costs through the use of highly integrated electronics, which will lead to a broader deployment.
One of the key capabilities that 5G brings forward is the ability to connect an enormous number of IoT elements, now forecasted in the trillions, thus enabling broad sensing and control applications, especially in industrial, robotics, agriculture and mobility sectors. Yet, the energy required to power them is often a challenge, since it is too expensive to wire them, and not sustainable to service them with batteries. Wireless power transfer is being touted as a solution to this issue, but it can currently only be utilized in limited scale, when other solutions are not viable, due to the poor efficiency of such an approach (around 1% for typical distances required). Advanced energy harvesting techniques are being developed, which are intrinsically more sustainable and scalable to the large number of devices being envisioned.
Energy Efficiency Takes the Front Seat to Start Working for the People
 Brian Zahnstecher
Brian Zahnstecher
Co-chair, Energy Efficiency Working Group, INGR
Principal, PowerRox
In 2022, we hope to observe a paradigm shift from recognition of the need for driving energy efficiency into a more pragmatic reality in which major stakeholders start to put far more resources into actions than words. The work of IEEE Future Networks has greatly facilitated by articulating concepts, terminology, and metrics (i.e. – Power Value Chain, Power Cost Factor, 5G Derate Factor, etc.) to enable a focus on global efficiency for the many stakeholders driving the development of hardware and network deployments in convergence with the utility grids that power them. The exciting advancements in the areas of distributed energy resources (DER), such as renewable microgrids, and grid-scale energy storage, all converging around autonomous energy grid management systems, bring us closer to a utopian, end-to-end network that self-optimizes from the micro to the macro levels.
We are also at another very fascinating crossroads in that union of communication systems and DERs driving the mitigation of the digital divide to grey the lines between pure economic gain and socioeconomic impact. The mutual benefits of investing in those on the less-connected end of the digital divide have been demonstrated, albeit at a smaller scale, but are certainly a promising step in the right direction. Powering previously disenfranchised or underdeveloped communities not only adds active cellular subscriptions and social media users but can optimize the utilization of energy while improving QoL (that is right, Quality of Life, not just Quality of Service or Experience, otherwise known as QoS/QoE). Everyone is a winner!
5G Becomes ‘Business as Usual’ in the Utility Sector
 James Irvine
James Irvine
Co-chair, Community Development Working Group, IEEE Future Networks
University of Strathclyde/Power Networks Demonstration Centre
2022 is a year where 5G will start to move from the realms of the possible into providing real ‘business as usual’ benefits to utility networks. As national deployments ramp up around the world, vendors start to provide private 5G solutions, and spectrum issues are eased through initiative like spectrum sharing and efforts such as the 450 MHz Alliance. Hence, 5G starts to become a viable solution to providing more ‘smarts’ in the distribution network at reasonable costs. Conservative minds in a very traditional industry – ‘if it ain’t broke, don’t fix it!’ - are also being focused by plans to turn off 2G and 3G networks over the next few years.
However, while the technology is there, there are still issues to be addressed, and key amongst these is resilience. Utility networks are used to five nines reliability, and mobile networks aren’t there yet. Power autonomy within the communications network is essential and must be improved. Where there is reasonable backup at the moment, it tends to be for earlier generation voice networks which are going away. Utilities expect communications to continue to work for up to seven days when mains power is lost, but experience from recent storms suggest 10-14 days might be required. Typical 4G sites last 30 minutes without mains power
A second major resilience issue is of the supply chain. There has been consolidation of the equipment supply chain, and use of 5G in Critical National Infrastructure has spurred governments to start defining who is able to provide equipment for certain applications. Combined with a trend to have greater vendor lock-in as the standards become more complex, the result is a squeeze that may still delay deployment.
2022 is the Year of Private 5G Networks; More Energy Efficient as Time Goes by
 Emil Björnson
Emil Björnson
IEEE Fellow
Working Group on Energy Efficiency, INGR
Professor of Wireless Communication, KTH Royal Institute of Technology, Sweden
Despite the hype around the emerging 5G enterprise market and its potential of reaching $700 billion by 2030, the initial focus of 5G is on the consumer market. Its data traffic grows by 40% per year and has been the main driver for evolving the network infrastructure in past decades. The Massive MIMO technology that is at the heart of 5G base stations changes the game when it comes to network dimensioning. The traffic capacity of a base station used to be a fixed resource to be divided between the customers. However, with a paradigm shift in network dimensioning, 5G capacity grows with the number of simultaneously active customers. It is like having a party where the cake grows with the number of guests, so that everyone gets (almost) an entire cake!
This paradigm shift is enabled by the highly directional transmissions from 5G base stations, which are adapted to each customer’s physical location. Current 5G networks are rather empty in the sense of only serving 1-2 users per millisecond, but they are fully capable of managing 5-10 users at the time, each being assigned the entire spectral bandwidth. The implication is that 5G networks will become increasingly cost and energy efficient as time goes by. We will get more bits per second while spending nearly the same power on the infrastructure side.
The spare capacity in 5G networks is also the enabler for new enterprise services. 2022 is the year when private 5G networks will appear, created through virtualization in the telecom operators’ 5G networks, so that enterprises can outsource connectivity delivery and start to gain access to premium wireless services for demanding use cases.
5G in 2022 … Another Year of More Pain Than Gain
 Rod Waterhouse
Rod Waterhouse
IEEE Future Networks, Tech Focus Editor-in-Chief
CTO, Octane Wireless
Sorry for sounding so melodramatic but all the signs are indicating 2022 will be another year of slowly catching up to over-the-top hype created several years ago. What we will see this year is more and more engineering development and roll out of lower spectrum (less than 6 GHz) 5G equipment and the pushing off the more ‘paradigm shift’ technologies into the ‘beyond’ 5G space. This in and of itself is not a bad thing, for it shows maturity of a system. An appropriate analogy from the recent Australian Tennis Open, would be that it’s time to work on your foot work, court coverage, and high percentage defensive shots rather than your overhead smashes, cross court winners, and aces down the tee.
Things to watch this year in the 5G world is the rural coverage fight; there seems to be a lot of players in this area, and I believe we will see a few either drop out or consolidate. For example, I haven’t heard too much on High-altitude Platforms recently; a great technology but maybe looking for an application? Smart agriculture is another compelling topic especially given the climate interest, although a lot of the goals of this may be achievable with WiFi (or equivalent) and, so, smart agriculture may not be considered a 5G application in the future.
5G Deployment and Security
 Ashutosh Dutta, Ph.D.
Ashutosh Dutta, Ph.D.
Fellow of the IEEE
Co-Chair IEEE Future Networks Initiative
Chief 5G Strategist, Johns Hopkins University Applied Physics Lab
In 2021, deployment of 5G technologies has largely been constrained due to factors including the prevailing pandemic, lack of interoperability and testing among vendor products, limited availability of open-source implementation, the absence of compelling use cases due to lack of accessibility to advanced testbeds, and lack of a compelling emerging application that would help drive the evolution of the network, and, finally, spectrum interference. As well, perceived security threats for 5G networks at various parts of the network including supply chain security have slowed down widespread deployment of 5G networks as operators weigh the risks associated with security threats and delay their deployment until proper security mitigation techniques are developed to take care of the risk. Thus, the gap between standardization and deployment has also widened.
While 5G deployment is still in its infancy, the research community has already started conducting research for the next generation, 6G being the next cellular evolution. Various SDOs and standards bodies around the world including 3GPP, ITU, IEEE Future Networks, the Next G Alliance, TSDSI, 6G Flagship projects, the Horizons project, and various other initiatives in Europe, China, Japan, and Australia have started delving into research to fill the gaps of 5G and augment 5G technologies.
Adversity during the pandemic has also led to the innovation of new use cases and applications that could exploit various 5G technologies and help bridge the Digital Divide. As 2022 unfolds, 5G technologies will not be limited to telecom operators, but will be further exploited to support verticals including first responders, public safety, tactical networks, defense, agriculture, entertainment, eHealth, and smart cities, to name a few. Enterprises will take advantage of 5G enablers, namely Open RAN, Edge Cloud, Software Defined Networking, Network Slicing, Virtualization, Orchestration, and AI/ML to customize their private 5G networks and support variety of applications including Ultra Low Latency, Enhanced Mobile Broadband and Massive Machine Type Communications. Support of heterogeneous access and HETNETS will be a norm than exception. This will lead to the co-existence of private 5G networks and Wi-Fi networks. New techniques will be developed to provide seamless priority services and quality of services as the end user moves between heterogeneous access networks. Operators will continue to take advantage of disaggregation of network functions, virtualization, orchestration, and closed loop automation and will implement Open RAN solutions to make their RAN programmable. The vendor and operator communities will continue to embrace open-source consortiums such as the Linux Foundation, the Open Networking Foundation, OpenAirInterface, O-RAN, OPNFV, and Free5GC among others, giving rise to faster deployment.
While 5G technologies have taken care of many of the security issues in 4G/LTE, there are additional security challenges and opportunities introduced by various 5G enablers that make the network programmable, scalable, and resilient. In order to deploy a secured 5G network, mitigation techniques need to be implemented to address the security issues presented by each of these enablers. Hence, there will be an effort by the security and monitoring companies to develop new tools and controls to mitigate the risks associated with these 5G enablers. These tools will implement AI/ML techniques and federated learning algorithms to devise predictive security solutions for zero trust type networks. Customized security architecture will be designed to support a variety of applications while maintaining a tradeoff between security indicators and key performance indicators. Collaboration among various SDOs, R&D consortiums, government, and academia will act as a catalyst towards research for next generation networks resulting in new standards, roadmaps, testbeds, use cases, and advanced proof-of-concept.
5G Security in 2022 - Cyber Resilience, End-to-End Security, Resilience-by-Design
 Eman Hammad, PhD, SMIEEE
Eman Hammad, PhD, SMIEEE
Co-Chair, Security Working Group, INGR
Assistant Professor, Texas A&M University – Commerce@RELLIS>
Following major cyber incidents and disruptions in 2021, systems security and resilience will continue to gain more invested focus from vendors, service providers, and end-users, especially commercial clients. With an ever-evolving and changing threat landscape, priority will be given to ensuring cyber resilience, end-to-end security, and resilience-by-design. This is mainly shaped by future networks and connected systems’ evolution to be more complex, adaptive, dynamic, and autonomous.
Cyber resilience and converged IT/OT/IoT operations will become more mature enabling more intelligent protective and active mitigation operation on different system layers. We will see advancements in enhancing cyber-resilience by integration of trusted closed-loop security automation that’s context-aware and considers the composite state of the system, types of applications, and operational and security KPI requirements.
Future networks rely heavily on ML/AI to enable its operation. While cyber risks and threats of ML/AI algorithms are acknowledged and somewhat better understood, specific recommendations and security controls remain lagging and in research phases. More development will be seen in model verification, reliability, and trust models, in addition to data quality measures.
Focus on end-to-end security architectures will increase in response to recent significant cyber risks and incidents targeting the supply chain. Efforts incorporating trust-based frameworks and platforms to verify and authenticate entities within an end-to-end architecture will gain maturity (attestation, zero-trust, Software Bill of Materials), and we could be seeing example reference security architectures piloted. This would be a necessary step to ensure gaps in supply chain security are managed and mitigated. Moreover, the next-generation evolution of smart grids, intelligent transportations, public safety, and others will require strict KPIs striking critical tradeoffs between security, reliability, and operational performance. URLLC use-case implementations outside of private 5G networks will gain some traction with some integrated security controls.
Industry 5.0: When Human and Robots Collaborate Towards the Next Industrial Revolution
 Halima Elbiaze
Halima Elbiaze
Technical Program Committee Co-Chair, IEEE Future Networks World Forum
Full professor, Computer Science Department, University of Quebec at Montreal, Canada
Industry 5.0 is a human-centric solution where robots collaborate with humans to enable personalizable autonomous manufacturing. Cobots can take repetitive and labor-intensive tasks while humans focus on perception-driven decision making. Together with IoT, digital twin, and AI, 5G and beyond (5GB) technology will play a pivotal role in enabling Industry 5.0. The 5GB radio access network infrastructure is designed to support a massive and dense number of devices as in the Industry 5.0 use-case where millions of sensors, hardware elements, and robots operate. 5GB is finally finding its killer use-case that includes many applications, along with increasing bandwidth requirements, stringent latency constraint and resource-greedy AI capabilities. Many applications of Industry 5.0 are tailored considering sustainability aspects including environmental, economic, and social sustainability such as intelligent healthcare, supply chain management, smart education, and smart agriculture.
Despite the promising ability of Industry 5.0 to transform several industrial segments, there are challenges that need to be tackled to achieve its full potential. For instance, one inherent characteristic of Industry 5.0 ecosystems, that brings a potential challenge in processing and handling, is data heterogeneity and volume. Furthermore, the stringent latency targeted (2 ms network delay and 1 ms jitter) by industrial control systems has been recognized as computationally prohibitive in large-scale networked systems. Thus, resource allocation needs a paradigm shift to a closely coupled control, computing, communication, and caching infrastructure where all devices and tiers cooperate towards some specific goals. Goal-oriented communication has the potential to alleviate the complexities of networked control systems by recognizing that communication is not an end, but rather a means to achieving some goals of the communicating parties.
5G: As Critical to Progress as Electricity or Water
 Sujata Tibrewala
Sujata Tibrewala
Co-chair, Edge Services Working Group, INGR
Worldwide developer community manager, oneAPI
5G is of one of the most ambitious technology disruptors if implemented well. Its open interfaces are designed to be accessible for inter-platform and cross vendor development, and hence it reduces barriers to entry and opens doors to smaller vendors and regions, which have traditionally remained unconnected. However, all is not roses and there are bottlenecks to its adoption. For example:
- Use of mm waves and Giga Hz spectrum has not been used before, hence its impact on human health is making people skeptical.
- Its requirement to be vendor- and technology-agnostic goes against the interest of major carriers who are also implementers of 5G, since they have historically protected their interests by providing vertically integrated solutions.
In conclusion, the state of 5G adoption creates a sense of déjà vu. In the early 2000s, industry built excess network capacity in anticipation of wide-scale e-commerce adoption. We are living in the age of e-commerce eating up brick and mortar stores today, but it lagged the industry prediction by at least 10 years. It is hard to say how long it will take for 5G to become mainstream, but we know it is inevitable, since it will level-set the playing field for everyone on this earth, since today connectivity is as critical to progress as electricity or water.
Looking Farther Ahead
This brief look into the coming year are the insights of the volunteers of IEEE Future Networks who in their day jobs work as telecommunications strategists, consultants, advisors, professors, developers, and more, with specific areas of expertise.
To see even farther down the road, many of these volunteers lead Working Groups contributing to the INGR, a living document creating a predictive model for communication networks looking as much as a decade into the future. Made up of 14 chapters focused on issues across the plane of establishing, deploying, and applying emerging telecoms networking generations, the INGR:
- Anticipates applications evolving from converged network generations and emerging technologies.
- Detects inflection points that may arise.
- Serves as both an investigator and aggregator of challenges and solutions.
The INGR is a resource that serves as a unified understanding of where future communication networks are headed. Updated versions of the INGR are released annually. INGR chapter overviews are available at no cost and for those who sign up for the IEEE Future Networks Technical Community full roadmap chapters may be read in their entirety.
7 Experts Cast Their Visions for 5G and Beyond in 2021
 19 January 2021
19 January 2021
Forecasting what might come about over the course of the next 12 months in a space as diverse and dynamic as 5G would be challenging at any given moment. It seems it would have come to prove downright futile ahead of the year in which COVID-19 dominated practically every aspect of life around the globe.
And, yet, looking back on the 5G forecasts of IEEE Future Networks subject-matter experts from January 2020, the “predictions validated fairly well despite COVID-19 emerging as a major socio-economic disruptor less than two months after we published the article,” reflected David Witkowski, Chair, Deployment Working Group, International Network Generations Roadmap, IEEE Future Networks, and Founder and Chief Executive Officer, Oku Solutions LLC.
Added Brian Zahnstecher, Chair, Energy Efficiency Working Group, International Network Generations Roadmap, IEEE Future Networks, and Principal, PowerRox: “If anything, then I feel COVID-19 has greatly accelerated the exponential increase in network traffic/demand even beyond the pre-COVID-19 predictions. This means pretty much all of the concerns expressed for 2020 are that much more salient.”
Again for 2021, we return to experts from across IEEE Future Networks for insights and perspectives on what the year ahead might hold for 5G.
Realization of 5G Value Through Global Pandemic Response
David Witkowski, Chair, Deployment Working Group, International Network Generations Roadmap, IEEE Future Networks, and Founder and CEO, Oku Solutions LLC
Dramatic socio-economic effects from efforts to contain the pandemic and reduce COVID-19 infections have manifested impacts on telecommunications in both positive and negative ways.
Citizens Broadband Radio Service (CBRS)—sometimes called “Private LTE” or “Private 5G”—as an in-building technology will be delayed until people again can start occupying buildings en masse. However, CBRS has proven useful in outdoor deployments for community broadband, and we expect this to continue in 2021.
Work-from-home, distance learning, and a shift to telehealth emerged as tools to contain pandemic spread, resulting in dramatic shifts in cellular voice and data usage patterns. Students without home broadband, or with inadequate home broadband, were given hotspots for school use, but, without good 4G coverage, hotspots are not useful. The increased density of simultaneous users during work/school hours in housing areas placed huge stresses on the 4G network, which resulted in many cities asking carriers and operators to speed up their 4G and 5G deployment efforts, a trend we expect will continue in 2021. In some cases, these users will be served by private networks using CBRS, Wi-Fi, and other unlicensed technologies.
The need for pandemic response tools that minimize human interactions creates an increased need for augmented and/or virtual reality (AR and/or VR) technologies. Likewise, the pandemic drives a need for Industrial Internet of Things (IIoT) (e.g., automation systems that reduce the amount of time a person needs to be in close quarters with other people). Both are enabled by 5G’s ultra-reliable low-latency communication (URLLC) and massive machine-type-communications (MMTC) capabilities, so we predict strong interest in finalizing those in technical standards.
In general, we predict that the value of 5G will be realized not only in smartphone and device connectivity but also in the application of technologies to address challenges we face as the world continues to adapt to the pandemic.
A More Serious Call to Action on Energy-Efficient Optimization
Brian Zahnstecher, Co-chair, Energy Efficiency Working Group, International Network Generations Roadmap, IEEE Future Networks, and Principal, PowerRox
2021 will be the year we stop paying lip service to energy-efficient optimization and start taking it more seriously as a critical call to action because there may be no path forward otherwise. Our Energy Efficiency Working Group (EE WG) has greatly expanded upon the original risk factor of The 5G Energy Gap (5GEG) and generated complementary concepts to help isolate and address related impacts to economics (i.e., The 5G Economic Gap) and even tie to socio-economic factors (i.e., The 5G Equality Gap). More importantly, these concepts have morphed into metrics for assessment and given way to an entire framework for modeling, simulating, and assessing complex chains (also known as “Power Value Chains” or PVC). The key metric of 5G Derate Factor, or 5GDF, is the culmination of all aforementioned factors to simplify into an overall, network metric to be reported and optimized by the framework, which we refer to as the “5G Systems of Systems” (SoS). Any stakeholder can convert their network area of focus PVC into our “universal currency” of energy and chain black boxes together to perform both static and dynamic analyses. The static analysis is necessary to assess a given configuration and identify energy bottlenecks. The dynamic analysis provisions for dynamic optimization of EE for the system as a whole and takes desired operating/financial performance targets to determine a 5GDF and provide recommendations for how to maximize that value for optimal EE performance and, therefore, energy utilization.
Strong Rollout and Penetration of Lower-spectrum 5G Network Globally
Rod Waterhouse, Co-chair, Publications Working Group, IEEE Future Networks, and CTO, Octane Wireless
Obviously, no one in 2019 could have predicted the huge curve ball that COVID-19 would throw in 2020. To the credit of the many people working in 5G technology-related areas, there was still substantial progress made in the 5G sector—albeit probably not as much as one had hoped to see. One impact of the virus was the strong push for the realization of virtual medical care.
So, my predictions for 2021? Really much of the same that I predicted last year (I know this sounds repetitive), with a strong emphasis on the rollout and, therefore, penetration of the lower-spectrum (less than 6 GHz) 5G network throughout the world. I believe the application areas of interests that I mentioned last year are still going to be relevant and intriguing to watch as 2021 unfolds, with the addition of what role high-altitude platforms (HAPs) may play in our future networks. 2021 promises to be an exciting year for 5G.
Expedited 5G Rollout to Support Applications Driven by Pandemic Needs
Ashutosh Dutta, Co-chair, IEEE Future Networks, and Senior Scientist, JHU Applied Physics Laboratory, Chief 5G Strategist and ECE EP Chair
The aftermath of the pandemic will be a key factor in determining a surge in various new types of activities around the world in 2021. These include virtual meetings, virtual conferences, remote education, online shopping, telehealth, and streaming, among others. Hence, there will be development of a series of new emerging applications to support these activities. These activities will result in a surge of both signaling and data traffic in the network. This surge in traffic from billions of end devices will result in a potential security risk for both data in transit and data at rest. In order to support the surge in traffic resulting from these applications, it is important to design networks that are flexible and resilient and will be able to scale out and scale down on demand. At the same time, it is important to have proper security controls in place to detect and mitigate various types of denial-of-service attacks. As a consequence, operators will need to augment their networks with various 5G enablers such as software defined networking (SDN), network function virtualization (NFV), edge cloud, cloud radio access network (RAN), and network slicing. Closed loop automation and orchestration will play a central role to make the network more resilient to support the surge in traffic. Closed loop orchestration in conjunction with security function virtualization and dynamic service chaining will be deployed to take care of denial-of-service type attacks in the network. Artificial intelligence (AI)/machine learning (ML) will play a big role to enable predictive security and stop the zero-day type attacks. AI/ML will also play a crucial role in placement of these control loops in the network. In order to make RAN more scalable and flexible, open RAN solutions will be deployed. There also will be a push toward private 5G networks. Thus, 5G deployment will be expedited across the world in order to support the applications caused by the pandemic.
Pervasive Connectivity Fabrics to Support Transformations Driven by COVID-19
Kaniz Mahdi, founding co-chair, Systems Optimization Working Group, International Network Generations Roadmap, IEEE Future Networks, and Vice President of Advanced Technologies, VMware
- 2020 was anticipated to be a transformational year for telco, with 5G expected to revolutionize the way we live, work, and entertain. It turned out to be transformational, indeed—COVID-19 being the key forcing function. COVID-19 will continue to dominate the scene through the first half of 2021, but behavioral transformations led by COVID-19 are here to stay, e.g., talent reimagined with distributed workforce, school reimagined with customized curriculum, and entertainment re-imagined with home-theatres, drive-in theatres, and e-sports taking a permanent place in our lives.
- We can expect expedited 5G deployments, enabling pervasive connectivity fabrics to underpin sustainable distributed operation of the transformations led by COVID-19 and previously outlined.
- We can expect the rise of edge computing driven by the behavioral transformations drastically reshaping consumer traffic patterns, as well as a high degree of process automation required to sustain such operations, resulting in “elephant flows” too costly to carry over long-haul networks.
- Extended reality (XR)—AR/VR/mixed reality (MR)—finally will become mainstream, as an essential user interface (UI) tool to enhance user experiences driven by sustainable COVID-19 transformations.
- AI will continue to dominate the research scene, with larger emphasis on brain machine interfaces, another manifestation of sustainable COVID-19 transformations.
- Bots everywhere—from consumer homes to manufacturing plants to shopping malls to healthcare facilities.
- Cloud providers will continue to extend their private backbones, capturing the bulk of the traffic shares getting closer to the user (e.g., Google Stadia).
- We can expect the advent of non-terrestrial networks (low-orbit satellite systems such as SpaceX Starlink) initially to bridge the digital divide, as well as continued tech advancements toward adoption with the autonomous-vehicle industry.
Cell-free Massive MIMO as Research Focus and Major System Architecture Change
Webert Montlouis, Co-chair, Massive MIMO Working Group, International Network Generations Roadmap, IEEE Future Networks, and Chief Scientist, Applied Physics Lab, Faculty, ECE, Johns Hopkins University
Cell-free massive massive-input, massive-output (MIMO) will see a lot of activities in the research community. The cell-free massive MIMO architecture will bring new ideas and ultimately drive innovation in other parts of the system, which will have significant importance for 5G and beyond. Although the approach can be seen as user-centric, it is expected to bring considerable improvements to the wireless network infrastructure. This architecture will be a driving force to meet the needs of the IoT in years to come. The cell-free concept will evolve into a major system architecture change that will drive a system partitioning and ultimately affect the edge and cloud computing. Some of the key areas will be:
- Spectral efficiency.
- Beamforming.
- Power-optimization techniques.
- Resource allocation.
- System partitioning in a cell-free massive MIMO architecture.
- Edge-computing architecture and cell-free massive MIMO.
- Cloud computing and cell-free massive MIMO.
- Load balancing to achieve energy efficiency and maintain latency requirements as the number of antenna elements increases.
Boundary-breaking Dialogue Among Electromagnetic-Spectrum Stakeholders
Alexander Wyglinski, Co-chair, Community Development Working Group, IEEE Future Networks, and Professor of Electrical Engineering and Robotics Engineering, Electrical & Computer Engineering, Worcester Polytechnic Institute
- During the next 12 months, expect some exciting and important dialogue between two major electromagnetic-spectrum stakeholders who do not normally communicate with each other: the emerging wireless-technologies community (e.g., 5G/6G and Wi-Fi 6) and the radio-science community (e.g., radio astronomy, GEO remote sensing, and radar). With the spectrum landscape experiencing significant flux—and as new wireless technologies progressively utilize frequency bands located close to spectrum allocated to radio science applications—these discussions are a necessity, in order to mitigate radio frequency interference (RFI) and enable sustainable spectral coexistence.
- The COVID-19 pandemic has significantly accelerated society’s move to an online format, including education, healthcare, and employment. This online way of life requires reliable broadband connectivity, and this pandemic has exposed the large digital divide that currently exists around the world between those who possess enough bandwidth to support their needs and those communities who are underserved or unserved. What we will see in 2021 is a significant effort across government, industry, and academia to bridge that digital divide, by developing broadband connectivity solutions that can reach these underserved/unserved communities, which are mostly located in rural areas with limited network infrastructure. Although part of this effort will focus on rolling out fiber to these communities, there also is an exciting opportunity to employ 5G technology tailored to the specific operating environment to achieve reliable broadband connectivity. However, bridging the digital divide cannot be achieved solely with technology. It also will require the help of other stakeholders, such as utility companies, community leaders, politicians and regional government, and economists. This is very much an interdisciplinary problem, but 5G technology is a game changer.
- 5G security and privacy will continue to be a major topic for the communications sector in 2021. Given how quickly 5G is being rolled out and assuming an ever-important role in supporting our society’s information needs, there is growing concern these very complex networks continue to be vulnerable to cyberattacks. We will see large-scale investment in activities related to securing the 5G network from threats introduced via a compromised supply chain, as well as the incorporation of untrusted hardware into the 5G infrastructure. Additionally, as 5G technology gets blended into the existing telecommunications infrastructure consisting of 4G and 3G cellular networks, the intersections where these technologies meet will be prime targets of attackers. Although the identification of these vulnerabilities can really be performed using actual 5G hardware, 2021 is experiencing significant activity in the construction of realistic 5G testbeds to examine this technology more closely, understand its behavior, determine threats, and provide a basis for the development of solutions to harden this increasingly vital infrastructure.
IEEE Future Networks invites participants in all aspects of current and future connectivity globally into collaboration on enabling the historic transformation promised by 5G and beyond for the benefit of all. Learn more about IEEE Future Networks.
Foundational Security Capabilities
 IEEE Future Networks Podcasts with the Experts
IEEE Future Networks Podcasts with the Experts
An IEEE Future Directions Digital Studios Production
5G Security, Part I: Foundational Security Capabilities
In this episode, we bring you Part I of a two-part podcast on 5G Security. In Part I, our experts discuss foundational security capabilities, and in Part II the focus is on use-cases, including device and application security.
The digital transformation brought about by 5G is redefining current models of end-to-end (E2E) connectivity and service reliability to include security-by-design principles. These principles are necessary to enable 5G to achieve its promise. Achieving 5G trustworthiness necessitates the importance of embedding security capabilities from the very beginning while 5G architecture is being defined and standardized. Security requirements need to overlay and permeate through the physical, network, and application systems layers of 5G, as well as different parts of an E2E 5G architecture, including a risk management framework that takes into account the evolving security threats landscape. The Security Working Group within the International Network Generations Roadmap follows a taxonomic structure, differentiation 5G functional pillars, and corresponding cybersecurity risks.
View the International Networks Generations Roadmap page with Executive Summary, and options for viewing the Security Chapter.
Subject Matter Experts

Ashutosh Dutta
Co-chair, Security Working Group, International Network Generations Roadmap.
Co-chair, IEEE Future Networks Initiative
Senior Scientist, Johns Hopkins University Applied Physics Lab.

Eman Hammad
Co-chair, Security Working Group, International Network Generations Roadmap
Industrial and IoT Security Specialist in Cybersecurity & Privacy, PwC Canada
With Brian Walker of IEEE Future Directions Digital Studio
Click here to listen.
Click here to download.
Subscribe to our feed on iTunes, Google Play, or Spotify
Podcast Transcript
Brian Walker: Can you tell us about 5G Security and why this generation presents a unique set of risks?
Ashutosh Dutta: 5G is different than previous generations in many ways. The previous generations can be categorized as 1G, 2G, 3G and 4G. Previous generations of network, they mostly focused on bandwidth intensive application. On the other hand, 5G networks not only focus on high-bandwidth type applications, but also focus on massive sensing and ultra-low-latency type applications. So, in order to support that, there is a need to design into an architecture, a network that's flexible, adaptive, and scalable enough to react to the changes in the network quite rapidly and efficiently. And thus, 5G has adopted many new technologies in various parts of the network. That includes changes in the radio access network, such as new radio, MIMO, millimeter wave in the core network, separation of user plane, control plane, service plus architecture, densification of cells, entities like edge-cloud, software-defined networking, network slicing, device-to-device communication, and IoT, etc. So, security requirements for 5G do need to overlay and permeate through different layers of 5G systems, including physical, network, and application, as well as different parts of end-to-end 5G architecture. And that will also include the risk management framework, and take into account the evolving security threat landscape. So, while the enablers bring various benefits and features, they also increase the threat landscape due to the introduction of these new enablers or technologies. For example, the additional SDN/NVF components and network functions, they increase that threat attack surface, and expose the end-to-end system to additional cyber threats. Some of the security risk that are pertaining to 5G may include network slicing threats, such as denial of service to other slices, or sites and other attacks at core slices. And we find, for example, when a certain slice is dedicated to a specific critical set of applications, such as emergency applications. So, all-in-all, the 5G network, although it includes a lot of features and adds some enablers, it also increases the threat landscape by posing unique sets of risks.
Eman Hammad: Just one thing on the last point you mentioned, when 5G evolved to carry more of the critical and more of the cyber physical applications and use cases, such as smart cities, transportation, energy systems, these kind of risks that might hinder the infrastructure will have a serious impact on where 5G is trying to enable the applications, specifically for such use cases. So, we're looking at a very different landscape, because of all the pieces that build the 5G system.
Brian Walker: What are the additional security pillars in 5G ecosystems?
Ashutosh Dutta: When you look at the 5G ecosystem, basically looking at end-to-end, you have a device, you have a radio access network, you have edge-cloud, you have the core network, and you also have applications. And if I look into the different pillars, from an end-to-end perspective, these pillars enable 5G features, right? But at the same time, we're also looking into the risks that are associated with pillars, and I can just name a few. To start with cloud-RAN security, SDN controller security, proactive security analytics, virtualization security or hypervisor container security, orchestration security, network slicing security, Open Source security, security function virtualization and faster authentication. So, these are some of the additional components where we have to look mainly at what are the additional risks, those are provided by adding these new 5G enablers. For example, if you have an SDN controller that gives you the programmability and flexibility, adaptability on the network, but at the same time, there are additional risks on the SDN controller. If the SDN controller is under attack, or this configuration gets changed, or somebody hacks into the SDN controller through a northbound API or southbound API, the whole programmable part becomes completely contaminated. So, instead of stopping bad traffic, it's going to allow the bad traffic to go through. Similarly, if you have orchestration security, if you do not have enough security on the orchestrator that allows to instantiate new network function, VNF, the Virtual Network Functions, one can just highjack the orchestration procedure and instead of orchestrating a specific VNF, it may orchestrate a wrong VNF in a wrong place. And that itself is pretty bad in terms of reliable operation. Similarly, for the hypervisor virtualization security, if a hypervisor is under attack or gets compromised then the VNF, the Virtual Network Function, from one tenant may be able to attack another tenant by compromising the reliable operation. So, these are some of the pillars. So, when we design an end-to-end 5G network, we need to look into, and make sure we have proper security requirements and mitigation techniques, which are available and designed from the very get-go.
Brian Walker: Where are these risks focused? Are they mainly at the consumer level? Or at the enterprise level as well?
Ashutosh Dutta: So, different security risks that are uniquely related to 5G are both on the consumer level and as well as the enterprise level. I'll just give you an example, because 5G's currently positioned to enable connectivity across many verticals. So, the security risk will be largely determined by the types of use cases for these verticals or the types of applications that are supported by these verticals, right? And these verticals could be transportation, first responder networks, smart city, tactical networks, auto industry, and automation. And the applications they support may have different key performance indicators. For example, they may need a different kind of bandwidth, different kind of latency, or different kind of system control. So, based on these KPIs we need to design our 5G network and, for each of these KPIs, we have to enable those components like edge-Cloud or SDN / NFV that may need proper security measures to be in place.
Eman Hammad: Maybe one point to add into this is, it's helpful always to look at the reference architecture for 5G. So, after the edge we're looking into the end users, devices, and systems. Systems that are enabled by 5G. And then after that demarcation point, we're looking at the main core networks and the connectivity to the Cloud. Now, as to end user level, we might be even dealing on that level with enterprise and end users as well. So, that speaks volumes to the complexity of 5G, and how the risks are propagated through even some architecture demarcation points, making it much more challenging to enforce cyber security functions, and require much more creativity and critical thinking when imposing security solutions. For example, one example is in one survey - most of the respondents from IP providers and telecom carriers - responded saying that they are looking at Zero Trust models to enable security in 5G. And Zero Trust models require really robust, scalable certificate management on all end devices and subcomponents of the 5G architecture, within the endpoint ecosystem, and within the 5G core system. So, this is one of the solutions that can actually mitigate risks from end-to-end on the 5G platform, some types of risks.
Brian Walker: And how do you anticipate security risks in mitigation with 5G evolving over time?
Eman Hammad: So, within any security framework, when you look at the complex system, and you look at a system that incorporates, as Ashutosh mentioned, many building blocks as well. The designers of the system have to incorporate from the very beginning an approach to assess the threats that are evolving with time, and assess the impact of such threats as they are actually happening. And this is usually formalized through a risk management framework. So, we believe that this is conducive for a 5G network to perform these realistic risk assessments on some of the scenarios and people should pay attention to the scenarios that are relevant to the use cases. For example, when you're really looking at risks of the type of electromagnetic interference, this has always been there, but with 5G and the different use cases for 5G, this takes a new shape and form. Also, risks related to resources exhaustion, and this is relevant to SDN, virtual function, cloud resources, slicing. So, any of these modular blocks that shape a service, if they are targeted within the control platform, or from a user via a massive IoT risk request or something of that sort, this will cause a resource exhaustion that will impact the reliability of the 5G as a whole system, or a major component of 5G. So, a risk management platform will say, "Okay, these are the risks that are currently happening. Let's assess for some of the use cases: what are the impacts, and based on that, let's look at existing security controls that are implemented, and what's missing? What are the gaps, and what's the priority to mitigate the high risks within that timeframe?" And adopting that methodology will help us as the threats continue to evolve. Because threats are just a point in time, and your security measures are a point in time. Now, a basic evolution or innovation that will help with 5G is incorporating that risk assessment into security automation. Meaning, if by some innovations and research, we can formalize an indicator of risk saying, "Okay, based on the latest threat intelligence, we know this is happening outside-- in the environment, in the ecosystem, then can we automate part of the provisioning of security functions to proactively protect certain parts of the network in anticipation of this threat vector?" So, this is where automation ties into risk management. This is not yet the case, but we expect this to be more prevalent in future systems to enable us to mitigate evolving cyber threats.
Ashutosh Dutta: I'd like to add a few things. I'll just take a specific use case. And we have a case here in which 5G is evolving over time. So, today we have 5G, 5G beyond, maybe it'll go 6G. There is one specific example I'd like to give, which is Open Source. As 5G and beyond evolve we are going to be relying maybe more on Open Source type solutions and while Open Source gives us a lot of modularity and acceleration to deploy, it also has potential risks, so that is something we all need to keep in mind. What are the potential risks associated with Open Source? And the second thing, Eman, you talked about automation, which is very important. How quickly you detect if there is an attack happening and how quickly do you mitigate that? This closed-loop automation, to a large extent, depends on the traffic variance, the service variance, which type of application, and they call it control variance. Where exactly do you want to put this closed-loop automation? Whether it should be in the edge, or should be in the core, or deep down in the application layer. So, to a large extent, that will determine how quickly we can detect and mitigate. And over time, I'd like to add that some of the AI and machine learning techniques could be applicable to determine the attack before the attack actually happens. And Eman, I think you talked about Zero Trust, right, how we can deploy those techniques to prevent the attack altogether.
Eman Hammad: Yeah, excellent point, Ashutosh. Just a follow-up, even when we look at automation that is enabled by A.I. and machine learning, as we have discussed many times, how to monitor A.I. and machine learning to establish the trust in the algorithm and to ensure that it continues to perform consistently with what has been designed, the design goals for the algorithms, right?
Brian Walker: What potential solutions might be developed to make 5G reliably secure?
Eman Hammad: So, when we look at the solutions that will enable 5G to catch up, to continuously be ahead of the game in cyber security and be able to deliver to its promise of being reliable and resilient. Some of the main trends are already being seen now, but they need to be evolved over time and innovated over time. One of the building blocks is encryption and certificate management. And one of the subtleties in that is that quantum computing threatens current encryption algorithms and certificate infrastructure. So, to be robust, future robust, or future proof, we have to start right now looking into PKI infrastructure, public key infrastructure to enable the Zero Trust models with quantum safe algorithms and encryption. That's one of the approaches. The other approach, we are looking now into Zero Trust. But as Zero Trust will require a massive scale of public key infrastructure and certificate management. We have started seeing trust platforms such as blockchain. Blockchain enables you within that certificate management to say, "This endpoint is trusted to actually connect to the network, or this antenna, or this base station is not a rogue space station. It's an authentic part of the network." So, similar solutions to establish trust, whether it's blockchain or something similar, that's scalable and reliable when it adds to reliability of the 5G network. Other solutions to take into account are the use cases for low latency. And the challenge comes from, let's imagine together use case for transportation or power systems. Within, if we are looking at 5G enabling these low latency use cases, then the delay that is incorporated by security functions going back through to the core, going to the core and back, this might not be acceptable within that key performance indicator for such use cases. So, we'll say, "Okay, at the edge, how can I enable these use cases within the low latency requirements with security guarantees?" And this will require innovations into light authentication or fast authentication. And this is beginning to be investigated in the academia and industry as well to enable these use cases. So, as mentioned so far, trust platforms, safe quantum algorithms or encryption, and low latency light authentication, for example. These are three examples of gaps that are existing in security controls right now that need more investment to establish reliable and robust security controls. In addition, one other point that we have to address as well is A.I. and machine learning. We know that the complexity of 5G will require orchestration and optimization that can only be handled by the likes of machine learning and A.I. And this will become more prevalent as we go to 5G-and-beyond networks. Now it’s necessary to establish some monitoring of these algorithms as they function, especially if they are to orchestrate security functions.
Ashutosh Dutta: The dynamic service churning, or security as a service is an important piece, and that can be enabled by having a closed loop that we talked about. Something that detects. That means you need to have a solid platform for security monitoring that means the ability to monitor the user plane, control plane and data plane signaling. At the same time, having analytics that can provide analytics to an orchestrated platform like ONAP (Open Network Automation Platform), and then having an interface from your orchestration platform to a software-defined network controller, like ODL (Open Day Light) or ONOS. And finally having some enforcement point on the DDOS (Distributed Denial of Service) or IDS (Intrusion Detection System) or IPS (Intrusion Prevention System) type functionality that interfaces with this SDN controller. So, that will allow one to detect any attack that's coming up, either at your Cloud-RAN or in the core, or in the application layer. And how quickly you can send it to orchestration. So, what is going to happen is you recover and resolve at the same time. So, while you're detecting the attack, who is attacking it, and the details of the attack, and trying to mitigate, at the same time you are recovering the network resources by having the ability to dynamically scale up the network. So, in that situation, in the case of a denial-of-service attack, you can still sustain the attack and any kind of priority services there will still continue to be provided while you figure out who is attacking it, and finally mitigate that, and then scale down the network. So, I believe this kind of security-as-a-service with the help of dynamic servicing will be very, very essential.
Eman Hammad: It speaks to the opportunities that are provided by 5G for isolation, proper mitigation, and forensics afterwards. I thought maybe we should add something on the application layer for our security capabilities because that will enable 5G to continue to operate. Because as you know 5G extends from the physical layer to application layer. One of the use cases for security is around 5G fraud. And we haven't touched on that previously. But within 5G fraud, with 5G, with all the pieces that tie into it has enabled—has better enabled providers and carriers better control over fraud within the subsystem and within the use cases.
Brian Walker: As threat vectors targeting 5G evolve, what would be the best approach to ensure reliable system operation?
Ashutosh Dutta: That means we need to have a closed connection between the KPIs that you discussed, for any specific type of application, and then how do we adapt your network accordingly to make sure your KPIs are properly attained. The other thing I was thinking is, they call it defense-in-depth. That means you have to design your network, and from the very get-go, you need to keep all the security threats and potential security risks in mind, and design your network accordingly. It is not like you wake up and figure out, "Well, this is a security risk, and I got to re-design my network." So, we have to keep in mind potential threat vectors, and do an end-to-end analysis. When I say that, you open up your network, open your network interface, look at all the components that comprise your network, and try to do a thorough analysis, we call it threat taxonomy, of each of the components, each interface, and what types of attacks could happen. If you design that ahead of time, then you can think about the mitigation techniques, and potential risks mentioned earlier, to have the mitigation technique that can be applied. If you do not have a security control, you make sure you put the proper security control in place. It has to be like an iterative process.
Eman Hammad: Yeah, yes, exactly. And that's what a risk management framework does. But I like the point, Ashutosh, where you mentioned the system is a not a point in time. The system design is not a point in time. So 5G is an evolving, living system, and I don't think that's an overstatement, because the orchestration, the automation, the optimization, the dynamic allocation of resources between the user and the control plane, the different -- how you can actually shape, and it was based on the changing KPIs, based on the changing attacks, based on the current state of system security or system service levels, required service levels, attest to the requirement for operators, security analysts that are working on the system, and automation like what are device levels of automation to make that feasible. It goes back into, yes, you have to have a very deep understanding of the system, the services, the APIs, the system calls between the APIs and what components work, how. And even in the design of network slicing for proper isolation, so that you have a reliability metric of the system because of the Security by Design that you have done at the very beginning that you will continue to do over time. And use cases change as the threat landscape changes, and as your load, or your requirements change.
Brian Walker: What are the inherent security opportunities resulting from 5G enablers?
Ashutosh Dutta: So, first of all, I'd like to make it clear when you say security opportunities, this means when we add or move to a new type of network, or new enablers, that provides us some opportunity and reduces the CAPEX or OPEX and helps smooth operation of the network, etcetera. But we already discussed some of the security issues associated with those enablers. What I'm talking about here is there are some security implications that could be minimized by having the enablers. So, there are two things. One is by introducing the enablers that are security issues that need to be taken care of. And this question we're talking about, the security opportunities that will be provided by these enablers, which are otherwise not available in previous generation of networks. I'll give you a few examples here. The first example is by having a 5G network, and 5G technology, inherently gives the resiliency support and flexibility support. So, I'll just take the example of network function virtualization, - NFV / SDN - these are the enablers of 5G. When they were not there, if there was an attack taking place, a denial-of-service attack, and, at that time it was taking a long time to detect, a long time to re-provision the network, or dynamically provision the network, but with 5G technology, this specific issue is taken care of because NFV and SDN, by default inherently provide this resiliency of the network by scaling up and scaling down the network on demand. So, the effect of a denial-of-service attack is minimized by having this resiliency. At the same time, if there is attack taking place, how quickly can we detect and mitigate that? By having an SDN controller in this closed loop function, it has the ability to dynamically service chain the DDOS, IDS and IPS functionalities and block this malicious traffic from going to any customer's premises. So, that is an opportunity, the programmability and flexibility. The third one I wanted to talk about is slicing. Network slicing is another enabler. So, network slicing itself provides the ability to assign resources to priority applications. You know, let's say an IoT application, first responder application, automotive application, they all get resources reserved from end-to-end. So, this is an opportunity, right? Well, at the same time we discussed earlier, slicing itself also gives rise to some security issues that needed to be taken care of. So, we are just highlighting some of the opportunities, security opportunities, those are provided, because if there is no slicing, the priority services’ quality of service is not properly maintained, and you cannot separate one application from another application, right? If the first responder wants to send a high quality of service, audio and video, that can be made possible by the use of slices. But, at the same time, virtualization is another opportunity where you can segment your computing resources and provide one type of application to one VNF or tenants, another type of application, another VNF with tenant, right? So, these are some of the high-level security-related opportunities that we can obtain from 5G type technology.
Eman Hammad: I just want to follow up by saying these capabilities of 5G, the enablers of 5G do provide some inherent characteristics that are like intuitive to expand our security and controls. Even provide security controls that were not available in other systems, such as slicing. What I wanted to add is to make sure that we reap the benefits of these inherent characteristics, we need to actually implement additional security controls and properly design the system with this thinking in mind. Meaning, for example, when we design the slicing, we have proper isolation of the slices, and some cap on resources for critical slices, for example. Critical services are assigned slices to make sure that if something happens to the resources, these slices continue to survive. This takes us to talk about other types of opportunities that come from 5G, and I guess I hinted at that when we said, "properly designed with security in mind." So, this requires investment in the security of 5G. And a continuous improvement of the security, but this could give us several folds of benefits. One benefit is to enable our system being resilient, flexible, reliable, as Ashutosh mentioned. The other thing is it enables the providers and carriers to extend their business into new elements. And I'll mention one example. We hear more about security-as-a-service. If a service provider or a carrier implements the proper security controls up to the edge, with monitoring, with some forensics and incident response, then that service provider can actually offer security-as-a-service for its clients, including enterprise clients, and different use cases such as certain transportation providers or a smart city.
Ashutosh Dutta: I’d also like to add one more thing I forgot to discuss, which is very, very important. As the operators are trying to get into 5G, they're building this eMBB (enhanced Mobile Broad Band) type network, one of the components is Cloud-RAN, and separation of user plane and control plane, right? So, by having Cloud-RAN or Open RAN type networks, you are separating your BBU (Base Band Unit)and RRH (Remote Radio Head) functionality, so thereby you are also dynamically adding RAN functionality, RAN functions in the networks in case of lots of IoT type devices, millions of IoT devices trying to get connected. You can easily scale up your RAN functionality on the BBU side in the Cloud right? And the security monitoring mitigation technique can be easily ported in Cloud-RAN, thereby, you can detect the type of attacks early enough, so your core network is not really affected, so that is another opportunity as well.
Brian Walker: Where can people learn more about 5G security?
Ashutosh Dutta: Eman and I are the Security Working Group Co-Chairs, that's one of the Roadmap Working Groups for the IEEE Future Networks International Network Generation Roadmap, we call it INGR. There are 15 roadmap working groups, and Security is one of them. If you visit the website, futurenetworks.ieee.org/roadmap, you will get to know more details. We have already published the first edition of the INGR Roadmap. You should be able to find out on the website some of the things Eman and I spoke about today, but it goes into details of three-years, five-years, and ten-years, what the security landscape is going to look like. How's it going to be useful for 5G-and-beyond, 6G or 7G. So, that's a good source you can take a look. In addition, we also have bi-weekly meetings, you're welcome to join this group, contribute. We have started working on the second generation of the Roadmap. At the same time, there are lots of opportunities like podcasts like we are doing today, webinars, research articles and testbeds, etcetera.
Eman Hammad: I want to add just one thing, which is that being involved with this initiative within IEEE enables you to kind of get more visibility into what's happening in parallel with the different initiatives and efforts, as well as help shape, if we feel, for example, there is a need or a serious gap in security in a certain area that we anticipate to be prevalent in five to ten years, we can point into that, and we can actually work on making special editions, special journals, special conferences, symposiums that will provide an incentive for people to pay attention to these gaps. So, it's really worthwhile to be part of the ecosystem.
Ashutosh Dutta: Yeah, that's a good point. So, there are lots of resources here, there are 46 Societies within IEEE. Over 23 of those are contributing to IEEE's Future Networks Initiative. And the Security Working Group also does collaborate with the other 14 Working Groups to see what are the potential security implications they might have. For example, MIMO, hardware, millimeter wave, edge automation applications. So, we have an opportunity to interact and collaborate with them and find out how we can look at their work and what are the potential security implications there. So, this is happening within IEEE, but we also do collaborate and attend 11 other standards groups like 3GPP, IETF, ITU and ETSI. And we try to complement the work they're doing by developing new technologies, or new algorithms, and new optimizers and techniques in security, how it can help the architecture being developed by, let's say, 3GPP, or protocol developed by IETF. So, that is a real benefit. Anything, Eman, on the standards' side?
Eman Hammad: Just the collaboration with the Standards Group of IEEE, because we all know how the strength of IEEE when it comes to standards. So, there's also the opportunity within IEEE to look at the gaps in standards, or try to facilitate more conversations between the main standards for these that you mentioned, Ashutosh.
Ashutosh Dutta: Right, and the other thing I wanted to also mention are the testbeds. Within the IEEE Future Network Initiative, we have a Testbed Working Group. But at the same time, we also have an MOU agreement with a few of the testbed like RUTGERS/WINLABand 5G Lab in Germany, and a few other testbeds where IEEE volunteers or members of Future Networks get a chance to login and do any kind of experimental work. So, for example, if somebody wants to try some security related experiment, they can join this group, and by being a member of this group, you get access to these labs, and can build your own experiments. At the same, IEEE standards activity recently has come up with IEEE Open, where they're building an Open Source testbed. Thereby, you can try various security related experiments. So, collaboration is very important, not only with academics, with industry, with the vendor community, develop the security requirements ahead of time, bring it to standards and build some proof of concept to make sure some of the security challenges or issues that we talked about should be validated or demonstrated, right? So, it's like a complete ecosystem. And we need help from, and collaboration from everybody around the world to make 5G and beyond more secure.
Eman Hammad: One final thought is around trust. So, when we discuss security or cyber security in general, we're talking about how we trust the technology that enables our day-to-day life. And this is exactly what we're talking about when we talk about being involved in shaping the initiatives; or try to be part of the ecosystem, to make sure that we build trustworthy systems, or we help guide the design and build out of trustworthy systems.
7 Experts Forecast What's Coming for 5G in 2020

Predictions on the 5G Ecosystem from the IEEE Future Networks Initiative
14 January 2020
2019 was the relative calm before the 2020 5G deployment storm. Carriers took their first steps in network deployments while engineers worked through gnarly technical challenges, and important tests of the technology were performed in real-world conditions.
It became clear in 2019 that 5G was much more than an upgrade to our mobile phones, and that its first use would not be consumer led. Rather, for the first time in any generation of wireless, enterprise applications would lead the way as first adopter.
The IEEE Future Networks International Network Generations Roadmap (INGR), First Edition predicts, “..it is anticipated that 2020 will see a transformation of the communication industry as multiple new (and powerful) players will fight for market share in which content and ease of use will be the driving factors.”
We tapped into IEEE Future Networks Initiative subject matter experts, many of whom are involved in the INGR, to get their insights, perspectives and expert opinions on what is to come in networks in 2020. This is what they said:
Spectrum Matters
Timothy Lee, Co-chair of the IEEE Future Networks Initiative, and General Chair, IEEE IMS2020
- Below 6 GHz, 5G deployments will gain momentum in 2020 with many installations across the globe. Meanwhile, mmWave 5G deployments will lag due to challenges of small cell deployment issues, costs, and regulatory hurdles. American carriers like Sprint with sub-6 GHz bands (i.e., 2.5 GHz) may gain an edge since they do not have to deploy small cells so soon.
- Shared Spectrum Access will be a key technology in the US that will enable sharing of commercial licensed, unlicensed, and government bands. Once proven, this will allow sub-6 GHz spectrum for more rapid deployment, especially in rural regions.
- Second generation mmWave transceivers will be released in 2020, paving the way to improved performance and much reduced costs for user equipment (UE).
- What will be the first 5G killer app to gain attention in 2020? AR/VR? Autonomous cars? Enhanced Broadband? MM2M for IoT? Some other use case?
What Innovation in Spectrum Allocation can Mean
James Irvine, Co-chair, IEEE Future Networks Initiative - Community Development Working Group, and Reader, Electronic and Electrical Engineering, University of Strathclyde
2020 will be the year when private 5G networks start being taken seriously. While 5G incorporates a range of innovations such as low latency and higher reliability, deployments so far have been very traditional, with mobile network operators (MNOs) adding the technology to their existing networks and focusing on delivering higher speeds. Instrumental in this is that, in general, it is the traditional operators who have access to spectrum. However, across the world, regulators are recognizing the need for innovation in spectrum allocation. For example, the UK regulator Ofcom recently introduced rules for spectrum sharing and the reallocation of existing mobile operator spectrum in areas where it isn’t currently used, with the aim of making local service provision easier. Combining these rules with the more flexible network structure of 5G will make community network providers and 5G private networks a practical possibility. This, in turn, will stimulate the deployment of new, specialized applications such as protection for electrical distribution networks, which 5G makes possible but which aren’t in the plans of traditional operators. As a result, 5G will disrupt the cellular market in a way previous generations have not.
The wild-card for 5G emergence is deployment: 2020 with some creep into 2021 and 2022
David Witkowski, Chair, IEEE Future Networks Initiative - International Network Generations Roadmap – Deployment Working Group, and Founder & CEO, Oku Solutions LLC
- Until the mobile device ecosystem begins widely offering 5G support, initial deployments of 5G will focus on Fixed Broadband as a competitor to xDSL and DOCSIS cable.
- We expect deployments of 5G Enhanced Mobile Broadband for portable devices will ramp up in late 2020, and initially they will focus on in-building networks (e.g. malls, convention centers, sports venues) and downtown areas with high user densities.
- Industrial IoT (IIoT) deployments using 5G Ultra-Low Latency Communications (URLLC) and Massive Machine-Type Communications will likewise depend on availability of sensors, actuators, and, in some applications, edge computing. We expect this to begin in 2021 as IIoT device vendors release 5G-enabled products.
- Availability of 5G URLLC will enable augmented reality (AR) and virtual reality (VR) products – initially for specialized (corporate, medical, government, and public safety) applications and later for consumers as economies of scale bring down costs. We expect some early announcements of 5G-enabled specialized AR/VR in 2020.
- Citizens Broadband Radio Service (CBRS) will enable private 4G/5G networks and will be disruptive. Device support for the CBRS band will emerge in late 2020, ramping to wide availability in 2021. We expect that in 2022, low-cost consumer-grade CBRS access points will enable homeowners and small businesses (SOHO) to deploy CBRS sites in the same way they currently deploy Wi-Fi access points.
- Widespread availability of CBRS support in devices will be disruptive to Wi-Fi, especially in enterprise and municipal/public deployments, then in SOHO deployments. Alternative providers now using Wi-Fi First models (Comcast Xfinity Mobile, Google Fi) will shift towards a “Wi-Fi or CBRS First” model, especially if broadband companies add support for CBRS into residential and small business gateways.
- The wild-card for 5G emergence is deployment. Local governments have struggled with 4G small cell deployments, and the higher density of 5G sites in millimeter wave bands presents additional challenges to application and permitting at the local level. Fears about 5G health effects will require deliberate response from industry, governments, and medical academia to counter misinformation, pseudoscience, and superstition.
Calling for a Sea Change in Transmitter RF Efficiency
Earl McCune, Ph.D., Co-chair, IEEE Future Networks Initiative - International Network Generations Roadmap – Hardware Working Group, Fellow IEEE, and Chief Technology Officer, Eridan Communications
As more operators push 5G from demonstration sites into wider deployment, 2020 is going to be the year that power efficiency moves to the center of the conversation. Today’s 5G radios are typically operating at about 10% power efficiency, and 5G base stations overall consume about three times as much power as the LTE base stations they replace. Beyond the increased scrutiny that CFOs at mobile operators will be applying to manage the costs of this input power, the waste heat generated by 5G radios is presently imposing substantial design constraints.
But for 5G to reach universal adoption, matching the 20%-range of power efficiency of LTE systems is nowhere near enough. To operate profitably, the industry requires a sea change in transmitter RF efficiency – getting to the neighborhood of 40-60% DC to RF, including all linearization. From small cells that are genuinely small, to cost-effective solar-powered systems, to beam-steering MIMO arrays to cover large open spaces, power efficiency must be at these levels to open up the new deployment options the industry needs.
The 5G Energy Gap – The Bad News and the Good News
Brian Zahnstecher, Chair, IEEE Future Networks Initiative - International Network Generations Roadmap – Energy Efficiency Working Group, and Principal of PowerRox
Ok, the bad news first…as these massive 5G networks are being deployed in full speed in 2020, there is the growing issue of the 5G Energy Gap, which is how microwatt-level devices at scale can have a direct impact on the ability of the utility grid to meet the load energy requirements, while maintaining grid reliability. The good news is this is also a fantastic opportunity to fast-track an emerging technology to the mainstream. Energy Harvesting (EH) solutions can supplement or even mitigate the tiny power requirements of systems where it matters most, at the edge. This is done by scavenging every form of physical, ambient energy from the surrounding environment to spare the utility grid and power plants the burden of the 105-106 Power Cost Factor multiples applied to each and every microwatt of edge device received power. Not only will EH sources be a critical factor in addressing the 5G Energy Gap, but this symbiotic relationship will also be mutually beneficial in the respect that increasing viability of the EH ecosystem will also make application to IoT and IIoT devices more pragmatic and affordable. Not only does this lead to a massive environmental impact (i.e., reduction of batteries/hazardous waste/carbon footprint) and increased reliance on sustainable power sources, but also drives critical system design philosophies in power management and energy efficiency.
If and when 5G+ Becomes Reality
Rod Waterhouse, Co-chair IEEE Future Networks Publications Working Group, and, CTO, Octane Wireless
2020 promises to be a very exciting and important year for 5G and future networks. We will definitely see more and more roll out and therefore penetration of the lower spectrum (less than 6 GHz) 5G network throughout the world. Associated with this we will see more debate on the health-related aspects of small cell architectures, whether the debate is founded in science or not. On the research and development side of things, we will see further, exciting activity in the realization of millimeter-wave technology for handsets and access points, and by the year’s end we should be in a better position to see if and when 5G+ (the true incorporation of mm-waves into the mobile network) becomes a reality. Areas of interest to watch over the next 12 months include the role of satellites in future networks, the ramping up of vehicle to X (V2X), the realization of virtual medical care and also efficient technology and protocols for the interface between the backbone and mobile networks. All could be crucial to the success of future networks.
Increasing Demand, Paths of Progress, and New Challenges
Ashutosh Dutta, Co-chair of the IEEE Future Networks Initiative, and Senior Professional Staff, JHU Applied Physics Laboratory
- There will be an increased demand for Wi-Fi 6 and private 5G type networks, resulting in co-existence of Wi-Fi and cellular technologies.
- Security will be embedded in the end-to-end network resulting in more secured 5G networks.
- There will be an increased trend in virtualizing the network end-to-end.
- There will be an increased trend in implementation of technologies like Cloud RAN and Mobile Edge Cloud.
- There will be an increased demand for use of 5G technologies for tactical and first responder networks.
- There will be a big focus toward sustainability and an increase in activities to spread wireless connectivity in rural networks.
- There will be increased activities toward implementing experimental testbeds for 5G technologies.
- Supply chain, geo-political, and environmental issues will be barriers for rapid deployment of 5G technologies.
- Rural communities will see widespread deployment of low-band networks.
- Satellite technologies will play an important role in support of 5G use cases.
Learn more about advances to come for 5G and future networks through the International Network Generations Roadmap (INGR), available now on the IEEE Future Networks website.
Future Networks Videos
Featured Video
5G Demystified: Will 5G Kill Wi-Fi?
15 December 2022, LinkedIn Live
We use Wi-Fi at home because it offers speeds better than our LTE phones get. But if 5G will provide speeds 10 times better than LTE, will that mean we no longer need Wi-Fi at home? Will public Wi-Fi become as antiquated as internet cafes? IEEE’s panel of experts will discuss and maybe debate the battle for last mile connectivity between 5G and Wi-Fi, as well as recent advances on how these two technologies may co-mingle.
Speakers Include: David Witkowski (Oku Solutions), Richard Bernhardt (WISPA), Dan Warren (Samsung Research UK), Claus Hetting (Wi-Fi NOW)
A Delay Modeling Framework for Embedded Virtual Network Function Chains in 5G Networks
Qiang Ye, Weihua Zhuang, Department of Electrical and Computer Engineering, University of Waterloo, Waterloo, Canada
{q6ye, wzhuang}@uwaterloo.ca
Xu Li, Jaya Rao, Huawei Technologies, Ottawa, Canada
{Xu.LiCA, jaya.rao}@huawei.com
IEEE Future Networks Tech Focus: Volume 3, Issue 1, March 2019
Abstract
With the development of software-defined networking (SDN) and network function virtualization (NFV), software-defined topology (SDT) design poses technical challenges in embedding virtual network function (VNF) chains to minimize the embedding cost under packet delay constraints. In this article, we present a novel E2E delay modeling framework for embedded VNF chains to facilitate the delay-aware SDT design. A resource allocation policy called dominant-resource generalized processor sharing (DR-GPS) is applied among multiple VNF chains embedded on a common physical network path to achieve dominant resource allocation fairness and high system performance. An approximated M/D/1 queueing network model is then developed to analyze the average E2E packet delay for each traffic flow traversing an embedded VNF chain.
1. Introduction
The fifth generation (5G) communication networks are evolving to interconnect a massive number of miscellaneous end devices with diversified service types for Internet-of-Things (IoT) [1]. Machine-to-machine (M2M) communication services and high data rate broadband services are two typical IoT service categories with different traffic statistics and customized end-to-end (E2E) delay requirements. To accommodate an increasing traffic volume from massive IoT devices with differentiated quality-of-service (QoS) demands, the number of network servers providing different functionalities, e.g., firewalls, domain name system (DNS), needs to be increased for boosted network capacity. However, the densified network deployment largely augments both capital and operational expenditure. Software-defined networking (SDN) [2] and network function virtualization (NFV) [3] are two complementary technologies to enhance global resource utilization and to reduce the network deployment cost for service customization, respectively. For the core network, the SDN control module determines the routing path for each service flow based on global network state information. A service (traffic) flow refers to aggregated traffic from a group of end devices belonging to the same service type and traversing the same source and destination edge switches. On the other hand, a centralized NFV control module exists to orchestrate virtual network functions (VNFs) at appropriate general purpose network servers (also named NFV nodes) to achieve flexible service customization. The SDN and NFV control modules are combined as an SDN-NFV integrated controller for VNF orchestration and placement, and traffic routing decisions. At the service level, each service flow is required to pass through a specific sequence of VNFs to fulfill an E2E service delivery with certain functionality and customized QoS requirement. For example, a DNS service flow traverses a firewall function and a DNS function sequentially. A video traffic flow passes through a firewall function and an intrusion detection system (IDS) for a secured E2E video conferencing. We call a set of VNFs interconnected by virtual links as a VNF chain. Software-defined topology (SDT) design studies how to embed each VNF chain onto the physical substrate network to minimize the VNF deployment and operational cost [4].
2. Delay-Aware SDT Design
For the SDT design, a joint routing and VNF placement problem can be formulated as a mixed integer linear programming (MILP) problem, and a low complexity heuristic algorithm is proposed to solve the problem [4]. The SDT output is the optimal VNF placement on NFV nodes and the optimal traffic routing paths among embedded VNFs. There is an essential tradeoff between minimizing the embedding cost and satisfying the E2E packet delay requirements. To reduce the embedding cost and improve the resource utilization, different VNF chains are preferred to be embedded on a common physical network path with multiple VNFs operated on an NFV node, as shown in Fig. 1. However, the E2E packet delay for each embedded VNF chain can be degraded as it shares both computing and bandwidth resources with other VNF chains.
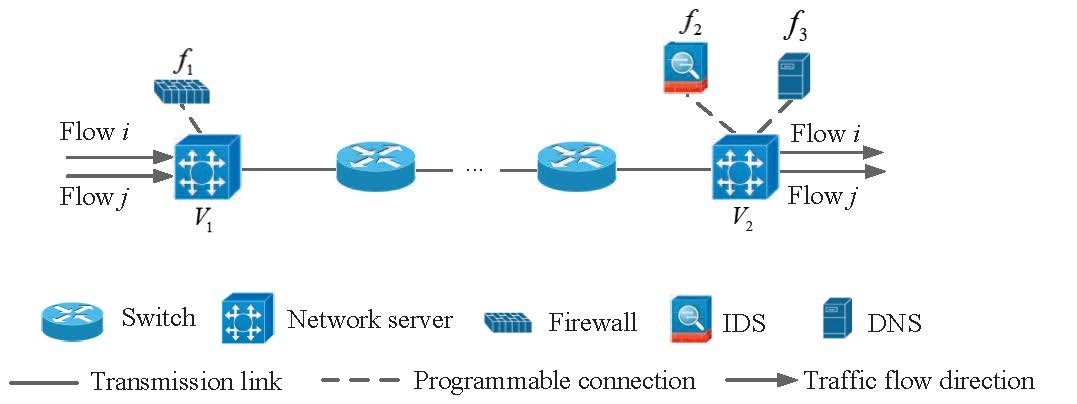
Figure 1: Multiple VNF chains embedded on a common physical network path.
Existing studies model the E2E packet delay of a traffic flow traversing an embedded VNF chain as the summation of packet transmission delays over each embedded virtual link, without considering the packet processing delay at each NFV node [3], [5]. As a matter of fact, when each packet of a traffic flow traverses an embedded VNF on an NFV node, the packet requires an amount of CPU processing time for certain functionality and an amount of packet transmission time on the outgoing link sequentially. Depending on the type of traversed VNF and the type of service that each flow belongs to, different flows have discrepant time consumption for both CPU processing and link transmission. Some small packets with large header size (e.g., DNS request packets) demand more CPU processing time, whereas other packets with large packet size (e.g., video packets) consume more link transmission time. Therefore, how to allocate both computing and bandwidth resources among the flows traversing the VNF(s) embedded on a common NFV node needs investigation, which affects the packet delay of each flow. More importantly, a comprehensive E2E delay model for packets of a service flow passing through each embedded VNF chain should be established, with the joint consideration of packet processing delays on NFV nodes and packet transmission delays on physical links and network switches (see details in Section III), to achieve delay-aware SDT design.
3. E2E Packet Delay Modeling
When traversing an embedded VNF, each traffic flow, say flow i, requires different amounts of packet processing time and packet transmission time, denoted by [ti,1,ti,2]. We refer to this time vector as time profile. We define the resource type that a traffic flow consumes more in processing or transmitting one packet as dominant resource. Since different service flows have discrepant time profiles when passing through the VNF(s) on an NFV node, a dominant resource generalized processor sharing (DR-GPS) scheme [6] is employed to allocate the CPU processing resources and the transmission bandwidth resources among different flows. Compared with GPS [7], the DR-GPS is a promising strategy in the context of bi-resource allocation to balance the trade off between fair allocation and high resource utilization. If GPS is directly applied for the bi-resource allocation (i.e., bi-resource GPS), where both processing and transmission rates are equally partitioned among different service flows, the system performance can be degraded due to the discrepancy of time profiles of different flows. In DR-GPS, the fractions of dominant resources allocated to multiple backlogged flows at an NFV node are equalized to ensure the allocation fairness on the dominant resource types (i.e. dominant resource fairness). The fraction of non-dominant resources is allocated to each backlogged flow in proportional to its time profile to eliminate the packet queueing delay before link transmission. When a traffic flow at an NFV node has no packets waiting for processing and transmission, its allocated resources are redistributed among other backlogged flows according to DR-GPS, to improve resource utilization via traffic multiplexing. With the DR-GPS, the processes of packets from each flow traversing the first NFV node V1 of an embedded network path can be modeled as a tandem queueing system, as shown in Fig. 2, where a set of flows traverse V1 and the traffic arrival process for flow i is modeled as a Poisson process with the arrival rate ɣi. The processing and transmission rates allocated to flow i are ri,1 and ri,2, where we have ri,1 =ri,2 according to the DR-GPS. Thus, there is no packet queueing before the link transmission, and packet queueing exists only before the CPU processing.
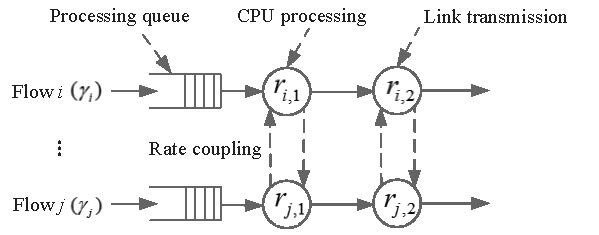
Figure 2: A tandem queueing model for traffic flows traversing V1.
Given the set of flows multiplexing at an NFV node, the instantaneous packet processing rate of a tagged flow varies among a set of discrete rate values, depending on the non-empty queueing states of the other flows. This rate correlation makes the queueing analysis intractable for delay calculation. For tractability, we calculate the average packet processing rate for each flow by taking into account the processing queue non-empty probabilities of all the other traffic flows (i.e., exploiting the traffic multiplexing gain), which is used as an approximation of decoupled packet processing rate for the flow [1]. Then, a decoupled queueing model for packet processing of each traffic flow at V1 is established, where the decoupled processing rate for flow i is denoted by di,1, as shown in Fig. 3. To further decouple the transmission rate correlation, we analyze the packet departure process from each decoupled processing at V1. Let Xi be the packet inter-departure time of flow i at the decoupled processing of V1. Due to the Poisson characteristics of the packet arrival process, a departing packet sees the same steady-state queue occupancy distribution as an arriving packet [8]. Therefore, if the mth departing packet sees a non-empty queue, we have Xi = Ti, where 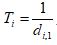
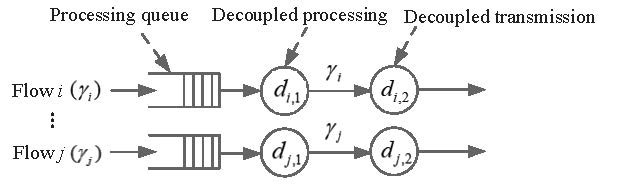
Figure 3: A queueing model for decoupled packet processing and transmisson [1].
Due to the memoryless property, Yi follows the same exponential distribution as the packet inter-arrival time. Therefore, the probability density function (PDF) of Xi can be calculated as
where , and
are the PDFs of Yi+Ti and Ti , respectively. As Ti and Yi are independent variables,
can be calculated as the convolution of the PDFs of Yi and Ti [1]. Then, the cumulative distribution function (CDF) of Xi, and its mean and variance are further expressed as [1]
Eq. (2) and Eq. (3) indicate that the packet inter-departure process from the decoupled processing is a general process between a Poisson process and a deterministic process, with the average departure rate ɣi. Therefore, by using the same method as the processing rate decoupling, we calculate the decoupled packet transmission rate for flow i as di,2, where di,2= di,1. This is because the instantaneous processing and transmission rates are equalized according to DR-GPS, i.e., ri,1 =ri,2, and the average departure rate from each decoupled processing is same as the arrival rate. With the completely decoupled queueing model for both packet processing and packet transmission, the average packet delay, Di,1, for traffic flow i traversing the first NFV node can be determined [1], including packet queueing delay before processing, decoupled packet processing delay, and decoupled packet transmission delay, according to the M/D/1 queueing analysis.
Before modeling the delay of packets traversing the second NFV node V2, we first analyze the packet departure process from the decoupled link transmission of flow i at V1, which is derived as the same general process with the departure process from the decoupled processing (Analytical details are provided in [1]). The process approaches a Poisson process when ɣi is small and a deterministic process when ɣi is large. Packets from each decoupled outgoing link transmission are then forwarded through a number of network switches and physical links before arriving at the subsequent NFV node. According to Proposition 1 in [1], the packet arrival process of a traffic flow at V2 is the same as the departure process from V1, as long as the transmission rate allocated to the flow at each traversed network switch and link is greater than or equal to the decoupled transmission rate at V1. In this way, no queueing delays are incurred on switches and links, and the bandwidth utilization is maximized. The delay over the embedded virtual links between V1 and V2 can be calculated as the summation of packet transmission delays over network switches and physical links between V1 and V2 [1]. Since the packet arrival process of each flow at V2 is the same general process in between a Poisson process and a deterministic process with the average rate ɣi, we decouple the processing and transmission rates for flow i at V2, similar to the rate decoupling at V1. The decoupled rates are denoted by di,1 and di,2, as shown in Fig. 4, where di,1 = di,2.
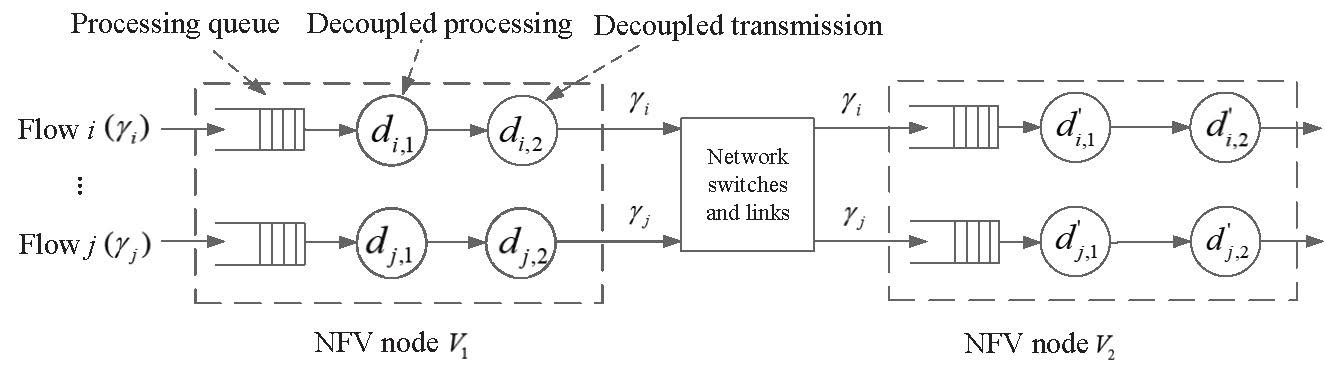
Figure 4: A decoupled queueing model for traffic flows traversing V1 and V2 in sequence.
Since the traffic arrival process at V2 correlates with the packet processing and transmission at V1, a G/D/1 queueing model is not accurate for calculating the delay of packets going through each decoupled processing at V2, especially when ɣi is large [8]. For the case of di,1 < di,2, the traffic arrival process of each flow at V2 is more likely to approach a Poisson process with the varying rate parameter ɣi under the queue stability condition [1]. For the case of di,1 ≥ di,2, there is no queueing delay for packet processing at V2. We approximate the packet arrival process of each flow at V2 as a Poisson process with rate parameter ɣi , and establish an M/D/1 queueing model to determine the average queueing delay before processing at V2. Proposition 2 in [1] indicates that the average packet queueing delay, based on the approximated M/D/1 queueing model, provides a more accurate upper bound than that using the G/D/1 queueing model under both lightly- and heavily-loaded input traffic. Therefore, the approximated average packet delay Di,2 , for traffic flow i traversing V2 can be determined [1].
In general, the same queueing modeling methodology can be applied independently at each subsequent NFV node (if any) along the embedded network path, upon which an approximated M/D/1 queueing network is established to calculate the E2E packet delay for each embedded VNF chain. With the proposed analytical E2E packet delay modeling, the delay-aware SDT design can be achieved as illustrated in the flowchart in Fig. 5. First, multiple VNF chains for different E2E service requests are pre-embedded on the substrate network. Then, our proposed delay modeling framework is applied to determine the E2E packet delay for traffic flows traversing the embedded VNF chains. If the E2E packet delay constraints for the flows are satisfied, the delay-aware VNF chain embedding process is completed; otherwise, the VNF chain pre-embedding phase is revisited and the whole process is repeated until delay-aware SDT is achieved.
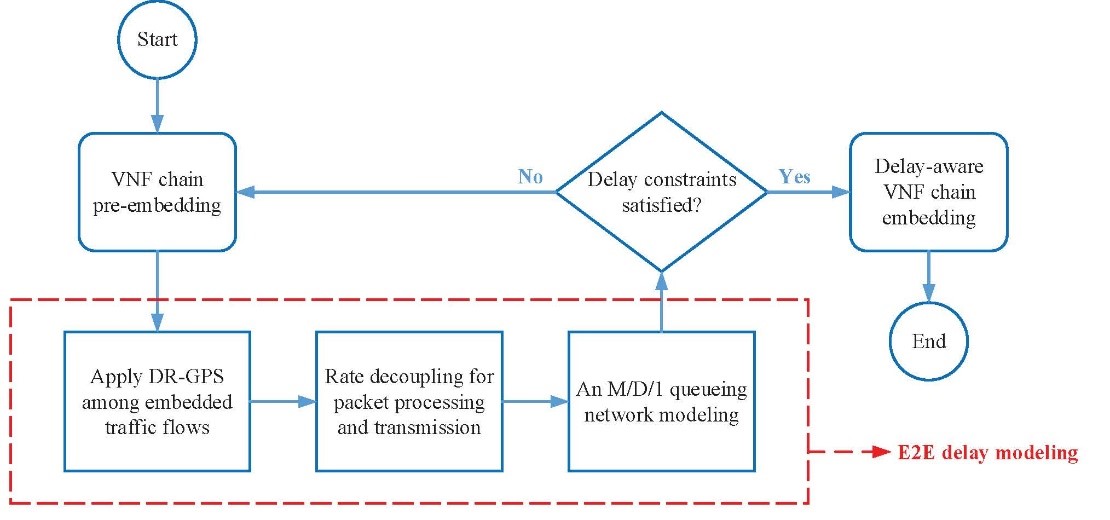
Figure 5: A diagram illustrating the delay aware SDT design process.
4. Simulation Results
In this section, simulation results are provided to verify the accuracy of the proposed E2E packet delay modeling for embedded VNF chains. All simulations are conducted using OMNeT++ [9]. We consider two VNF chains embedded over a common physical network path, as shown in Fig. 1, where flow i traverses f1 and f2 and flow j traverses f1 and f2. We test time profiles of the service flows traversing different VNFs over OpenStack [10], a resource virtualization platform for VNF chain orchestration. The testing results and other simulation settings are referred in [1]. We verify the effectiveness of the proposed rate decoupling and delay modeling methods at each NFV node. Packet queueing delay for one of the flows (flow j) before processing at V1 is shown in Fig. 6. It can be seen that the queueing delay derived using the rate decoupling method is close to the simulation results with rate coupling. Packet queueing delay for flow j at V2 is evaluated in Fig. 7, where the queueing delay derived based on the approximated M/D/1 queueing model achieves a much tighter upper bound than that using the G/D/1 queueing model.
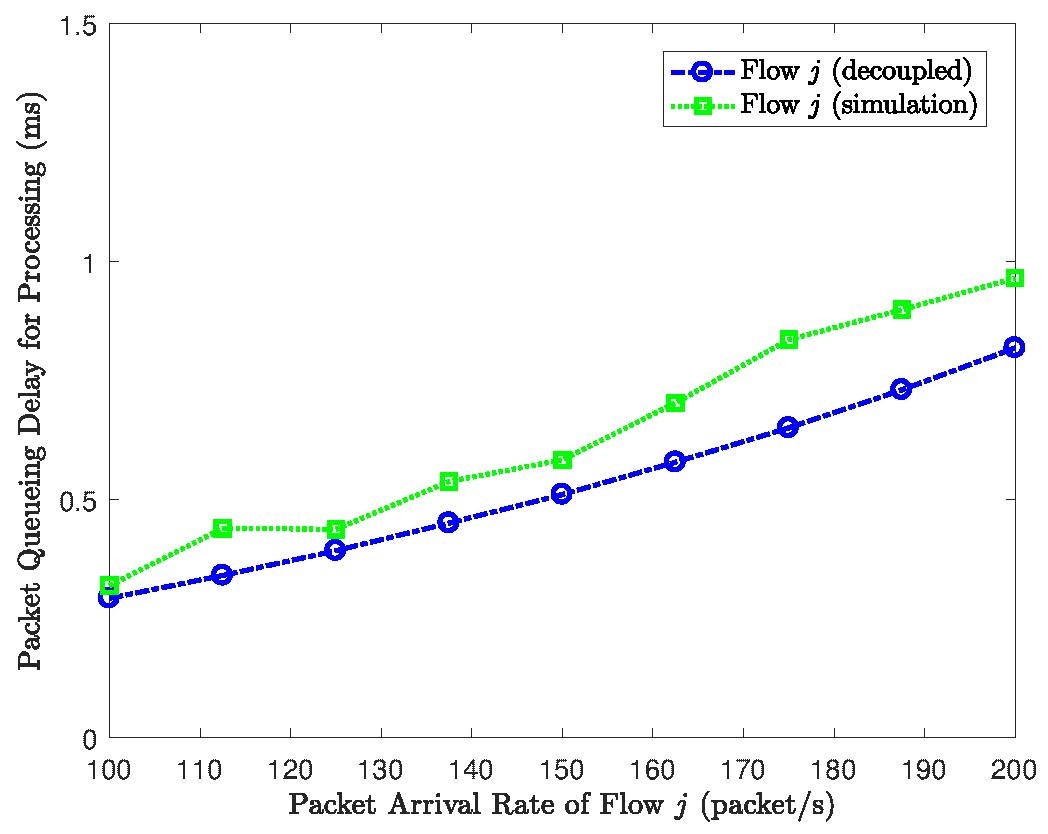
Figure 6: Average packet queueing delay for processing at V1.
5. Conclusion
In this article, an E2E packet delay modeling framework is established for embedded VNF chains over the 5G core network to facilitate delay-aware SDT design. For the VNF chains sharing resources over a common embedded physical network path, the DR-GPS scheme is employed to allocate the computing resources on network servers and bandwidth resources on outgoing transmission links to achieve dominant resource allocation fairness and high resource utilization. With DR-GPS, an approximated M/D/1 queueing network model is established to analyze the E2E packet delay for traffic flows passing through each embedded VNF chain, which is proved to be more accurate than the G/D/1 queueing model for flows traversing each subsequent NFV node following the first NFV node. Simulation results demonstrate the accuracy and effectiveness of the proposed E2E delay modeling framework, upon which delay-aware SDT can be achieved.
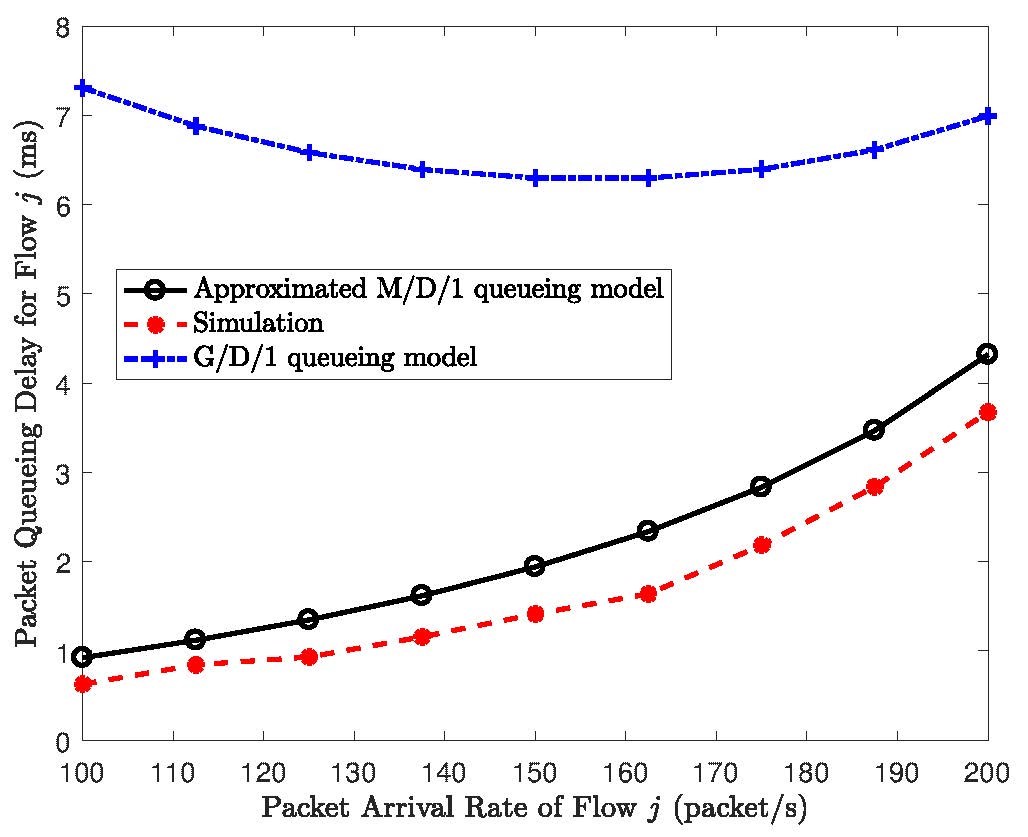
Figure 6: Average packet queueing delay for processing at V2.
Acknowledgement
This work was supported by research grants from Huawei Technologies Canada and from the Natural Sciences and Engineering Research Council (NSERC) of Canada.
References
[1] Q. Ye, W. Zhuang, X. Li, and J. Rao, “End-to-end delay modeling for embedded VNF chains in 5G core networks,” IEEE Internet Things J., to appear, doi: 10.1109/JIOT.2018.2853708.
[2] W. Xia, Y. Wen, C. H. Foh, D. Niyato, and H. Xie, “A survey on software-defined networking,” IEEE Commun. Surv. Tutor., vol. 17, no. 1, pp. 27–51, First Quarter 2015.
[3] F. Bari, S. R. Chowdhury, R. Ahmed, R. Boutaba, and O. C. M. B. Duarte, “Orchestrating virtualized network functions,” IEEE Trans. Netw. Serv. Manage., vol. 13, no. 4, pp. 725–739, Dec. 2016.
[4] O. Alhussein, P. T. Do, J. Li, Q. Ye, W. Shi, W. Zhaung, and X. Shen, “Joint VNF placement and multicast traffic routing in 5G core networks,” in Proc. IEEE GLOBECOM’18, to appear.
[5] L. Wang, Z. Lu, X. Wen, R. Knopp, and R. Gupta, “Joint optimization of service function chaining and resource allocation in network function virtualization,” IEEE Access, vol. 4, pp. 8084–8094, Nov. 2016.
[6] W. Wang, B. Liang, and B. Li, “Multi-resource generalized processor sharing for packet processing,” in Proc. ACM IWQoS’ 13, Jun. 2013, pp. 1–10.
[7] A. K. Parekh and R. G. Gallager, “A generalized processor sharing approach to flow control in integrated services networks: The single-node case,” IEEE/ACM Trans. Netw., vol. 1, no. 3, pp. 344–357, Jun. 1993.
[8] D. P. Bertsekas, R. G. Gallager, and P. Humblet, Data networks. Englewood Cliffs, NJ, USA: Prentice-hall, 1987, vol. 2.
[9] “OMNeT++ 5.0,” [Online]. Available: http://www.omnetpp.org/omnetpp.
[10] “Openstack (Release Pike),” [Online]. Available: https://www.openstack.org.

Qiang Ye (S’16-M’17) received his Ph.D. degree in electrical and computer engineering from the University of Waterloo, Waterloo, ON, Canada, in 2016. He is currently a Research Associate with the Department of Electrical and Computer Engineering, University of Waterloo, where he had been a Post-Doctoral Fellow from Dec. 2016 to Nov. 2018. His current research interests include AI and machine learning for future wireless networking, IoT, SDN and NFV, network slicing for 5G networks, VNF chain embedding and end-to-end performance analysis.

Weihua Zhuang (M’93-SM’01-F’08) has been with the Department of Electrical and Computer Engineering, University of Waterloo, Waterloo, ON, Canada, since 1993, where she is a Professor and a Tier I Canada Research Chair in Wireless Communication Networks. She is the recipient of 2017 Technical Recognition Award from IEEE Communications Society Ad Hoc & Sensor Networks Technical Committee, and a co-recipient of several best paper awards from IEEE conferences. Dr. Zhuang was the Editor-in-Chief of IEEE Transactions on Vehicular Technology (2007-2013), Technical Program Chair/Co-Chair of IEEE VTC Fall 2017 and Fall 2016, and the Technical Program Symposia Chair of the IEEE GLOBECOM 2011. She is a Fellow of the IEEE, the Royal Society of Canada, the Canadian Academy of Engineering, and the Engineering Institute of Canada. Dr. Zhuang is an elected member in the Board of Governors and VP Publications of the IEEE Vehicular Technology Society. She was an IEEE Communications Society Distinguished Lecturer (2008-2011).

Xu Li is a staff researcher at Huawei Technologies Inc., Canada. He received a Ph.D. (2008) degree in computer science from Carleton University. His current research interests are focused in 5G system design and standardization, along with 90+ refereed scientific publications, 40+ 3GPP standard proposals and 50+ patents and patent filings. He is/was on the editorial boards of the IEEE Communications Magazine, the IEEE Transactions on Parallel and Distributed Systems, among others. He was a TPC co-chair of IEEE VTC 2017 (fall) – LTE, 5G and Wireless Networks Track, IEEE Globecom 2013 – Ad Hoc and Sensor Networking Symposium.

Jaya Rao (M'14) received his Ph.D. degree from the University of Calgary, Canada, in 2014. He is currently a Senior Research Engineer at Huawei Technologies Canada, Ottawa. Since joining Huawei in 2014, he has worked on research and design of CIoT, URLLC and V2X based solutions in 5G New Radio. He has contributed for Huawei at 3GPP RAN WG2, RAN WG3, and SA2 meetings on topics related to URLLC, network slicing, mobility management, and session management.
Editors: Chih-Lin I and Haijun Zhang
Disruptive Models for Telecom Operators in a New Digital Ecosystem
Christian James Aguilar-Armenta, Federal Telecommunications Institute of Mexico, This email address is being protected from spambots. You need JavaScript enabled to view it.
IEEE Future Networks Tech Focus: Volume 2, Number 3, December 2018
Abstract
Because the new digital ecosystem implies the development of novel telecommunications services, both telecom operators and regulators are faced with new opportunities and challenges. It is thus necessary to understand the role that telecom operators will play in the value chain of new business models, their interactions with other stakeholders, as well as the potential regulatory impacts of all this. In this article we present an examination of some key innovative business models wherein operators are the main actors. Our data analysis leads us to conclusions about regulatory challenges and potential competition implications for 5G.
1. Introduction
In this article we examine how telecom operators (Telcos) and stakeholders are currently engaging in new business models fostered by the new digital ecosystem when providing services, so as to generate hypothesis about the competition impacts and regulatory implications that these might bring in years to come. We begin by presenting an analysis of the participation that Telcos have in current new business. Subsequently, we address the potential repercussions and challenges that these new business models represent for both operators and regulators.
2. New Digital Ecosystem
The new ecosystem has the potential to lure in both novel and extant participants of the digital world, increasing the participation of the latter with new services and innovative technologies in Telcos' value chain.
But, all in all, what makes this new ecosystem so attractive and promising? The most likely answer is the technologies that are essential for the development of 5G, which will bring different attributes compared to the current 4G networks, namely: massive MIMO, beam-forming, Software Defined Networking (SDN) and Network Function Virtualization (NFV). The last two in particular will allow the Network Slicing to meet specific needs with specific network attributes [1]. This capacity creates a number of possible services that we have not seen so far. These technologies, in combination with the massive deployment of small cells, will allow 5G networks to have the capacity to: 1) provide higher speed and broadband (xMBB); 2) support the massive connectivity of various devices (mMTC); and 3) provide connectivity with very low latency and with high level of reliability (uMTC) [1], the latter commonly known as URLLC.
This new digital ecosystem will allow the development not only of super connectivity services but it will also offer specific solutions across different sectors in both urban and rural areas. However, these opportunities will not only be presented to Telcos but to all the stakeholders involved in the ecosystem. It is right here where the new disruptive business models emerge and where the value chain will be modified due to the participation of more actors.
3. Methodology
A systematic review of a wide variety of sources was performed, aiming to pinpoint: 1) new business models for Telcos; 2) the competition implications; and 3) regulatory challenges. We focused on academic and telecom standardization bodies’ databases, Telcos’ official websites, informative, analytic or editorial texts published online by consulting agencies, as well as specialized news sites. Although the last three cannot be considered as scientific references, sometimes they were the only existing sources of information about newest business models. In order to narrow down our search to pertinent resources, we developed a boolean search combination of terms related to the new digital ecosystem (e.g. IoT, 5G, Big Data, AI, etc.), plus those pertaining to Telcos (e.g. network operators, communications service providers, etc.).
4. Results
So far, there is no launch of a large-scale 5G network in any country, there has only been pre-commercial testing of 5G services [2]. In spite of this, at present there are services of the new digital ecosystem that enable the development of new business models of which Telcos are the main providers.
We were able to identify 27 use cases in which operators are the main actors. It is important to note that the number of cases are not of primordial importance for this article. What is indeed substantive is the identification of new business models and, above all, the possibility to predict the potential competition and regulatory implications for the sector. Table 1, therefore, concentrates on only five representative use cases that are outside the universe of services that Telcos traditionally offer, in order to synthesize the most relevant information about these new business models. In the subsequent section, however, we expound on the competition and regulatory aspects that we consider require attention from the regulators, based on the analysis of the 27 use cases that we identified.
As a supplement to the results, Fig. 1 features a schematic of the 27 use cases that we identified, classified by groups, showing the sectors of greatest commercial interest for Telcos that they target [3]. This schematic is not a standard representation of the new business models that exist in the market today; it only shows the particular distribution of the use cases that we found.
Figure 1. Schematic representation of services by group and target sectors
Table 1. Selection of use cases
| Use cases | Service | Network Requirements | Business model |
|
IoT [4] |
Mobile network platform that provides connectivity, management and control for autonomous vehicles in South Korea. | Low latency; High reliability; High throughput; High availability; Connection density; Traffic volume density; Coverage (mobility); Security; Data analytics; AI. |
Marketing of the 5G self-driving technologies consisting in network capacity (28 GHz band), AI, sensors, and 3D HD maps by SK Telecom to provide connectivity, management and control of autonomous vehicles. SK Telecom in partnership with Nvidia and LG Electronics, as well as in collaboration with The Korean Transportation Safety Authority and the University of Seoul. |
| Big Data [5] | Telefonica’s Big Data service unit to provide an information analysis service to help its clients in decision-making and resource management processes. | Data analytics;
Cloud computing; |
Marketing of three Big Data business lines: 1) Business Insights: provides companies with anonymous and aggregated data collected by Telefonica’s networks; 2) Synergic Partners: provides analytical and consultancy data services; and 3) Big Data as a service: giving enterprises the means to make better use of their own data, using Telefonica’s cloud infrastructure. |
| Blockchain [6] | City Pass to pay multiple services such as bike sharing, tourist sites, libraries, etc. by means of a card or a mobile app that allows authentication and secure mapped direct transactions with the platform. | Low latency;
High availability; |
Marketing of the City Pass service by Deutsche Telekom to carry out direct, secure and decentralized digital transactions between the user and the platform. Open and independent system for the integration of more services. |
| AI [7] | Home device (speaker) based on voice recognition that works as a virtual assistant for smart home control services, music, weather and traffic information, e-commerce service and multimedia playback. | Cloud computing;
Data analytics; |
Marketing of the virtual assistance device by SK Telecom, with an open interface to incorporate other AI devices and services into the ecosystem. SK Telecom will also integrate other AI developers to strengthen the ecosystem. |
|
Media & Entertainment [8] |
Test of 5G commercial network in the Winter Olympic Games in South Korea to provide services such as: 1) 4K transmission and 360° vision; 2) VR; 3) massive connectivity of devices and control with Edge Computing; 4) high throughput; and 5) enhanced broadband. | High throughput;
High reliability; |
Marketing of 5G services by KT, Intel, Toyota, Samsung and Ericsson. In particular, Intel provides the FlexRAN platform and Edge Computing technology, as well as cloud computing and data center functions; Samsung and Ericsson, in direct collaboration with KT, provide the 5G network in the 28 GHz band. The network test paves the way for the operator to launch commercial 5G services. |
5. Regulatory Challenges and Potential Competition Implications
We seek to help regulators anticipate the needs to encourage investment by Telcos towards 5G success. In the following subsections we present a brief explanation of each of the aspects that we consider are of relevance to the authorities.
A. Regulatory Challenges
Spectrum. The new digital ecosystem requires spectrum classified into three general frequency ranges: <1 GHz, 1 - 6 GHz, and > 6GHz. The 600, 700, 800 and 900 MHz bands are important for the range below 1 GHz. The 3.4 - 4.2 GHz band is significant in the segment 1 - 6 GHz. Likewise, bands 1.4 and 2.5 GHz are important in this segment. The 26 and 28 GHz bands stand out among the frequencies above 6 GHz; however, there are others frequencies that are in the process of identification by the WRC-19 (i.e. 37- 43.5 GHz, 45.5 - 50.2 GHz, 66 - 76 GHz and 81 - 86 GHz).
It is also necessary to explore adequate models for assignment spectrum for both isolated areas (e.g. smart farming) and confined or delimited areas (e.g. smart factory) that require specific solutions. The use of unlicensed bands may not be sufficient for services that require greater security and reliability. We also consider it important to capitalize more from the secondary licenses of the spectrum, as well as from other spectrum sharing techniques at high frequencies that experience limited propagation and less interference.
Infrastructure. It is necessary to create adequate models for infrastructure sharing, mainly for indoor places in urban areas for small cell densification. Flexibility of new entrants who intend to market their infrastructure and spectrum could be another important factor.
Open architectures. In order to guarantee the interconnection and interoperability between networks, it is essential for regulators to be very attentive to the use of new technologies and to ensure both technological neutrality and the adoption of international standards among operators.
Quality of services. Quality standards will have to broaden their scope and not to be limited to throughput parameters. Several services would require clear quality standards, particularly those that require low latency, connection density, traffic volume density, high availability and reliability.
Service differentiation. In theory, Network Slicing will allow a Telco to provide various services with specific requirements through the same network without interfering the traffic and performance of the different services that are on the network. If so, regulators would have to establish clear rules to avoid violating the net neutrality, similar to the following: 1) the capacity of the network should be sufficient to provide specialized services in addition to any Internet Access Service (IAS) that is provided; 2) the specialized services are not used or offered as a replacement for the IAS; and 3) the specialized services should not diminish the availability or the quality of the IAS.
Ethical and legal regulation of AI systems. Security and privacy are the aspects that most concern people when using AI systems, particularly due to the lack of a clear ethical and legal scenario that limits the scope and responsibilities of these systems.
Delimitation of responsibilities. It is important to define the responsibilities of the participants in the value chain, as well as to be able to identify the responsible (e.g. AI systems).
Security, privacy and data protection. It is evident that digital data is the sine qua non of all digital services. Therefore, regulators should encourage the development of the new ecosystem while ensuring: 1) privacy or control over the dissemination of people‘s personal data; 2) the non-vulnerability of the data; and 3) protection through some type of security.
B. Competition implications
Association or vertical integration. The associations of Telcos with other stakeholders in the provision of a service turned out to be an option for most of the new business models that we found.
Possible entry barriers. The associations can generate entry barriers for other operators and suppliers of technology, equipment, platforms or applications.
Tariff differentiation per service. The lack of a clear tariff plan for new services that involve the connection of several devices could affect the balance between the cost-benefit that users acquired and the costs that the operators need to recover.
Possible distortion of neutrality to competition. It is essential that the participation of the Government does not generate distortions to the market because of its power over public property.
Possible barriers to access essential supplies. Big Data services use aggregated and anonymous data collected from Telcos’ network users as essential input. This could generate commercial disadvantages to other competitors if there is an incumbent providing these services.
6. Conclusions
The new digital ecosystem represents several significant changes in the creation, provision and commercialization of new telecommunications services. From our analysis of the new business models identified, we derive the following conclusions:
- The new business models are aimed at vertical industries, specific sectors and business niches that go beyond connectivity services;
- The new ecosystem represents business opportunities for all stakeholders of the digital world;
- The value chain can be modified upstream with the participation of new stakeholders that provide, for example, infrastructure for small cells, as well as downstream with the participation of intermedaries that offer services directly to the end user;
- In a very general way we consider that there are four possible participation scenarios for Telcos in the value chains: 1) they dominate the entire value chain and are responsible for providing both technology and services to end users; 2) they are the main actors of the value chain and are responsible for providing the service to end users; however, they require third-party specialists in the sector for the provision of technology and platforms; 3) they have the best technological network capabilities to support the specific requirements across different sectors, nonetheless they are not the ones who provide services to end users but intermediaries who know the sectors very well; and 4) they remain outside the value chain because technology developers, in collaboration with new specialists in the sector, have the ability to provide specific services to end users;
- The success of Telcos depends, among other things, on their ability to meet the specific requirements of users, the investment they make in their networks for the deployment of new capabilities, their strategy of participation in the value chain, and of their capacity to take advantage of all the wireless, fixed and satellite technologies that currently exist for the provision of mixed connectivity.
References
- A. Osseiran, J. F. Monserrat, and P. Marsch. “5G mobile and wireless communications technology”. Cambridge, UK: Cambridge University Press, 2016.
- D. Johnson, “5G Poised for Commercial Rollout by 2020”, IEEE Spectrum: Technology, Engineering, and Science News, 2018.
- K. Taga, R. Swinford, and G. Peres, “5G deployment models are crystallizing”, Arthur D Little, 2017.
- J. P. Tomás, “South Korea allows KT to test self-driving bus in Seoul”, Enterprise IoT Insights, 2018.
- J. P. Tomás, “Telefonica launches big data services unit”, Enterprise IoT Insights, 2016.
- C. Sentürk, and A. Ebeling, “City Pass – Blockchain”, Deutsche Telekom, 2018.
- J. P. Tomás, “SK Telecom unveils artificial intelligence service”, Enterprise IoT Insights, 2016.
- M. Dano. “KT’s millimeter wave 5G network transmitted 3,800 TB of data during Winter Olympics”, FierceWireless, 2018.
 Christian James Aguilar A. received his Ph.D. degree in Electronic Engineering from the University of York, UK. He holds a BSc in Telecommunications Engineering from the National Autonomous University of Mexico (UNAM). He has more than five years of experience in the Telecom industry, public sector and research. Currently his is a researcher at the Federal Telecommunications Institute (IFT) of Mexico. Previously, he was the technical adviser of former Commissioner Adriana Labardini of IFT, a post he held for over three years. His latest research project revolves around disruptive business models for Telcos in the 5G ecosystem. He has published various scientific articles, among which stands one entitled: ‘Cantilever RF-MEMS for Monolithic Integration with Phased Array Antennas on a PCB’.
Christian James Aguilar A. received his Ph.D. degree in Electronic Engineering from the University of York, UK. He holds a BSc in Telecommunications Engineering from the National Autonomous University of Mexico (UNAM). He has more than five years of experience in the Telecom industry, public sector and research. Currently his is a researcher at the Federal Telecommunications Institute (IFT) of Mexico. Previously, he was the technical adviser of former Commissioner Adriana Labardini of IFT, a post he held for over three years. His latest research project revolves around disruptive business models for Telcos in the 5G ecosystem. He has published various scientific articles, among which stands one entitled: ‘Cantilever RF-MEMS for Monolithic Integration with Phased Array Antennas on a PCB’.
Editor:
 Siming Zhang received the dual BEng degrees with the highest Hons. from the University of Liverpool (UK) and Xi’an JiaoTong and Liverpool University (XJTLU, China) respectively in 2011. She obtained her M.Sc with distinction and her Ph.D. degree from the University of Bristol (UK) in 2012 and 2016. She then joined China Mobile Research Institute and currently works on research areas ranging from Massive MIMO and mmWave, channel measurements and modeling, conductive testing and prototype development. She has been an active member of the IEEE Communications Society and IEEE Young Professionals. She serves as the Associate Managing Editor of the IEEE 5G Tech Focus. She is the co-lead on the PoC project in the NGMN Trial and Testing Initiative. She is the TPC for IEEE ISCC2017. She has received numerous awards for her outstanding achievements during her study and her career.
Siming Zhang received the dual BEng degrees with the highest Hons. from the University of Liverpool (UK) and Xi’an JiaoTong and Liverpool University (XJTLU, China) respectively in 2011. She obtained her M.Sc with distinction and her Ph.D. degree from the University of Bristol (UK) in 2012 and 2016. She then joined China Mobile Research Institute and currently works on research areas ranging from Massive MIMO and mmWave, channel measurements and modeling, conductive testing and prototype development. She has been an active member of the IEEE Communications Society and IEEE Young Professionals. She serves as the Associate Managing Editor of the IEEE 5G Tech Focus. She is the co-lead on the PoC project in the NGMN Trial and Testing Initiative. She is the TPC for IEEE ISCC2017. She has received numerous awards for her outstanding achievements during her study and her career.
The Levels of Intelligence of Mobile Networks and Consideration of Architecture Evolution
Yan Wang, Hua Huang, Yingzhe Li, Wei Zhou, Wireless Network Research Department, Huawei Technologies, Shanghai, China
{jason.wangyan, hua.huang, yingzhe.li, will.zhou} @huawei.com
Chih-Lin I, Qi Sun, Siming Zhang, China Mobile Research Institute, Beijing, China
{icl, sunqiyjy, zhangsiming} @chinamobile.com
IEEE Future Networks Tech Focus: Volume 2, Number 3, December 2018
Abstract
The rejuvenation of AI technology provides a new way to solve the increasingly complex and difficult problems in the 5G network, which makes the network more intelligent and autonomic. This field has gradually become a hot topic both in the academia and industry. But the industry has not yet reached a unified definition of an intelligent mobile network, and how to measure and judge the level of intelligence. This paper attempts to give the definition of the levels of mobile network intelligence and analyzes the influence of intelligence on the evolution of wireless network architecture, hoping to help the industry to reach consensus.
1. The state of the art of the mobile network with AI
In the evolution process from 4G to 5G, the performance and flexibility of wireless networks have changed fundamentally. For the performance, to support the three typical services of enhanced Mobile Broad Band (eMBB), massive Machine Type Communications (mMTC) and Ultra-Reliable and Low Latency Communication (URLLC), 5G network introduces advanced technologies such as large-scale antenna array, flexible air interface and Non-Orthogonal Multiuser Access technology to meet the more stringent technical requirements in terms of peak rate, spectrum efficiency, low delay, high reliability, connection density. For the flexibility, various decoupling are happened in the 5G architecture, such as software and hardware decoupling for the Network Function Virtualization (NFV), control and forward decoupling for the gateway, control plane function decomposition, Central Unit (CU) and Distributed Unit (DU) separation of Radio Access Network (RAN), etc. This makes network functions easier to deploy on the cloud computing platform, enabling automated orchestration and deployment of network functions to provide efficient network slicing services for different vertical application requirements.
Although 5G has brought a qualitative leap in performance and flexibility, the richer KPI dimensions, flexible air interface, virtualization of network function and the introduction of slicing technology lead to the utmost complexity and challenges of the design, deployment operation and optimization of the 5G network. Artificial Intelligence (AI) technology, which is rejuvenated by the great development of big data, deep learning and cloud computing, provides a data driven methodology worthy of exploration for solving the complicated problems that 5G network faces [1]. The application of AI to wireless networks has attracted more and more attention in the academic field. There are many research literatures in AI assisted New Radio (NR) resource allocation, cloud resource management, receiver design, channel parameter estimation and so on[2][3][4][5].
However, mobile network empowered by AI is not a single point technology or internal implementation problem but requires systematic thinking on the architectural level. 5G Americas proposed that orchestration, analytics and automation enabled by AI or Machine Learning (ML) will play a key role in 5G network [6]. Some research projects of 5G Infrastructure Public Private Partnership (5GPPP) tries to use AI and ML to a achieve real time autonomous 5G network management [7][8][9]. Many pre-standard and standardization organizations have carried out discussions and research items on network intelligence based on Big data and AI technology. For example, the European Telecommunications Standards Institute (ETSI) set up the Experiential Network Intelligence Industry Specification Group (ENI ISG) and the Zero touch network and Service Management Industry Specification Group (ZSM ISG) focusing on intelligent closed loop policy and fully automatic network management, respectively[10][11]. ITU-T set up Focus Group on Machine Learning for Future Networks including 5G (FG-ML5G) investigating on valuable use cases, data model and algorithms, and network intelligent architecture [12]. 3GPP has approved data driven related study items, e.g., Enables of Network Automation in 3GPP SA2 working group [13] and RAN-Centric Data Collection and Utilization in 3GPP RAN3 working group [14].
2. The Lack of unified definition for mobile network intelligence
Currently different organizations and research institutions have different views on the application of AI into the mobile network. They pay more attention to the specific layer or domain in which the AI or Big data can be used to improve the efficiency and performance, making the research relatively fragmented. For instance, ETSI ENI ISG mainly focuses on policy architecture, ETSI ZSM ISG focuses on management, 3GPP focuses on control plane and Self-Organized Network (SON), and academic community pays more attention to the physical layer and new application scenarios (such as cache in wireless network).
Can the mobile network be considered as intelligent when the AI is only used in mobile networks to solve certain specific problems at certain specific layer or domain? Let's first examine the following questions:
- Is AI enabled operation and maintenance an intelligent network? The intelligent operation and maintenance is the primary value of the AI for network. AI helps to improve the optimization of parameter configuration and the efficiency of fault prediction and diagnosis, minimize the manual intervention and reduce OPEX. However, intelligent operation and maintenance only maintains the existing network to its best level and does not make the network itself to have intelligence such as context awareness, service awareness, and automatic policy control and resource scheduling.
- Is AI enabled SON an intelligent network? Self-Organizing Network (SON), defined by 3GPP, includes self-configuration, self-optimization and self-healing. In fact, it has embodied the characteristics of network intelligence. But 3GPP's definition of SON is limited to certain specific features, such as the Automatic Neighbor Relation (ANR), Mobility Load Balancing (MLB), Mobility Robustness/Handover Optimization (MRO), Inter-Cell Interference Coordination (ICIC), Coverage and Capacity Optimization (CCO), Cell Outage Detection (COD), Cell Outage Compensation (COC) and so on [15]. These SON features usually designed independently and heavily rely on the standardization resulting in a bundle of chimney-like features. AI enabled SON may be just a better SON, but it won’t change its limited scenarios and dependence on the standard process.
- Is AI enabled Radio Resource Management (RRM) or Radio Transmission Technology (RTT) an intelligent network? Recently, academic community have tried to study AI technology in radio resource management level and physical level, such as Adaptive Modulation and Coding (AMC), Massive MIMO beam forming, etc., to exploit potential performance with reduced complexity [16]. For these research, AI is more of an auxiliary means of existing algorithm or an alternative to the traditional algorithm, which cannot be regarded as a system-level intelligence from the whole network perspective.
In summary, the use of AI technology at any layer or domain of the mobile network can solve some complex problems and bring a certain degree of intelligence, which unfortunately does not demonstrate the intelligence of the whole network. Network intelligence should be a system-level concept, not a single function. This leads to several further questions:
- What is the ultimate goal of realizing wireless network intelligence with AI?
- How to evaluate the level of wireless network intelligence?
- What is the impact of different level of intelligence on the existing wireless network architecture?
- How will the network architecture evolve towards the goal of intelligence?
3. The definition of mobile network intelligence
The grading definition of automated driving provides a good reference for us to understand and judge the levels of intelligence of mobile networks. To unify the understanding of the concept of automated driving in the whole industry, the SAE (International Automotive Engineering Society) J3016 document provides a taxonomy with detailed definitions for 6 levels of driving automation [17]. The proposal has become a widely accepted standard in the vehicle industry and is used to guide the vehicle industry to carry out five phases of work for driving automation in stages [17].
Introducing intelligence into vehicles achieves fully automated driving, while the goal of wireless network intelligence is the "network autonomy". The network can automatically deploy, configure, and optimize by itself to achieve target KPI according to the intention of the operators, and can automatically avoid or solve abnormal events to ensure the security and reliability of the network. But the ultimate objective of full autonomy cannot be achieved overnight. It needs to be implemented step by step. Borrow the idea from SAE, we also need to define several features related to the level of mobile network intelligence and determine the level of network intelligence by analyzing the degree of substitution for AI subsystem with the defined features.
Here we try to give 7 features for investigating network intelligence levels:
- Context awareness and analysis. It is to tell what happened inside the network and what is the root cause;
- Non-real time prediction and inference. It is to judge what will happen in the network management plane in future (maybe several minutes or hours later);
- Decision-making and execution. It is to make policy and take control measures automatically based on the prediction and reasoning;
- Real-time prediction and inference. It mainly aims at prediction and inference at milliseconds or microsecond scale at L1-L3 layer of RAN with real-time control and scheduling;
- Exception handling. It refers to the handling of sudden or extreme events and recovery from abnormal outage;
- Human-Network Interface. It refers to whether operator interact with the network through traditional specialized signaling or command interaction, or through intention-based interface;
- Applicable scenarios. It refers to whether the intelligent scenarios cover specific functionalities, specific services, or integrated scenarios in the complete network life cycle.
Based on the degree of substitution for the AI subsystem in the 7 defined features, we can classify the intelligence of the mobile network into 6 levels, as shown in Figure 1.
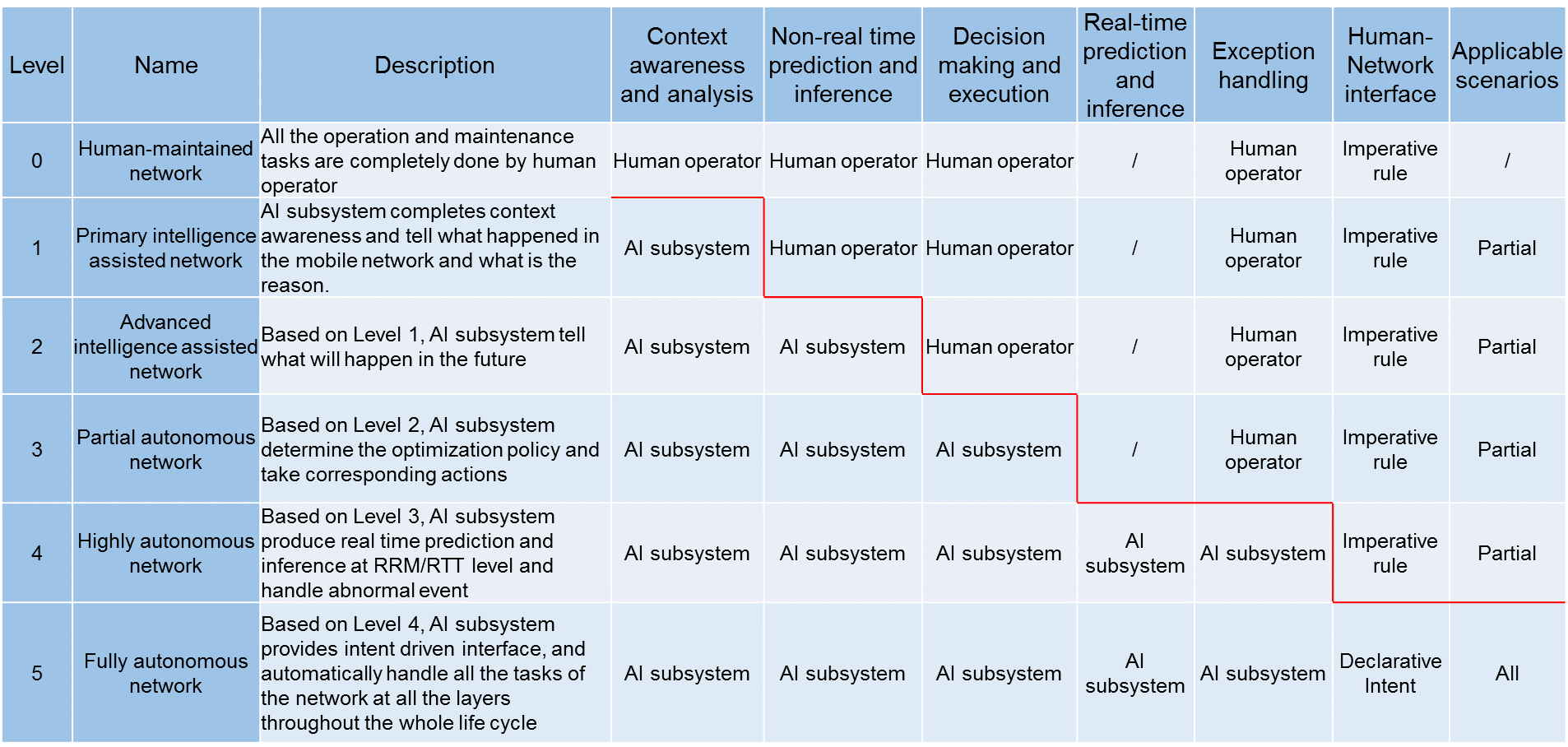
Figure 1. The levels of mobile network intelligence
As shown in Fig. 1, the higher the level of network intelligence, the more work of human operators are replaced by AI subsystems in the 7 features. It is worth noting that a certain level of intelligence is reached only when all the features of this level are implemented by the AI subsystem. For example, to achieve level 2 intelligence, the AI subsystem must simultaneously support feature 2 and feature 3. However, if the AI subsystem only supports part of the feature required, it cannot be regarded as Level 4 intelligence.
The benefits of such intelligence grading are as follows:
- It helps the industry to reach a consensus of the definition of intelligent wireless networks;
- It provides some criteria for judging the development level of the wireless network intelligence;
- It provides decision-making basis for the government, operators, equipment vendors and other related industry partners to do technology selection, product planning, etc.
4. The impact on the mobile network architecture evolution
Introducing Big data and AI technology into wireless networks to achieve network intelligence will definitely impact the existing mobile network architecture. We believe that AI subsystems will be introduced in the three domains of the network, i.e., the Operations Support System (OSS) plane, the Core Network (CN), and the Radio Access Network (RAN.) 3GPP has approved two study items related to network data analysis, i.e., Enabler of Network Automation in SA2 and RAN-Centric Data Collection and Utilization in RAN3, which will accelerate the standardization pace. The core network side has defined the Network Work Date Analysis (NWDA) function as the hosting entity of big data and AI subsystem. The RAN side study item which approved in June may also study the possibility of introducing a Radio Data Analytics (RDA) function (i.e. NWDA-like functional entities) on the RAN side.
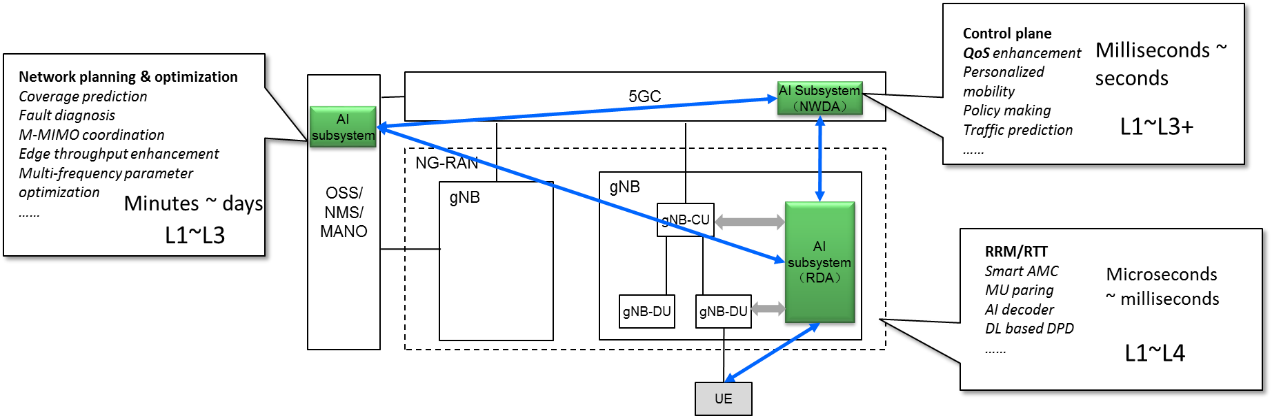
Figure 2. The introduction of AI subsystem in the 3GPP network architecture
The application scenarios and intelligent level that each domain requires are different, as shown in Figure 2. At the OSS, it usually covers the network planning related use cases, including coverage prediction, fault diagnosis, cell edge throughput enhancement, and virtual grid based multi frequency parameter optimization and so on. The prediction is non-real-time and usually beyond minutes’ level. According to the aforementioned intelligent level definition, the OSS intelligence can reach level 3 at the most because it cannot achieve near-real-time and real-time prediction and inference needed at the control layer and the physical layer. 5G CN with introduced AI subsystem can achieve control plane related intelligent scenarios, such as the intelligent QoS control, the personalized mobility management, the load-balance of the Virtualized Network Function (VNF), network traffic prediction, etc. The prediction timescale is usually larger than second level. Since the core network cannot handle the real-time resource control at the TTI level in RAN, the core network intelligence can reach level 3 or at most level 4. If the AI subsystem is introduced in the RAN, it can handle the near real-time and real-time RRM/RTT related intelligent scenarios, including Smart AMC, intelligent multiuser Pairings, AI decoders, deep learning based digital pre-distortion, etc., and the prediction timescale can be even reduced to the microsecond level. It is possible to realize intelligence of level 4 at most since only the scenarios within RAN are considered.
Only when the AI subsystems of all three domains collaborate, the network intelligence of level 5, i.e., the fully autonomous network, can be reached.
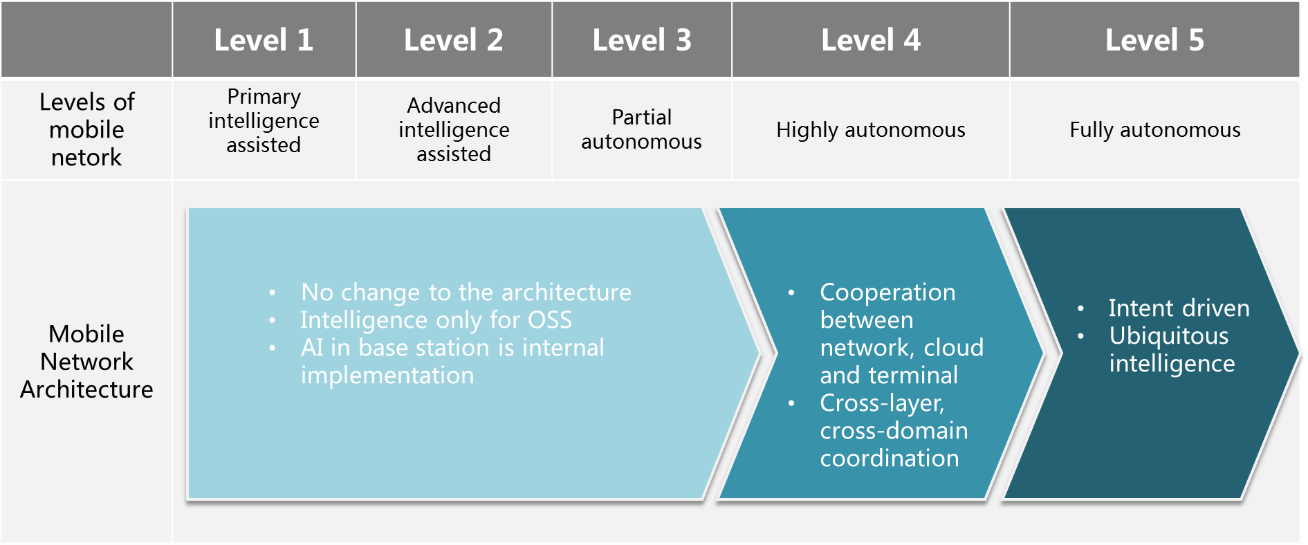
Figure 3. The architecture evolution map according to the network intelligenct levels
Based on the above analysis, Figure 3 shows the relationship between the architecture evolution and network intelligent grading. If only the network intelligence or autonomy of L1~L3 level is needed, there is no impact on the 3GPP network architecture, and the intelligence is mainly embodied in the OSS, or the management and orchestration layer. At this stage if the AI technology is utilized to improve the performance and efficiency within base station, since this is only an internal implementation issue, there is still no need for architectural support.
However, if we need to achieve intelligence above level 3, network architecture is required to be upgraded. To achieve Level 4 intelligence, we need to further introduce AI subsystem in CN and RAN to increase near-real-time and real-time prediction and reasoning capabilities. In addition to the interaction between the three AI subsystems, it may be necessary to interact between the wireless network AI system, cloud platform and UE to achieve cross-layer or cross-domain coordination, thereby significantly expanding the network intelligent application scenarios. For the Level 5 intelligence, the AI will be already a ubiquitous capability of the network, and it will bring about a fundamental change in the human-network interface, realizing an intent-driven network, free of manual operation and maintenance. To realize the network intelligence of Level 4-5, the network architecture will have great changes in functions, interfaces and procedures, as well as innovations in chips and algorithms.
5. Conclusions
The introduction of AI into mobile networks has been highly expected by the industry for solving complex problems at various network levels, and ultimately enabling an intelligent and fully autonomous network. This paper attempts to give a definition and grading of mobile network intelligence from a research perspective. We propose a taxonomy with detailed definitions for 6 levels of intelligence and 7 key features to be fulfilled. Hopefully such discussion will serve as an anchor in reaching a unified understanding of the definition of intelligent mobile networks and its evolution path to the ultimate intelligence and autonomy. Although this paper proposes intelligent grading for mobile networks, the conclusion is also applicable to the definition of general network intelligence. The current thinking is still relatively elementary. We welcome contribution and discussion from academic community and industrial organization to further improve the taxonomy of the intelligence grading for mobile networks.
References
- You X H, Pan Z W, Gao X Q, et al. The 5G mobile communication: The development trends and its emerging key techniques. Sci Sin Inform, 2014, 44 (5): 551-563 [. 5G. 2014, 44 (5):551-563
- Wang T, Wen C K, Wang H, et al. Deep learning for wireless physical layer: Opportunities and challenges[J]. China Communications, 2017, 14(11): 92-111.
- Tang P, Li F, Zhou W, et al. Efficient auto-scaling approach in the telco cloud using self-learning algorithm[C]//Global Communications Conference (GLOBECOM), 2015 IEEE. IEEE, 2015: 1-6.
- Zhou W. TCRM: Telco Cloud Resource Management Using Real-Time Data Analysis[C]//Cloud Computing Technology and Science (CloudCom), 2016 IEEE International Conference on. IEEE, 2016: 480-481.
- O’Shea T, Hoydis J. An introduction to deep learning for the physical layer [J]. IEEE Transactions on Cognitive Communications and Networking, 2017, 3(4): 563-575.
- 5G Americas white paper. 5G Network Transformation. http://www.5gamericas.org/files/3815/1310/3919/5G_Network_Transformation_Final.pdf
- SELFNET. Framework for Self-Organized Network Management in Virtualized and Software Defined Networks. [Online]. Available: https://5g-ppp.eu/selfnet/
- CogNet. Building an Intelligent System of Insights and Action for 5G Network Management. [Online]. Available: https://5g-ppp.eu/cognet/
- SESAME. Small cEllS coordinAtion for Multi-tenancy and Edge services. [Online]. Available: https://5g-ppp.eu/sesame/
- ETSI ENI White paper, Improved operator experience through Experiential Networked Intelligence, https://www.etsi.org/images/files/ETSIWhitePapers/etsi_wp22_ENI_FINAL.pdf
- ETSI ZSM ISG White paper, Zero-touch Network and Service Management, https://portal.etsi.org/TBSiteMap/ZSM/OperatorWhitePaper
- ITU-T FG ML5G ToRs, https://www.itu.int/en/ITU-T/focusgroups/ml5g/Documents/FG-ML5G_ToRs.docx
- 3GPP Study of Enablers for Network Automation for 5G (Release 16), 3GPP TR 23791
- 3GPP New Study Item Proposal, RAN Centric Data Collection and Utilization, RP-181456
- 3GPP, “Technical Specification Group Services and System Aspects; Telecommunication Management; Self-Organizing Networks (SON); Concepts and requirements (Release 13),” 3GPP, TS 32.500, v13.0.0,
- N. Samuel, T. Diskin, and A. Wiesel, "Deep MIMO detection," IEEE 18th Int. Workshop Signal Process. Advances Wireless Communication (SPAWC), pp. 690–694, 2017.
- https://www.sae.org/standards/content/j3016_201401/preview/
 Yan Wang received his Ph.D. degree from the department of Electronic Engineering, Shanghai Jiao Tong University, China, in 2009. He is a principal engineer at Huawei Technologies in Shanghai, China. He has led many research projects on the mobile network evolution, including EPC enhancement, NFV, SDN, CU separation, service chaining, MEC mobility, Mobile LAN etc. Many of the research outputs have contributed to the 3GPP 4G and 5G standards. He is now leading a team of future network evolution research and prototype, and he is also the leader of architecture group of Wireless Artificial Intelligence Alliance. His current interesting of study includes intelligent mobile network enabled by big data and Artificial Intelligence, as well as mobile deterministic networks
Yan Wang received his Ph.D. degree from the department of Electronic Engineering, Shanghai Jiao Tong University, China, in 2009. He is a principal engineer at Huawei Technologies in Shanghai, China. He has led many research projects on the mobile network evolution, including EPC enhancement, NFV, SDN, CU separation, service chaining, MEC mobility, Mobile LAN etc. Many of the research outputs have contributed to the 3GPP 4G and 5G standards. He is now leading a team of future network evolution research and prototype, and he is also the leader of architecture group of Wireless Artificial Intelligence Alliance. His current interesting of study includes intelligent mobile network enabled by big data and Artificial Intelligence, as well as mobile deterministic networks
 Hua Huang is the director of Huawei Mobile Broadband Network Research Department. He is also the chief expert of the wireless architecture research in Huawei. Mr. Hua graduated from Zhejiang University with a Master degree in telecom science in June 1996 and joined Huawei in 2000. From 2000 till 2003, Hua is a senior engineer in Huawei 3G product, responsible for the system design of packet domain equipment. From September 2003 till April 2006, Mr. Hua was the leader of Huawei 3GPP SA2 Standard team and responsible for the system and architecture evolution standard research. He also joins the 3GPP TSG-SA plenary as delegate. Since 2006, Mr. Hua was responsible for Huawei wireless research as a director in access network and architecture areas. His current research is focused on the future wireless architecture, including AI, Big data, SDN, NFV, Cloud Computing, Open source, and other technologies, he is in charge of 5G architecture researches, and also lead the wireless AI research team in Huawei.
Hua Huang is the director of Huawei Mobile Broadband Network Research Department. He is also the chief expert of the wireless architecture research in Huawei. Mr. Hua graduated from Zhejiang University with a Master degree in telecom science in June 1996 and joined Huawei in 2000. From 2000 till 2003, Hua is a senior engineer in Huawei 3G product, responsible for the system design of packet domain equipment. From September 2003 till April 2006, Mr. Hua was the leader of Huawei 3GPP SA2 Standard team and responsible for the system and architecture evolution standard research. He also joins the 3GPP TSG-SA plenary as delegate. Since 2006, Mr. Hua was responsible for Huawei wireless research as a director in access network and architecture areas. His current research is focused on the future wireless architecture, including AI, Big data, SDN, NFV, Cloud Computing, Open source, and other technologies, he is in charge of 5G architecture researches, and also lead the wireless AI research team in Huawei.
 Yingzhe Li received the Ph.D. degree from Shanghai Institute of Microsystem and Information Technology, Chinese Academy of Sciences, China, in 2011. He is a principal engineer at Huawei Technologies in Shanghai, China. He has research on the algorithm of Self-Organizing Networks, such as network optimization, Mobility robust optimization. Now He focuses on the applications of Artificial Intelligence in wireless networks.
Yingzhe Li received the Ph.D. degree from Shanghai Institute of Microsystem and Information Technology, Chinese Academy of Sciences, China, in 2011. He is a principal engineer at Huawei Technologies in Shanghai, China. He has research on the algorithm of Self-Organizing Networks, such as network optimization, Mobility robust optimization. Now He focuses on the applications of Artificial Intelligence in wireless networks.
 Wei Zhou (M’15) received his Ph.D. degree from the department of Electrical Engineering and Information Systems, University of Science and Technology of China, in 2009. Currently, he is a Principal Engineer in Huawei Technologies Co., Ltd. His research interests include wireless communication, wireless Intelligence, machine learning and big data in next generation mobile network.
Wei Zhou (M’15) received his Ph.D. degree from the department of Electrical Engineering and Information Systems, University of Science and Technology of China, in 2009. Currently, he is a Principal Engineer in Huawei Technologies Co., Ltd. His research interests include wireless communication, wireless Intelligence, machine learning and big data in next generation mobile network.
 Chih-Lin I received her Ph.D. degree in electrical engineering from Stanford University. She has been working at multiple world-class companies and research institutes leading the R&D, including AT&T Bell Labs; Director of AT&T HQ, Director of ITRI Taiwan, and VPGD of ASTRI Hong Kong. She received the IEEE Trans. COM Stephen Rice Best Paper Award, is a winner of the CCCP National 1000 Talent Program, and has won the 2015 Industrial Innovation Award of IEEE Communication Society for Leadership and Innovation in Next-Generation Cellular Wireless Networks.
Chih-Lin I received her Ph.D. degree in electrical engineering from Stanford University. She has been working at multiple world-class companies and research institutes leading the R&D, including AT&T Bell Labs; Director of AT&T HQ, Director of ITRI Taiwan, and VPGD of ASTRI Hong Kong. She received the IEEE Trans. COM Stephen Rice Best Paper Award, is a winner of the CCCP National 1000 Talent Program, and has won the 2015 Industrial Innovation Award of IEEE Communication Society for Leadership and Innovation in Next-Generation Cellular Wireless Networks.
In 2011, she joined China Mobile as its Chief Scientist of wireless technologies, established the Green Communications Research Center, and launched the 5G Key Technologies R&D. She is spearheading major initiatives including 5G, C-RAN, high energy efficiency system architectures, technologies and devices; and green energy. She was an Area Editor of IEEE/ACM Trans. NET, an elected Board Member of IEEE ComSoc, Chair of the ComSoc Meetings and Conferences Board, and Founding Chair of the IEEE WCNC Steering Committee.
She was a Professor at NCTU, an Adjunct Professor at NTU, and an Adjunct Professor at BUPT. She is the Chair of FuTURE 5G SG, an Executive Board Member of GreenTouch, a Network Operator Council Founding Member of ETSI NFV, a Steering Board Member and Vice Chair of WWRF, a Steering Committee member and the Publication Chair of IEEE 5G Initiative, a member of IEEE ComSoc SDB, SPC, and CSCN-SC, and a Scientific Advisory Board Member of Singapore NRF. Her current research interests center around “From Green & Soft, to Open & Smart”.
 Qi Sun received the B.S.E. and Ph.D. degree in information and communication engineering from Beijing University of Posts and Telecommunications in 2009 and 2014, respectively. After graduation, she joined the Green Communication Research Center of the China Mobile Research Institute. She has published over 20 conference and journal papers and over 20 patent applications. Her research focuses on 5G and 5G+ technologies, including wireless big data driven intelligent RAN optimization, network resource management, non-orthogonal multiple access, etc.
Qi Sun received the B.S.E. and Ph.D. degree in information and communication engineering from Beijing University of Posts and Telecommunications in 2009 and 2014, respectively. After graduation, she joined the Green Communication Research Center of the China Mobile Research Institute. She has published over 20 conference and journal papers and over 20 patent applications. Her research focuses on 5G and 5G+ technologies, including wireless big data driven intelligent RAN optimization, network resource management, non-orthogonal multiple access, etc.
 Siming Zhang received her Ph.D. degree in wireless communications from the University of Bristol (UK) in 2016. She currently works at the Green Communications Research Center in China Mobile Research Institute (Beijing). She is one of the co-leads on NGMN Trial and Testing Initiative. She is also co-leading WG1 of the Wireless Artificial Intelligence Alliance. She is the Associate Managing Editor of the IEEE 5G Tech Focus Journal. Her current research interests include PHY layer design on Massive MIMO and mmWave, especially on channel modeling and prototyping, wireless big data analysis, and AI application in the RAN domain.
Siming Zhang received her Ph.D. degree in wireless communications from the University of Bristol (UK) in 2016. She currently works at the Green Communications Research Center in China Mobile Research Institute (Beijing). She is one of the co-leads on NGMN Trial and Testing Initiative. She is also co-leading WG1 of the Wireless Artificial Intelligence Alliance. She is the Associate Managing Editor of the IEEE 5G Tech Focus Journal. Her current research interests include PHY layer design on Massive MIMO and mmWave, especially on channel modeling and prototyping, wireless big data analysis, and AI application in the RAN domain.
Editor: Panagiotis Demestichas
On Consideration of the RAN Slicing - From the Operator's Perspective
Chih-Lin I, Junshuai Sun, Xingyu Han, Yingying Wang, Xueyan Huang, Green Communication Research Center, China Mobile Research Institute
{icl, sunjunshuai, hanxingyu, wangyingying, huangxueyan} @chinamobile.com
IEEE Future Networks Tech Focus: Volume 2, Number 3, December 2018
Abstract
5G provides the capability to support various services, which means the original one-size-fits-all architecture and functions cannot satisfy the diversified requirements of different scenarios. As one of the most promising service-oriented technologies, end-to-end network slicing was put forward to support the 5G provisions. As a vital part of the end-to-end slicing, the RAN slicing is still under-developed. This article provides a detailed investigation on the RAN slicing with functional explorations and operational procedures, hoping to give heuristic approaches to the implementation of the RAN slicing.
Keywords: RAN slicing, OAM, QoS
1. Introduction
The 5G era is coming near. As an evolutional generation of the mobile network compared to 4G, 5G is required to support vertical industrial scenarios, which gives 5G the strong capability to explore the blue sea of the telecommunication industry. Consequently, the whole network is demanded to become more service-driven and user-centric. Under this circumstance, end-to-end network slicing was proposed to satisfy the above-mentioned characteristics of the new network.
From the operator’s perspective, the end-to-end mobile network is made up of three parts: the core network (CN), the transmission network (TN) and the radio access network (RAN). According to the current progress of standardization on slicing, the detailed description on the network slicing in CN has been adopted by 3GPP SA2 in TS23.501 [1]. In addition, ITU-T SG-15 recently approved the proposal on the Slicing Packet Network (SPN) [2] as a candidate scheme of TN for further study. Compared to the rapid standardization pace in CN and TN, the work on the RAN slicing is comparatively slow in progress.
Different from CN and TN, the characteristic of the air interface indicates that the sharing of radio resources provides the most efficient way of resource utilization, which is still the design logic of 5G New Radio (NR), i.e., 5G RAN. Although 3GPP RAN3 has given several solutions on the setup procedure for the RAN slicing instance in the Study Item (namely, TR38.801 [3]), this topic is still controversial, especially on the detailed descriptions of the supported functions, let alone considering the interaction with Operation, Administration and Maintenance (OAM) entity.
2. Why investigate RAN slicing?
One may argue that there’s no need to adopt the RAN slicing, which can be replaced by precise QoS manipulation of Data Radio Bearers (DRBs) without breaking the design logic of resource sharing. In fact, it cannot be denied that the sharing on resources including calculation, storage, radio and frequency maximizes the network utilization. After the introduction of the RAN slicing, the base-stations have to be able to configure more dedicated resources, which may have an impact on the resource exploitation. From the perspective of operators, however, providing customized services in terms of dedicated resources indicates a possibility to improve the Quality-of-Experience (QoE) for users, compared to the strategy of the total resource sharing. In addition, the RAN awareness of the slice information is suitable for the adoption of the user-centric network, enabling the RAN to make better scheduling judgment, which trades off between the resource utilization and the user satisfaction.
It should be noted that several attempts on Proof-of-Concept (PoC) tests on the RAN slicing have been carried out in academia [4]-[6], including the theoretical analysis, the algorithmic investigation, and the prototype demonstration, etc. All of them have shown remarkable performance improvement, which indicates the practicability of the RAN slicing; however, none of them have provided a systematic exploration on the feasible functions for the RAN slicing, nor did they propose any operational procedures. As a result, this article is aiming at offsetting these gaps by providing detailed discussions in the following two parts.
3. Functional exploration for the RAN slicing
In this part, the possible functions related to the RAN slicing are explored on the gNB (i.e. the base-station of 5G NR) side not only in terms of services, but also in terms of the OAM, which could be constructive to operators. The basic framework for the functional exploration is shown in Fig.1.
Fig. 1: The proposed functions related to the RAN slicing
Firstly, the OAM-related functions are discussed, which can be further divided into Equipment Management (EM), Network Management (NM) and Deployment Management (DM), etc. The detailed descriptions are given below:
- EM: With the introduction of the RAN slicing, the operators should be able to perform the slice-level EM besides the classical OAM functions such as equipment status monitoring. In addition, when the system is evolved to the cloud platform, the OAM should be able to independently manage multiple Network Functions (NFs), which may be operated on the same general device but belong to different slices. In a word, EM should be able to achieve administration and control of all types of devices if the RAN slicing is adopted.
- NM: NM is responsible for the partition and distinction of applicable scopes for different slices while maintaining the isolation of NFs. In order to reflect the idea of user-centric network, it is inspiring for the RAN to decouple NFs from classical network entities. Therefore, the vertical industrial slice and the common communication slice can be implemented by two independent sets of NFs, which brings convenience compared to the management of network entities.
- DM: DM is in charge of the deployment of NFs or network entities according to the requirement of the slice from CN. For example, for URLLC slices, the functions of the protocol stack should be deployed on devices which are close to the air interface as much as possible, in order to guarantee the low latency of the transmission. In a word, the deployment ways are diversified for NFs, and most importantly, DM needs to ensure the accuracy and the stability on controlling the NFs.
Secondly, the service-related functions are investigated, which is composed of User Management (UM), Function Management (FM), Radio Management (RM) and QoS Management (QM). The separate descriptions are obtainable as follows:
- UM: UM is in charge of the storage and the maintenance of UE context according to the characteristics of users and the slice information. In addition, UM is responsible to perform differentiated configurations for Radio Bearers (RBs) and Cell Groups (CGs). If a specific user is configured with multiple slices which belong to different network tenants, UM should be able to achieve the isolation and the security protection of the user information, while satisfying different targeting requirements for different tenants.
- FM: FM provides the differentiated settings on functions of the protocol stack for different slices. For example, for URLLC slices, the Duplication function should be configured at the PDCP layer in order to satisfy the ultra-high reliability; while for mMTC slices, the DRX function with differentiated settings should be adopted and separately configured in order to satisfy different levels of energy-saving. The extension is driven by use cases, which provides sufficient space for further exploration.
- RM: As mentioned above, the adoption of the RAN slicing introduces possible management on dedicated resources, and the adaptation to which requires the concept redefinition and the algorithmic improvement. For example, since the adopted 100MHz bandwidth is sometimes too much for a service, the whole bandwidth can be partitioned into several smaller service-oriented bandwidth parts based on the slice information. In addition, RM should also support the soft isolation of bandwidth parts subject to different tenants.
- QM: QM is responsible to provide reasonable slice-level QoS profiles. In addition, for new slice type provided by a tenant, QM needs to realize the feasible quantified QoS definition within the scope of RAN, according to the OAM-related weight for this tenant and QoS Flow/DRB (Data Radio Bearer)-level QoS profiles within the slice, and guarantees the QoS characteristics of this slice.
In summary, the above analysis aims at inspiring the work on the functional exploration subject to the RAN slicing, and the feasible functions are not restricted to ones listed above; hopefully more extensions could be introduced for further study.
4. The setup/modification procedure for the RAN slicing instance
This part gives an overall setup/modification procedure for the RAN slicing instance which is shown in Fig. 2; in particular, the procedure involves the interaction with OAM from the operator’s perspective. Generally speaking, the procedure is triggered by NSSAI sent from 5G Core (5GC). And the gNB is responsible to produce the scheme to support the RAN slicing, with the aid of OAM-related and service-related functions specified above and configure corresponding UEs through Radio Resource Control (RRC) signaling.
Firstly, the UE interacts with 5GC to perform the selection of Access and Mobility Management Function (AMF) through Non-Access Stratum signaling (which is transparent to RAN and UE Access Stratum), determining requirements of the end-to-end network slicing based on the selected S-NSSAI, which may imply the isolation information for this slice.
Next, 5GC informs RAN to setup or modify the RAN slicing instance which is within RAN’s capability by sending NSSAI. An NSSAI may contain multiple S-NSSAIs, each of which corresponds to a specific SLA. Note that the NSSAI can be carried on different messages (which are given in Fig. 2) by listing all S-NSSAIs for each PDU session. After RAN obtains the NSSAI, the six-step procedure for the RAN slicing starts.
Figure 2: An overall setup/modification procedure for the RAN slicing instance
- Step 1: RRC sends NSSAI Request message to RRM.
After acquiring NSSAI, in order to satisfy the slice-level QoS profile, RRM generates/selects parameters, functions and algorithms which may contain:- The management parameters including UE context and slice-level QoS profile.
- The functional parameters including configured functions subject to specific RB/Logical Channel (LCH) within the slice, and the mapping between RBs and LCHs.
- The selected algorithms subject to the RAN slicing including bearer management part and resource management part, from which the bearer management part further contains algorithms for Admission Control, Bearer Control and Handover; while the resource management part further contains algorithms for Scheduling, Power Control, Interference Coordination and Load Balancing (which indicates that RRM contains both RRC-level and MAC-level controlling operations).
- Step 2: RRM sends NSSAI Response message back to RRC.
- Step 3: RRC sends OAM for RAN Slicing Request message to OAM which contains corresponding slice information.
After receiving this message, according to the operator’s strategy, OAM generates parameters and scheme for the RAN slicing which may contain:- Setting up independent strategy for tenants: OAM is able to define specific priorities for different slices for each tenant, providing customized guarantees on the air interface. In addition, OAM ensures the isolation on the equipment and the network, while trying best to provide high flexibility for the deployment of NFs. If the slice requirement matches the one in the stored slicing template, it is suggested that the stored template can be reused.
- Performing operations related to EM, NM and DM for the RAN slicing, such as providing a combinatorial set of equipments and NFs for specific types of slices.
- Step 4: OAM sends OAM for RAN Slicing Response message back to RRC. If the message indicates a failure, a cause value should also be included in the response.
(Note that, in our opinion, the RRM configuration and OAM configuration procedures are independent, which means Step 1-2 and Step 3-4 could be executed concurrently.) - Step 5: After the completion of Step 1-4, RAN is able to support the specified RAN slicing. Then RRC sends RAN Slicing Configuration message to configure L2 (SDAP/PDCP/RLC/MAC) and L1 (PHY) on the gNB side.
- Step 6: gNB sends RAN Slicing Setup/Reconfiguration message to UE, triggering the RAN slicing setup/reconfiguration procedure which requires the interaction between gNB and UE AS. During the procedure, UE achieves the configuration on parameters and functions for the protocol stack which is indicated by RRC signaling on the gNB side.
After the completion of the above 6 steps, RAN sends response back to CN, which means the successful establishment/modification of the RAN slicing instance.
5. Conclusion
The RAN slicing contains huge potential to be one of the most practical technologies in 5G NR. As a result, it is believed that work on the RAN slicing is becoming more and more valuable. This article presents opinions on functional exploration and procedural descriptions on the RAN slicing from the perspective of operators, which only makes a quick glance at current progress on the RAN slicing. With deeper investigations on related topic, there are many more standardization and algorithmic research to study on. In order to clarify the problems related to the RAN slicing, any further technical discussions from any organizations are welcomed.
References
- 3GPP TS 23.501: “System Architecture for the 5G System; Stage 2”, V15.0.0 (2017-12)
- China Mobile Communications Corporation, “Technical Vision of Slicing Packet Network (SPN) for 5G Transport”, V1.0 (2018-02)
- 3GPP TR 38.801: “Study on New Radio Access Technology; Radio Access architecture and interfaces”, V14.0.0 (2017-03)
- Kokku, R, et al. "CellSlice: Cellular wireless resource slicing for active RAN sharing." Fifth International Conference on Communication Systems and Networks IEEE, 2013:1-10.
- Foukas, Xenofon, et al. "Orion: RAN Slicing for a Flexible and Cost-Effective Multi-Service Mobile Network Architecture." The, International Conference 2017:127-140.
- Ksentini, Adlen, and N. Nikaein. "Toward Enforcing Network Slicing on RAN: Flexibility and Resources Abstraction." IEEE Communications Magazine 55.6(2017):102-108.
 Chih-Lin I received her Ph.D. degree in electrical engineering from Stanford University. She has been working at multiple world-class companies and research institutes leading the R&D, including AT&T Bell Labs; Director of AT&T HQ, Director of ITRI Taiwan, and VPGD of ASTRI Hong Kong. She received the IEEE Trans. COM Stephen Rice Best Paper Award, is a winner of the CCCP National 1000 Talent Program, and has won the 2015 Industrial Innovation Award of IEEE Communication Society for Leadership and Innovation in Next-Generation Cellular Wireless Networks.
Chih-Lin I received her Ph.D. degree in electrical engineering from Stanford University. She has been working at multiple world-class companies and research institutes leading the R&D, including AT&T Bell Labs; Director of AT&T HQ, Director of ITRI Taiwan, and VPGD of ASTRI Hong Kong. She received the IEEE Trans. COM Stephen Rice Best Paper Award, is a winner of the CCCP National 1000 Talent Program, and has won the 2015 Industrial Innovation Award of IEEE Communication Society for Leadership and Innovation in Next-Generation Cellular Wireless Networks.
In 2011, she joined China Mobile as its Chief Scientist of wireless technologies, established the Green Communications Research Center, and launched the 5G Key Technologies R&D. She is spearheading major initiatives including 5G, C-RAN, high energy efficiency system architectures, technologies and devices; and green energy. She was an Area Editor of IEEE/ACM Trans. NET, an elected Board Member of IEEE ComSoc, Chair of the ComSoc Meetings and Conferences Board, and Founding Chair of the IEEE WCNC Steering Committee.
She was a Professor at NCTU, an Adjunct Professor at NTU, and an Adjunct Professor at BUPT. She is the Chair of FuTURE 5G SG, an Executive Board Member of GreenTouch, a Network Operator Council Founding Member of ETSI NFV, a Steering Board Member and Vice Chair of WWRF, a Steering Committee member and the Publication Chair of IEEE 5G Initiative, a member of IEEE ComSoc SDB, SPC, and CSCN-SC, and a Scientific Advisory Board Member of Singapore NRF. Her current research interests center around “From Green & Soft, to Open & Smart”.
 Sun Junshuai received the M.S. degree in CST from Xidian University, Xi’an, China, in 2005. From 2005 to 2013, he worked in CATT as a TD-SCDMA/TD-LTE L2 engineer, SE, team leader and the director of high layer technology department. Since 2013, he has worked as a researcher in CMRI. He has great R&D and industry experience in both telecommunication and radio resource management, based on which he puts forward MCD (Multiple centralized and distributed) design logic of the protocol stack. His current research interests focus on the architecture and functionalities of wireless protocol stack.
Sun Junshuai received the M.S. degree in CST from Xidian University, Xi’an, China, in 2005. From 2005 to 2013, he worked in CATT as a TD-SCDMA/TD-LTE L2 engineer, SE, team leader and the director of high layer technology department. Since 2013, he has worked as a researcher in CMRI. He has great R&D and industry experience in both telecommunication and radio resource management, based on which he puts forward MCD (Multiple centralized and distributed) design logic of the protocol stack. His current research interests focus on the architecture and functionalities of wireless protocol stack.
 Xingyu Han received the Ph.D degree in electronic engineering from the department of EECS, Queen Mary University of London, UK, in 2016. Since 2017, he has been working as a researcher and project manager in Green Communication Research Center of China Mobile Research Institute, focusing on promoting the development of the protocol stack for 5G NR and beyond. He is now tracking the progress of 3GPP RAN2&3 and contributing to the related Working Groups. His current research interests include the system design of the protocol stack, the innovation of RAN architecture and the application of Wireless Big Data.
Xingyu Han received the Ph.D degree in electronic engineering from the department of EECS, Queen Mary University of London, UK, in 2016. Since 2017, he has been working as a researcher and project manager in Green Communication Research Center of China Mobile Research Institute, focusing on promoting the development of the protocol stack for 5G NR and beyond. He is now tracking the progress of 3GPP RAN2&3 and contributing to the related Working Groups. His current research interests include the system design of the protocol stack, the innovation of RAN architecture and the application of Wireless Big Data.
 Wang Yingying received the B.S. degree and M.S. degree in Communication and Information System from Xidian University, Xi’an, China, in 2007 and 2010. From 2010 to 2015, she worked in NPC and Spirent as a senior LTE L2 software engineer. Since 2015, she has worked in CMRI as a Wireless access network researcher. She has great research and industry experience in telecommunication. She focuses on the architecture and functionalities of wireless protocol stack of RAN.
Wang Yingying received the B.S. degree and M.S. degree in Communication and Information System from Xidian University, Xi’an, China, in 2007 and 2010. From 2010 to 2015, she worked in NPC and Spirent as a senior LTE L2 software engineer. Since 2015, she has worked in CMRI as a Wireless access network researcher. She has great research and industry experience in telecommunication. She focuses on the architecture and functionalities of wireless protocol stack of RAN.
 Huang Xueyan received the master degree in wireless communication from Beijing University of Posts and Telecommunications, Beijing, China, in 2015. From October 2015 to 2018, she was a protocol researcher of China Mobile Research Institute, focusing on user plane protocol stack research. She has more than one year 3GPP experience, and mainly follows RAN3 CU/DU architecture/interface and RAN2 user plane function design and optimization.
Huang Xueyan received the master degree in wireless communication from Beijing University of Posts and Telecommunications, Beijing, China, in 2015. From October 2015 to 2018, she was a protocol researcher of China Mobile Research Institute, focusing on user plane protocol stack research. She has more than one year 3GPP experience, and mainly follows RAN3 CU/DU architecture/interface and RAN2 user plane function design and optimization.
Editor: Anwer Al-Dulaimi
IEEE Future Directions Talks Future Networks
Contribute
The IEEE 5G Intiative is looking to create robust cross-society working groups to support the initiative. If you are interested in participating, please fill out the contact form below, and we will communicate your information to the appropriate working group.
- Web Portal / Content Development
- Publications
- Education
- Community Development
- Brand Development
- Technology Roadmap: Based on horizon scanning, interviews and expert knowledge, the mission of the 5G Roadmap working group is to identify short (~3 years), mid-term (~5 years) and long-term (~10 years) research, innovation and technology trends in the communications ecosystem. This will enable the development of a concrete innovation and engagement roadmap guiding the IEEE community towards maximum impact contributions across its societies, and in conjunction with its demand-side as well as the wider industry & standards ecosystem. The outcome shall be a live document with a clear set of (accountable) recommendations; the document shall be updated annually and be developed in conjunction with the other working groups.
- Standards
- Industry Engagement: Seeking engagements from industry particularly with verticals that can be enabled or improved with 5G technologies. Industry partners with a understanding of 5G infrastructure can assist in explaining the core technology but central is industry contributions to verticals that will benefit from 5G implementations.
- Conferences / Events
Join the IEEE 5G Technical Community to stay informated about the activities occurring througout the IEEE 5G Initiative.
Please fill out the following form completely to indicate interest in joining the 5G Initiative:
If you have further questions please email the 5G Initiative co-chairs Tim Lee (This email address is being protected from spambots. You need JavaScript enabled to view it.) or Gerhard Fettweis (This email address is being protected from spambots. You need JavaScript enabled to view it.) with a copy to Theresa Cavrak, IEEE staff, (This email address is being protected from spambots. You need JavaScript enabled to view it.) to join any of the following working groups:
IEEE International Network Generations Roadmap (INGR)
2023 Edition INGR Chapters and Abstracts
Full chapters of the INGR are available exclusively to signed-in participants of the IEEE Future Networks Technical Community (FNTC). Learn more and become a participant here today!
The INGR Executive Summary and Chapter Abstracts are FREE. We have published fourteen (14) free abstracts and full chapters as part of the 2023 Edition
|
|
Accessing the INGR Documents
Full chapters of the INGR are available exclusively to signed-in participants of the IEEE Future Networks Technical Community (FNTC). Learn more and become a participant here today!
The INGR Executive Summary and Chapter Abstracts are FREE.
Becoming a participant of the IEEE Future Networks Technical Community is:
- free for all IEEE society members
- $5 for IEEE student members
- $10 for IEEE members who are not members of a society, and
- $15 for non-IEEE members.
Click HERE to become a participant and unlock access to the INGR and the many benefits
of the IEEE Future Networks community. Instructions for joining the IEEE Future Networks community are available.
INGR Webinar Series Videos
The INGR working groups have presented a series of monthly webinars. Watch the videos today!
 |
|
About the IEEE International Network Generations Roadmap (INGR)The purpose of the International Network Generations Roadmap (INGR) is to stimulate an industry-wide dialogue to address the many facets and challenges of the development and deployment of 5G in a well-coordinated and comprehensive manner, while also looking beyond 5G by laying out a technology roadmap with 3-year, 5-year, and 10-year horizon. Future network technologies (5G, 6G, etc.) are expected to enable fundamentally new applications that will transform the way humanity lives, works, and engages with its environment. INGR, created by experts across industry, government and academia, is designed to help guide operators, regulators, manufacturers, researchers, and other interested parties involved in developing these new communication technology ecosystems. Each chapter is peer-reviewed by internal industry experts, then sent out for external review by subject matter experts, and finally receives an editorial review before being finalized for publication. Development of the INGR has produced a technical community that fosters the exchange of ideas, sharing of research, setting of standards, and identification, development, and maturation of system drivers, system specifications, use cases, and supported applications. As work continues, new experts are encouraged to participate, to evolve and strengthen this crucial document. Join us! Please send a message to one of the groups listed below to express your interest in participating. Be notified of new releases and all other Future Networks news by joining our technical community. |
|

Working Group Teams
| Working Group | Chairs | Email to contact to participate |
| Co-Chairs | This email address is being protected from spambots. You need JavaScript enabled to view it.This email address is being protected from spambots. You need JavaScript enabled to view it., This email address is being protected from spambots. You need JavaScript enabled to view it. (advisor) | This email address is being protected from spambots. You need JavaScript enabled to view it. |
| Applications and Services | This email address is being protected from spambots. You need JavaScript enabled to view it., This email address is being protected from spambots. You need JavaScript enabled to view it. | This email address is being protected from spambots. You need JavaScript enabled to view it. |
| Artificial Intelligence / Machine Learning | This email address is being protected from spambots. You need JavaScript enabled to view it., This email address is being protected from spambots. You need JavaScript enabled to view it., This email address is being protected from spambots. You need JavaScript enabled to view it. | This email address is being protected from spambots. You need JavaScript enabled to view it. |
| Connecting the Unconnected | Sudhir Dixit, This email address is being protected from spambots. You need JavaScript enabled to view it. | This email address is being protected from spambots. You need JavaScript enabled to view it. |
| Deployment | This email address is being protected from spambots. You need JavaScript enabled to view it.,This email address is being protected from spambots. You need JavaScript enabled to view it. | This email address is being protected from spambots. You need JavaScript enabled to view it. |
| Edge Services and Automation | This email address is being protected from spambots. You need JavaScript enabled to view it., This email address is being protected from spambots. You need JavaScript enabled to view it. | This email address is being protected from spambots. You need JavaScript enabled to view it. |
| Energy Efficiency | This email address is being protected from spambots. You need JavaScript enabled to view it.This email address is being protected from spambots. You need JavaScript enabled to view it. | This email address is being protected from spambots. You need JavaScript enabled to view it. |
| Massive MIMO | This email address is being protected from spambots. You need JavaScript enabled to view it., This email address is being protected from spambots. You need JavaScript enabled to view it., This email address is being protected from spambots. You need JavaScript enabled to view it. | This email address is being protected from spambots. You need JavaScript enabled to view it. |
| Millimeter Wave and Signal Processing | This email address is being protected from spambots. You need JavaScript enabled to view it., This email address is being protected from spambots. You need JavaScript enabled to view it. | This email address is being protected from spambots. You need JavaScript enabled to view it. |
| Optics | This email address is being protected from spambots. You need JavaScript enabled to view it., This email address is being protected from spambots. You need JavaScript enabled to view it. | This email address is being protected from spambots. You need JavaScript enabled to view it. |
| Quantum Information Technology | This email address is being protected from spambots. You need JavaScript enabled to view it. | This email address is being protected from spambots. You need JavaScript enabled to view it. |
| Satellite | This email address is being protected from spambots. You need JavaScript enabled to view it., This email address is being protected from spambots. You need JavaScript enabled to view it. | This email address is being protected from spambots. You need JavaScript enabled to view it. |
| Security and Privacy | This email address is being protected from spambots. You need JavaScript enabled to view it., This email address is being protected from spambots. You need JavaScript enabled to view it. | This email address is being protected from spambots. You need JavaScript enabled to view it. |
| Standardization Building Blocks | This email address is being protected from spambots. You need JavaScript enabled to view it., This email address is being protected from spambots. You need JavaScript enabled to view it., This email address is being protected from spambots. You need JavaScript enabled to view it. |
This email address is being protected from spambots. You need JavaScript enabled to view it. |
| Systems Optimization | Dilip Krishnaswamy, This email address is being protected from spambots. You need JavaScript enabled to view it., This email address is being protected from spambots. You need JavaScript enabled to view it., This email address is being protected from spambots. You need JavaScript enabled to view it. | This email address is being protected from spambots. You need JavaScript enabled to view it. |
| Testbed | This email address is being protected from spambots. You need JavaScript enabled to view it., This email address is being protected from spambots. You need JavaScript enabled to view it. | This email address is being protected from spambots. You need JavaScript enabled to view it. |
Industry
 The IEEE Future Networks Technical Community a new service to engage the broad array of companies working in the 5G and future networks space. Volunteers in our technical community recognized a need to fill in the space of collaborative innovation for 5G and 6G networks and to facilitate the transition of ideas into real technologies that improve human connectivity.
The IEEE Future Networks Technical Community a new service to engage the broad array of companies working in the 5G and future networks space. Volunteers in our technical community recognized a need to fill in the space of collaborative innovation for 5G and 6G networks and to facilitate the transition of ideas into real technologies that improve human connectivity.
Understanding that the industry and research communities thrive best in a neutral environment not bound by geography, proprietary technologies, or testing scope, IEEE created the 5G/6G Innovation Testbed to foster collaborative experimentation and advancement among stakeholders in the 5G and 6G ecosystem. These stakeholders, including telecommunications operators, equipment vendors, and application developers, rely on each other to deliver exceptional products and services across an ever-evolving network, and that interdependence requires significant testing for conformity and interoperability.
 The IEEE 5G/6G Innovation Testbed is intended to expedite the process of industry innovation by providing an efficient, low-cost collaborative testing and development environment that helps industry work together to get products and services to market faster.
The IEEE 5G/6G Innovation Testbed is intended to expedite the process of industry innovation by providing an efficient, low-cost collaborative testing and development environment that helps industry work together to get products and services to market faster.
- Virtual, end-to-end 5G network testing and innovation platform in the cloud
- Accelerate technical innovation across the interdependent industry adopters of 5G (operators, vendors, and application developers)
- Speed up innovation/development and improve ROI
- Use cases: Interoperability and conformance testing, load testing, sandbox innovation, proof of concepts, security tests, and more
- Enables both independent and collaborative testing and experimentation
- Able to connect to physical hardware
- Leverages IEEE’s technical reputation and independent/neutral position
For more information or to schedule a call to discuss setting up an account, visit the 5G/6G Innovation Testbed website.
-Anwer Al-Dulaimi,IEEE 5G/6G Innovation Testbed Chair
-Ashutosh Dutta,IEEE 5G/6G Innovation Testbed Co-Chair